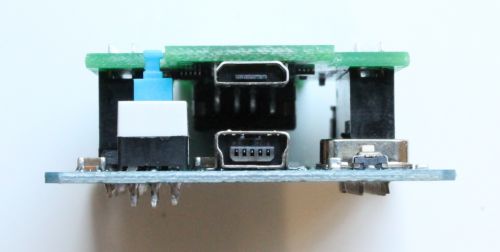
BugBlat EzSniffer USB Protocol Analyzer
Summary
The BugBlat EzSniffer USB Protocol Analyzer is as easy to use, small form factor USB Protocol Analyzer. It uses USB 2.0 technology with micro-B, mini-B and USB-A type ports. It can capture up to 256 MB of traffic at a time. The companion application is easy to use, easy to set up and provides additional information concerning the captured packets. The EzSniffer is best suited to capture regular data transfers (e.g., thumbdrives or other external drives) but cannot capture data from input devices like an USB mouse.
Requirements
Analysis host
- USB Type A socket
- USB Type A to USB mini-B cable (included in EzSniffer plus EZ-USB Package)
Sniffed USB Connection
- Type A to Type micro-B cable to connect to a host device that receives the packets
- Type A to Type A cable to connect to a target device that sends the packets
Software
- EzSniff application available for Linux/Windows
- Additional driver necessary for Windows
- Download the driver
- Plug in the EzSniffer
- Run the Zadig executable
- Choose Cypress FX2LP from the device list (if not shown tick List All Devices in Options) (remark: upon testing unknown device #1 showed instead but it worked regardless)
- Select the WinUSB driver
- Click Replace Driver
Description
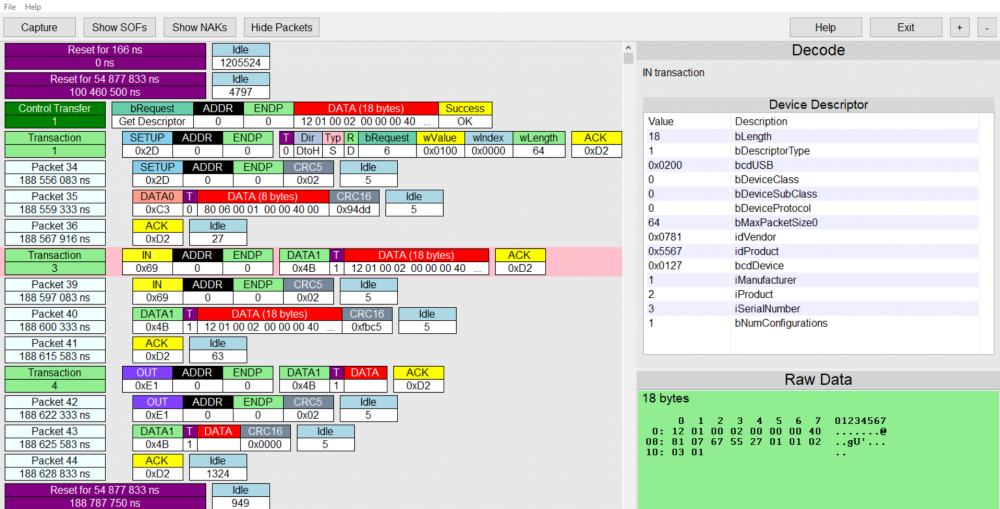
After installing the EzSniff application, make sure to that the analysis computer is connected to the USB Port located on the blue Microcontroller Board (EZ-USB FX2LP) and that the blue switch is in the On-position, i.e. pressed down. Start the application and you will see a default screen where you can see example packets that you can click on to receive additional information in the decode screen on the top right. On the bottom right you can see the raw data displayed.
Before trying to capture anything, you should connect a host machine to the host port on the green EzSniffer board and a USB device to the device side of the board. To start capturing simply click on Capture and the capture window will open. Here you can control the connection between host and device and you can set the buffer size for the capture. You can establish and sever the connection between device and host by clicking the respective buttons. Upon starting the capture the device automatically connects. This can be handy to capture a newly forming USB connection. Note that the EzSniffer will capture only data up to the set buffer value. This value can be up to 256 MB and it is set to a default of 32 KB. For our first test we will set this buffer to 4MB and we will try to transmit a .docx file to a regular USB Thumbdrive.
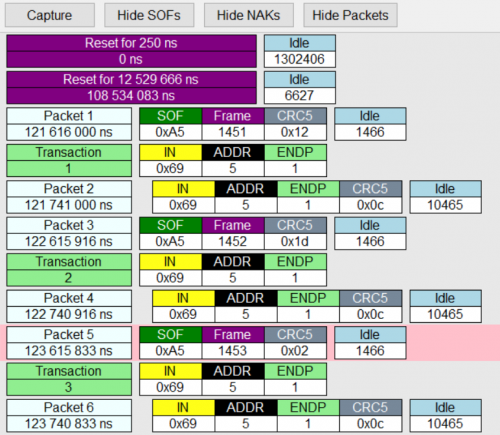
As can be seen the first messages shows the reset that is done by the application before starting the connection. The first packet is a SOF (Start of Frame) packet that denotes the start of a frame and contains a frame number that is incremented. These packets can be hidden by clicking on Hide SOFs since they don’t give us much information. All packets that can be seen above are IN-packets that signal to the USB thumbdrive that the host whishes to read information. It is also possible to hide NAKs, which are signals that the device temporarily can’t receive data and you can also hide the packets itself. When hiding packets you get a view that only shows you transactions that subsume the actual packets. Scrolling further down we find the actual data transfer.
Below a early part of the data transfer can be seen. The first transaction is a control transfer that uses SETUP-packets which are used to configure the way the device transfers data. These messages are needed less in the latter parts of the transaction. You can also see an OUT-packet where the device informs the host that it wants to send data and etween those the data packets (333, 336, 339) can be seen. Every transaction is ended with an ACK-packet.
A second test using a standard USB mouse was unfortunately inconclusive. The EzSniffer could not capture any actual packets and showed only reset messages. If you need to capture packets other than datapackets you should try the Beagle USB 12 Protocol Analyzer.
Used Hardware
- BugBlat EzSniffer USB Protocol Analyzer
- Kingston DT50 16GB USB 3.0 Thumbdrive
- Logitech M100 mouse
- 2 Windows 10 PCs