VirtualBox: How to set up a Basic Pentesting Lab
Introduction
Training penetration testing typically occurs in a dedicated environment known as a pentesting lab, which is isolated from regular user applications and operating systems for security and convenience reasons. A pentesting lab can vary in complexity, with a minimalist setup involving a single computer running multiple virtual machines (VMs), often referred to as a virtual or basic pentesting lab. This variant uses virtualization software like VMware or VirtualBox to create an attacker VM with a specialized OS, such as Kali, Parrot or Arch, and allows for the addition of target machines. These machines are then consolidated in a virtual network. Users can log into the attacker machine to begin testing. More advanced labs may incorporate real hardware, such as real computers, routers, and firewalls, but this increases costs and electricity usage. However, these sophisticated environments enable more realistic scenarios and complex tasks.
This page explains how a basic pentesting lab that can be set up with VirtualBox. This environment will suffice for most people who want to try out or train pentesting and hacking at home. The system will consist of a base machine at performs the actual operations (the attacker machine) and arbitrary target machines, the user can add and remove at will.
The software used in this tutorial:
- Windows 10 or 11 (as the Host OS)
- VirtualBox
- Kali Linux
Setup Steps
Installation
Download and install VirutalBox on your Windows machine. There is no need to manually configure anything in this installation process, you can just leave everything at default.
On the Kali Linux download-page, make sure you go to "Pre-built Virtual Machines" and select the VirtualBox option. Using a pre-built image will make the OS setup much easier than with traditional ISO-files. This download might take a while.
Attacker Setup
Downloading the Kali pre-built VM will get you a .ZIP-folder. Extract it to a directory of your choice. Inside you should find a .VBOX-file. Double-click it and the VM will be automatically imported to the VirtulBox Manager.
This machine can now be used out-of-the-box. The login credentials are "kali" and "kali". This is OK because, this is just a training environment. The password does not need to be strong or protected.
If the machine automatically boots up when imported, you can shut it down again. Do this by clicking "File" in the top bar of the machine window. Then "Close" and "Power off the machine" -> OK. Alternatively, you can login and shut it down from there normally.
Now you should have the Kali VM in your list, looking something like this:
Network Configuration
The goal is to create a testing network that is separated from the host OS. The easiest way to do this is by creating a virtual network that only contains the attacker and target machines. This can be achieved by setting up a DHCP-service within VirtualBox, that automatically assigns IP-addresses to the VMs when booted up.
Open the windows command prompt and navigate to the VirtualBox installation directory. By default, this is C:\Program Files\Oracle\VirtualBox. Now use the vboxmanage tool to create the DHCP server:
vboxmanage dhcpserver add --network=vnet --server-ip=172.16.0.1 --lower-ip=172.16.0.2 --upper-id=172.16.0.100 --netmask=255.255.255.0 --enableYou can also choose other settings for your network, but make sure to use private IP addresses. If you don´t know what values to pick, you can just copy this command.
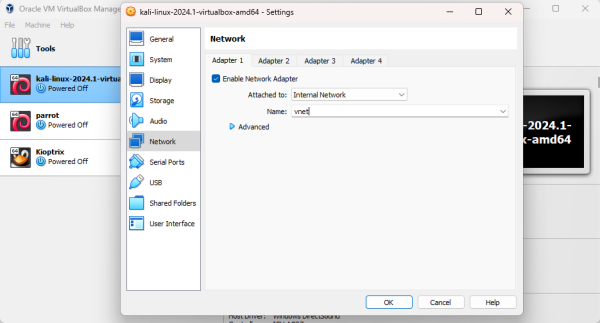
For every machine you want to add to the pentesting network, go into the settings for the VM and go to Network. Enable one adapter and set it as attached to Internal Network. Below, enter the same name that was used in the vboxmanage-command (vnet in this example).
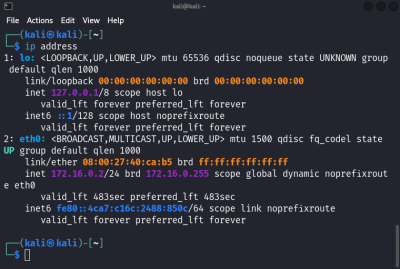
At the end, you can start the machine and verify the network configuration. If the machine has an IP from the defined pool, the DHCP service works correctly.
Add Target Machines
Now your virtual pentesting lab is ready. You can add vulnerable target machines that you can hack from your Kali-Base-VM. A great source for such VMs is VulnHub.com. This site offers a vast collection of virtual machines that are intentionally vulnerably. You can legally hack and break them inside your environment.
However, always make sure to add your machine to the testing network, like we did with the attacker machine.
Once a target is added you can use nmap, fping, ping, netdiscover or some other tool to find it on the network. Now you can start hacking and exploring the machine for weaknesses.
Optional: Host-to-VM Connection
With the current network configuration there is no connection between the physical host machine, that is running the VMs, and the attacker machine. Therefore, the attacker also has no internet connection.
This is not necessary for such an environment. But if you want this, you can enable a second adapter in the VM settings and set it to NAT. This way the VM will have host and internet connectivity. But this goes only in one direction, the host or the internet cannot reach the VM.
If you want the connection to go bidirectional, set the adapter to Bridged Adapter.