BLE-Berry Project
Summary
This Project is the result of a master’s thesis that created a Threat Model of the Bluetooth Low Energy (BLE) Standard and developing a tool called BLE Berry to enable easier BLE Development and to perform basic pentesting operations.
Threat Model
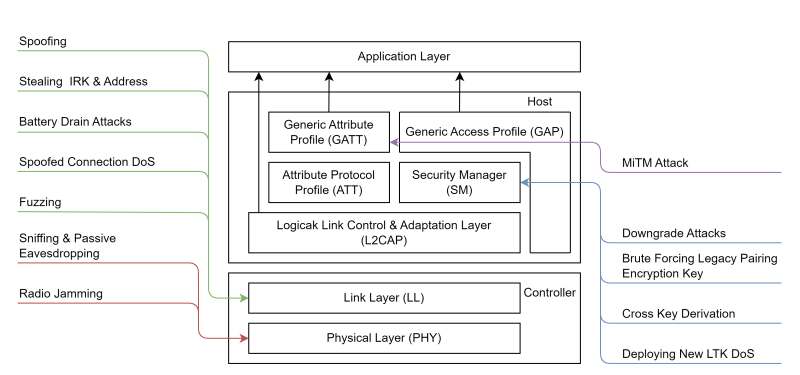
The Threat Model was performed by analyzing the BLE portion of the BLE Standard and gathering further information's from numerous white papers and scientific papers. The gathered Threats and Vulnerabilities got mapped to the Layer/Protocol they are performed on, as shown in the figure below.
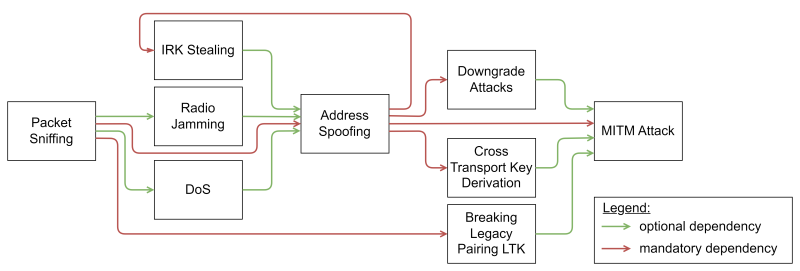
Some of the Threats have use other Threats as an entry vector, e.g., a machine-in-the-middle attack relies on address spoofing and can benefit from Radio Jamming. The dependencies of the Threat is shown in the figure below.
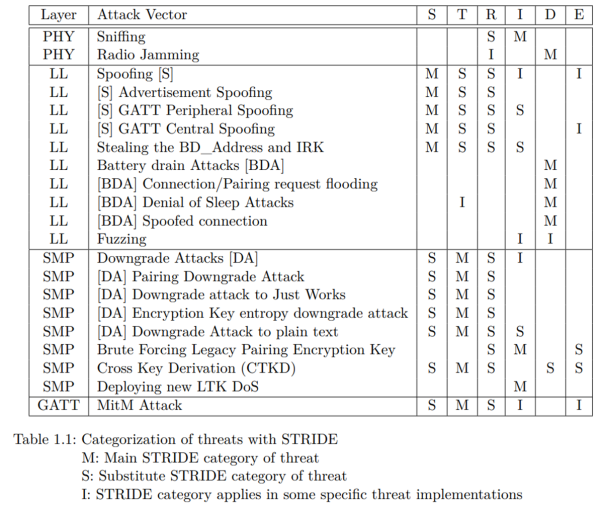
The STRIDE method was used to categorize the discovered Threats, as shown in the following table. STRIDE separates the Threats in the following six categories:
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial of Service
- Elevation of Privilege
Threat Vectors
Sniffing / Eavesdropping
Sniffing or eavesdropping is performed with BLE by scanning the Radio for messages. This results in an information disclosure, but can be countered if encryption is used to provide confidentiality. The BLE standard itself provides AES-CCM encryption with message authentication by a key created with the usage of P256 ECDH. The commercial market provides some affordable USB Sniffing Accessories, which output pacap files that can be analyzed with wireshark:
Radio Jamming
Radio jamming aims to perform a Denial of Service (DoS) by disrupting sent data with interfering signals. Radio jamming can be performed on all channels at the same time (called full band jamming) or selective on a single channel. Furthermore, can be differentiated into persistent and reactive jamming. Persistent full band jamming can be detected easily because it interferes with all sent messages. Selective reactive jamming on the other hand is hard to detect because it only jams specific messages.
Spoofing
Spoofing is the process of changing the Bluetooth address to another one to impersonate the other device. BLE Spoofing cannot be prevented and is one of the biggest vulnerability of the communication protocol. Furthermore, many BLE chip manufacturer provide the functionality to change the address with manufacturer specific host controller interface (HCI) commands, which is abused for spoofing.
IRK Stealing
The BLE provides a function to hide the address of and device by using private address. This security feature aims to prevent tracking of devices because they change their address periodically. The devices still can establish a connection by resolving the private address by calculating a hash with the usage of the Identity Resolving Key. This key gets distributed after a legit connection establishment. Therefore, can an adversary spoof another device and tell the target that it lost the long term key and initiate a new pairing process and gathers the IRK.
Battery Draining Attacks
Battery drain attacks aim to preform a Denial of Service by draining the devices' battery. This can be either achieved by flooding a device by many pairing request that then don't get performed, or by connecting to the device and using its services and denying it to sleep. Many devices achieve a long battery life by using log deep sleep phases and short wake up times, which is prevented by an adversary in this case.
DoS due to Spoofed Connection
Older versions of BLE only allowed a peripheral device to only serve one connection at a time. This can be used by an adversary to prevent the legit central device from discovering the peripheral by connecting it and keeping the connection open. This restriction was lifted, but the ability to serve multiple connections must be configured by the device manufacturer and therefore is not used by most devices.
Fuzzing
Fuzzing is the act of sending arbitrary data or message with mutated lengths of fields. This can cause device failures and deadlocks.
Downgrade Attacks
Downgrade attacks downgrade either the used paring algorithm or the key size of the encryption key. This attack require a machine in the middle attack during the connection establishment and altering the input output capabilities, secure connections or key size field in connection request.
Bruteforcing Legacy Pairing Encryption Key
DoS due to Key replacement
Machine in the Middle
Step 2
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)