Difference between revisions of "BeEF"
(→Result) |
|||
| (19 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Summary == | == Summary == | ||
'''Browser Exploitation Framework (BeEF)''' allows | '''Browser Exploitation Framework (BeEF)''' is a free and open-source Framework, that allows user to start client-side-attacks against Browsers, assess | ||
* the security of the browser and | |||
* the possible effects on the network to be tested. | |||
It is pre-installed in Kali Linux. Run BeEF under '''Applications -> System Services''', with a click on '''beef start''' a terminal window will open to start the service. | |||
== Requirements == | == Requirements == | ||
| Line 9: | Line 14: | ||
== Example == | == Example == | ||
Below we have an example of how to start a client-side attack | Below we have an example of how to start the BeEF service, and execute a "'''Google Phishing'''" client-side attack. With this example we'll see how to gather credential information of victim. | ||
[[File:login.jpg|150px|thumb|Example|left|Login to BeEF service]] | [[File:login.jpg|150px|thumb|Example|left|Login to BeEF service]] | ||
| Line 27: | Line 31: | ||
[[File:localhost.jpg|150px|thumb|Example|left|localhost]] | [[File:localhost.jpg|150px|thumb|Example|left|localhost]] | ||
<br> | |||
=== Hook Target Browser === | === Hook Target Browser === | ||
| Line 61: | Line 67: | ||
[[File:googlephishing_pw.png|150px|thumb|Example|left|result]] | |||
<br> | |||
=== Result === | === Result === | ||
| Line 73: | Line 76: | ||
<br> | <br> | ||
<br> | <br> | ||
Latest revision as of 03:12, 11 July 2021
Summary
Browser Exploitation Framework (BeEF) is a free and open-source Framework, that allows user to start client-side-attacks against Browsers, assess
- the security of the browser and
- the possible effects on the network to be tested.
It is pre-installed in Kali Linux. Run BeEF under Applications -> System Services, with a click on beef start a terminal window will open to start the service.
Requirements
As part of this guide, I used Kali (Kali GNU/Linux Rolling 5.10.0-kali3-amd64) as the OS, so it was already preinstalled. I installed Kali on a Virtual machine (VMware® Workstation 15 Pro 15.5.5 build-16285975).
Example
Below we have an example of how to start the BeEF service, and execute a "Google Phishing" client-side attack. With this example we'll see how to gather credential information of victim.
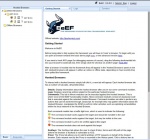
Start: Open the BeEF service and authenticate
After the beef service has started, you have to log into the service. Default credentials are 'beef' for username and 'beef' for the password.
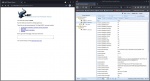
Hook Target Browser
For practicing purposes BeEF provides a localhost webpage.
To see the details of hooked Browser
If you click on the hooked browser, under "Details" you can see information about the browser.
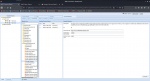
Command execution in the Browser
There are hundreds of modules under "Commands", which include from social engineering to browser hacks. The desired module can be selected by clicking and executed with the "Execute" button at the bottom right. I choosed the "Google Phishing" module under the "Social Engineering" Folder and clicked to "Execute".
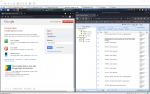
Result
After executing the "Google Phishing" module, the victim is asked to "Sign in". Victims entered credentials are visible under "Logs".
Courses
- WFP-1