Difference between revisions of "BLE-Berry Project"
| Line 16: | Line 16: | ||
The STRIDE method was used to categorize the discovered Threats, as shown in the following table. | The STRIDE method was used to categorize the discovered Threats, as shown in the following table. | ||
[[File:BLE Berry Project | [[File:BLE Berry Project STRIDE2.png|800px]] | ||
=== Step 1 === | === Step 1 === | ||
Revision as of 18:56, 2 October 2023
Summary
This Project is the result of a master’s thesis that created a Threat Model of the Bluetooth Low Energy (BLE) Standard and developing a tool called BLE Berry to enable easier BLE Development and to perform basic pentesting operations.
Threat Model
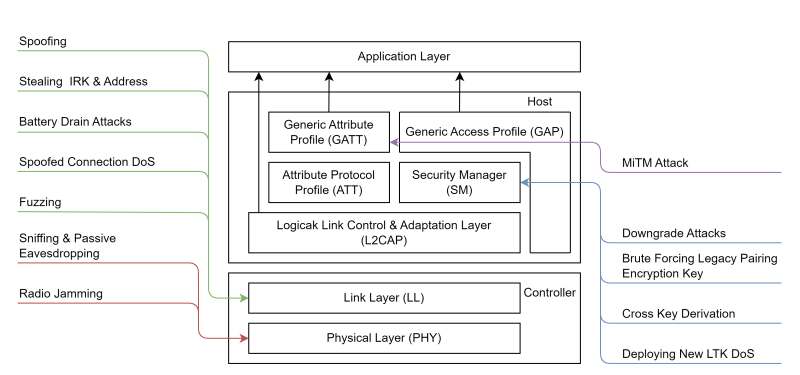
The Threat Model was performed by analyzing the BLE portion of the BLE Standard and gathering further information's from numerous white papers and scientific papers. The gathered Threats and Vulnerabilities got mapped to the Layer/Protocol they are performed on, as shown in the figure below.
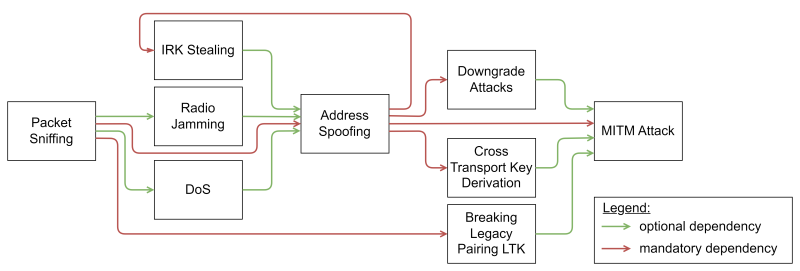
Some of the Threats have use other Threats as an entry vector, e.g., a machine-in-the-middle attack relies on address spoofing and can benefit from Radio Jamming. The dependencies of the Threat is shown in the figure below.
The STRIDE method was used to categorize the discovered Threats, as shown in the following table.
File:BLE Berry Project STRIDE2.png
Step 1
Step 1.2
Enter these commands in the shell
echo foo echo bar
Step 2
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)