Radio-frequency identification
Introduction
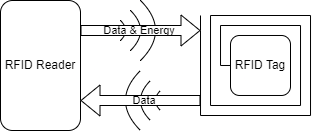
Radio-frequency identification (RFID) is a communication technology, that uses electromagnetic waves to identify and track tags. A RFID system consists out of a tag, which is attached to an object, an reader, which extracts the information of the tag and an application, that uses the gathered information.
RFID-System
Reader
A reader is responsible for initiating the communication with a tag, in case of a passive tag the reader also supplies the energy needed to operate the tag.
A reader consists out of to components:
- A control unit
- A high-frequency interface
Control Unit
The control unit is responsible for
- Communication with the application
- Communication with the tag
- Coding and decoding of the signal
- Anti-collision algorithm
- Encryption and decryption of data sent between reader and tag
- Authentication between reader and tag
High-frequency interface
The high-frequency interface is responsible for
- Generation of strong high-frequency signals to activate the tag and supply it with energy
- Modulating the transmission signal to send data to the tag
- Receiving the radio frequency signals transmitted by a tag and converting them back into original data
Tag
RFID tags are divided into six categories by EPC Global[1]. A tag in one category has all the capabilities of the subordinate categories. This means that tags are backward compatible
Passive tags, which have no built-in energy source and draw their energy from the reader's radio waves, are assigned to classes 0 to 3. Active tags, with their own energy source, are assigned to class 4. Class 5 is reserved for tag readers and active tags that can read other tags.
- class 0: These tags are passive and work with UHF. These tags are pre-programmed in the manufacturer's factory and can no longer be reprogrammed, the information can no longer be changed.
- Class 1:Class 1 tags use HF radio waves. In contrast to class 0 tags, class 1 tags and higher can be programmed by the user. However, in class 1, tags can only be described once.
- Class 2: Unlike class 1, class 2 tags can be written to multiple times.
- Class 3: Read-write with integrated sensors that are able to detect parameters such as temperature, pressure and movement; can be semi-passive or active. Semi-passive means that they occupy an energy source but cannot initiate communication with other tags or readers.
- Class 4: Class 4 tags have their own energy source and can initiate communication with other tags or readers, so they are active tags.
- Class 5: Class 5 tags are the most advanced, they can transfer energy to passive tags and communicate with readers and tags of any class, so they can also be classified as readers.
Tag information
Four types of information can be stored on a transponder:
- Information to identify the tagged item: This category includes the identification data used to uniquely identify the tagged item. This includes user-defined fields such as bank accounts, product barcodes and prices, as well as predefined registers such as the Application Family Identifier (AFI) and the Data Storage Format Identifier (DSFID)
- Supplementary information on the object: Supplementary data includes further standard information such as Application Identifiers (AIs) and ANSI MH-10 Data Identifiers (DIs), which enable further differentiation and specific information on the tagged item
- Control data: Control data could include information about the configuration of the tag, such as the settings for the security controls, including mechanisms that restrict reads or writes to user memory blocks and special registers that contain the AFI and DSFID values
- Manufacturer data: The unique identifier (UID), transponder type, manufacturer and manufacturing data can be stored in this category. This information can be specific to each manufacturer and transponder type.
The first two categories, identification and supplementary information, are present on all tags as they provide essential information for identifying and supplementing the tagged item. Categories three and four, control data and manufacturer data, can vary depending on the manufacturer and contain specific information for configuring the tag and identifying the manufacturer.
RFID Attacks
In contrast to attackers on the Internet, who can always attack a machine on the Internet, a server is always online and responds to requests from all over the world, an attacker of an RFID system does not have constant access. He must be physically close to the tag that is to be read. Or must be present during a transaction. Security models must be adapted to these facts. Further more, cheap RFID tags cannot perform standard encryption.
The challenge is therefore to create a realistic security model that reflects the threats and capabilities of reality as accurately as possible.
Cloning
There are two different types of cloning used to attack.
- Simple RFID cloning: If an attacker gains physical access to an RFID tag, they can clone it. The advantage of cloning is that, unlike theft, the original tag does not have to be kept by the attacker. Since the owner can easily become aware that the original tag is missing in the event of theft, no changes are made to the tag during cloning. The cloned tag has the same access options as the original. This makes it much less likely that the victim will know that they have been victimized. Disadvantage, needs physical access to the card/tag, must copy it and then return it. There are various devices for copying the card.
- Distance RFID cloning: There are a large number of devices that can read and clone RFID tags at a distance. The range is limited to less than 1 meter, and the greater the range, the more expensive the devices become. There are devices that can store the read data on an SD card.
Man-in-the-middle attacks
For this attacks, the hacker positions himself between the RFID tag and the reader in order to influence or eavesdrop on the communication. We distinguish between the following attacks.
- Eavesdropping: An attacker can use devices or apps to intercept the communication between the RFID tag and the reader in order to capture the transmitted data.
- Replay attacks: In this attack, the attacker is in the vicinity of a communication between the RFID/NFC tag and a reader. The communication is recorded and can be replayed at a later time to the reader.
- Relay attack: In a relay attack, the communication between the RFID tag and reader is recorded and sent to a third device.
Data manipulation
An attacker who has access to an RFID/NFC device manipulates it so that false data or requests are sent.
Skimming
Skimming is the use of unauthorized readers to retrieve data from RFID tags or to start a transaction, for example with a mobile wallet.
Spoofing
The attacker creates fake RFID tags or readers to fool the system and gain unauthorized access.
Denial of Service (DoS)
These attacks aim to overload RFID systems and disrupt their function in order to prevent authorized access.
Side channel attacks
This involves analyzing the physical properties of the RFID system, such as power consumption or electromagnetic emissions, in order to derive confidential information.
Cryptanalytical attacks
These attacks aim to break the cryptographic mechanisms used to protect the data in RFID systems.
Physical attacks
These include methods such as physically destroying RFID tags or changing their internal structures in order to disrupt their function or obtain information.
Phone malware
A vulnerability was found in Android devices in 2019. Using NFC, it was possible to download software that is not offered in the Google Play Store. Normally, the smartphone warns in such a case. The download triggered by this vulnerability did not trigger these warnings, but the user still had to confirm the download. This vulnerability has now been closed.[2]
Physical shielding of the tag
To circumvent Electronic Article Surveillance (EAS), thieves use multi-layered aluminium pockets, creating a Faraday cage, to shield the tag from the reader.
Social Engineering
Social engineering is not a direct attack, but social engineering can be used to gain access to NFC or RFID devices, which makes it possible to clone them or steal information.
Tools
There are a lot of different tools to attack RFID-Systems. Well known tools are: