Bluetooth Pentesting Tools (HW/SW)
Summary
This article describes various tools for bluetooth penetration testing and aims to provide an overview to choose the right tool for a use case.
Requirements
- Operating system: Kali Linux amd64 2019.2
- Packages: Individual shown for each tool
In order to use hardware pentesting devices a dedicated installation of kali linux is recommended but it is also possible to use hypervisors which are capable of passing USB devices from the host- to the guestsystem e.g. VMWare Workstation or the free hypervisor VirtualBox.
Information gathering
The offical linux bluetooth protocol stack BlueZ is already installed on kali linux but can be installed on other linux maschines with:
apt install -y bluez bluez-utils systemctl start bluetooth.service systemctl status bluetooth.service
hcitool
To start with penetration testing we need to gather information about our environment, for this purpose scan for available bluetooth devices with the included packages 'hcitool' or 'bluetoothctl'.
First check if your bluetooth device is available:
hciconfig
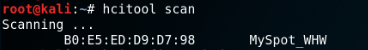
Scan for BR/EDR Bluetooth devices with hcitool:
hcitool scan
In order to scan for BLE devices use:
hcitool lescan
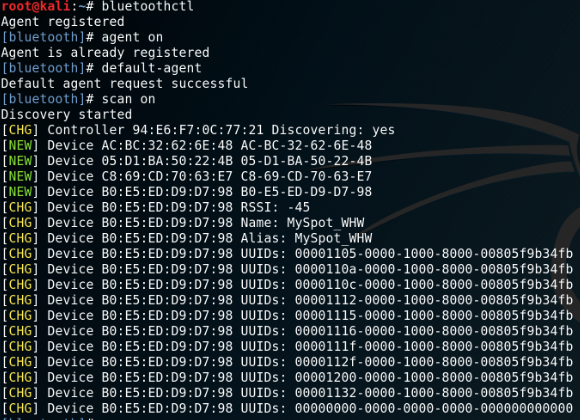
bluetoothctl
Alternatively you can use bluetoothctl which is also included in the bluez-utils package:
bettercap
This Software is described in the Bettercap Documentation.
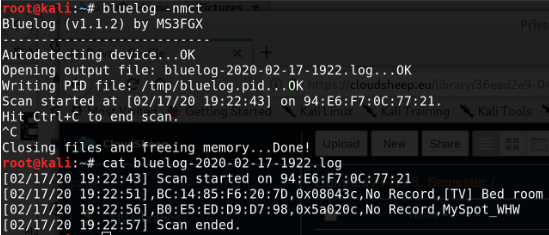
bluelog
Another great tool for bluetooth device discovery is 'bluelog'. It is extremly lightweight and can be automated for background usage without user intervention. Bluelog is already preinstalled on kali linux but can be installed with:
apt install -y bluelog
To start scanning for bluetooth devices use:
bluelog -nmtc
(n=log device names;m=log manufacturer;t=log timestamps of discovery;c=log device class)
Capturing bluetooth traffic
btmon
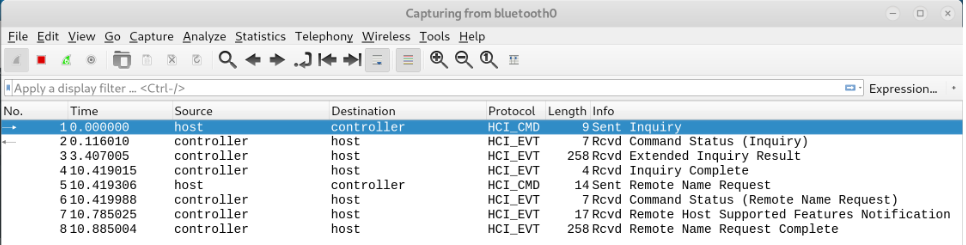
With the preinstalled package 'btmon' it is possible to capture traffic between the HCI and the controller:
btmon --write ~/Documents/bttraffic.snoop
These files can be viewed and analysed with 'Wireshark' which is also preinstalled on kali linux.
Wireshark
Alternatively you can capture bluetooth traffic directly with Wireshark. Start Wireshark with...
wireshark -w ~/Documents/bttraffic.snoop
...and select your bluetooth interface e.g. bluetooth0 or bluetooth1.
Bluetooth Pentesting Software
In the following chapter we will present some software pentesting tools which are used for ethical bluetooth device hacking.
BlueMaho
BlueMaho is a tool suite for bluetooth device pentesting and provides various exploits. It is written in python and uses wxPython. The feature set includes: scanning, tracking, alerts on new devices or targeted devices, sending files or changing BT values like the BD_ADDR.
Although it is still listed in the kali linux tool list, it has to be manually installed:
apt install autoconf build-essential build-dep git python-wxtools git clone https://github.com/zenware/bluemaho cd bluemaho/config ./build.sh
In order to run the GUI use:
./bluemaho.py
GATT Tool
Before you can start using the GATT Tool you need to know the Bluetooth Address of the victim device. For gathering this information you can use the hcitool, which is described above.
The GATT Tool has a powerful interactive mode. During this mode the devices stay connected and you can use more than one handle sequentially.
sudo gatttool -I <Bluetooth interface> -b <BD_ADDR> connect
To get the name of your Bluetooth interfaces use hciconfig, which is described above.
The Interactive mode also allows to list the characteristics of the connected device and control them.
characteristics
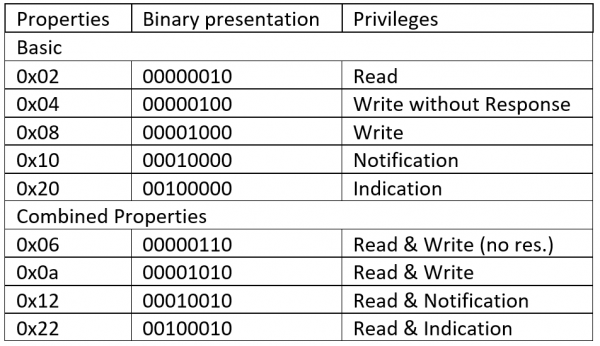
Depending on the Privileges you can Read, Write characteristics of the device.
Read: char-read-hnd <handle> Write: char-write-req <handle> <write value> or char-write-cmd <handle> <write value>
The Privileges are described in the following graph
An example of an guided exploit can be found at the Mipow Playbulb: Bluetooth Connection Sniffing documentation
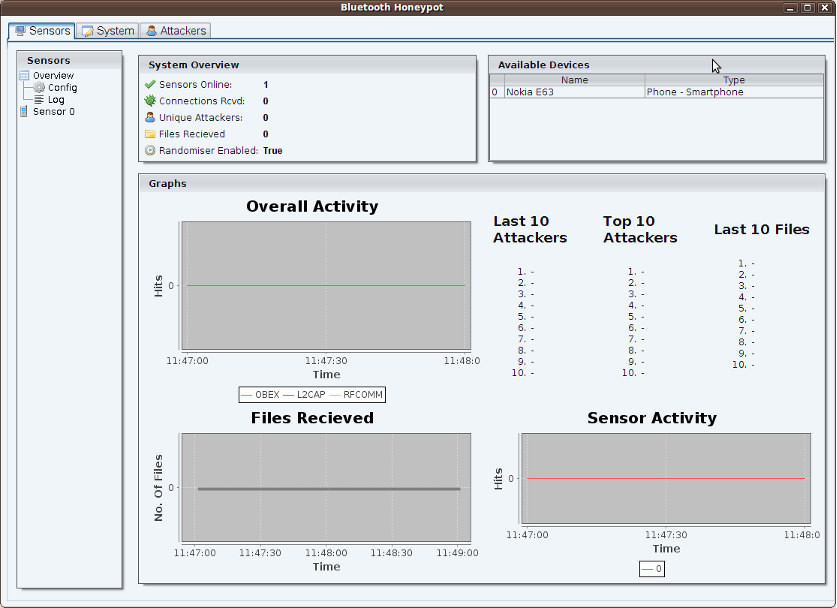
Bluepot
Bluepot is a Bluetooth Honeypot written in Java, it is designed to accept and store any malware sent to it and interact with common Bluetooth attacks. The system also allows monitoring of attacks via a graphical user interface that provides graphs, lists, a dashboard and further detailed analysis from log files.
In order to install bluepot use following commands:
wget https://github.com/andrewmichaelsmith/bluepot/raw/master/bin/bluepot-0.1.tar.gz tar xfz bluepot-0.1.tar.gz java -jar bluepot/BluePot-0.1.jar
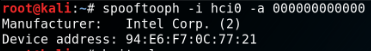
spooftooph
Spooftooph is designed to automate spoofing or cloning Bluetooth device information. The software is able to clone and log bluetooth devices, generate or change new random bluetooth profiles and specify device information for bluetooth interfaces.
E.g.: Spoof your own device address for the interface hci0:
Bluetooth Pentesting Hardware
For hardware pentesting devices like the Ubertooth one please see following documentations: