Difference between revisions of "Clipper Chip"
| (13 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
= Summary = | = Summary = | ||
This document shows an overview about the Clipper Chip | This document shows an overview about the Clipper Chip, which was part of the capstone program. The chip was introduced by the U.S. Government in 1993. Its use was abandoned in 1996 and its algorithm has been declassified in 1998. | ||
= Description = | = Description = | ||
| Line 7: | Line 7: | ||
The Clipper Chip is a small Chipset, that was developed by the NSA (National Security Agency) and advertised by the U.S. Government, in the early 90´s. | The Clipper Chip is a small Chipset, that was developed by the NSA (National Security Agency) and advertised by the U.S. Government, in the early 90´s. | ||
The idea was, that the Chipset would be integrated in Communication devices like telephones or personal computers and to securely encrypt their Communication, while | The idea was, that the Chipset would be integrated in Communication devices like telephones or personal computers and to securely encrypt their Communication, while giving the U.S. Government the possibility to decrypt the communication. This was done by the use of a Key Escrow Algorithm. | ||
=Origin= | =Origin= | ||
According to official U.S. Government Documents, the origins of the Clipper Chip | According to official U.S. Government Documents, the origins of the Clipper Chip program, can be traced to the [https://en.wikipedia.org/wiki/Computer_Security_Act_of_1987 "Computer Security act of 1987"]. This Act was meant to ammend legislation of the Year 1949, to create security standards for non-military computer systems. | ||
in 1993 The U.S. Government introduced an initiative, that should provide security for communication of non-classified data with a special Chipset, called the Clipper Chip. | in 1993 The U.S. Government introduced an initiative, that should provide security for communication of non-classified data with a special Chipset, called the Clipper Chip. | ||
The goal was to at first equip the DoJ (Department of Justice) with phones containing the Clipper Chip and then extend its use to the US high-tech industry. | The goal was to at first equip the DoJ (Department of Justice) with phones containing the Clipper Chip and then extend its use to the US high-tech industry. | ||
=Functionality= | =Functionality= | ||
For the encryption of the communication the Clipper Chip uses the Skipjack-algorithm. For the key escrow, the Escrowed Encryption Standard was used. | |||
==Skipjack Algorithm== | |||
The Skipjack algorithm is a blockcipher with a blocksize of 64 bit. The key length was 80 bit. It supported modes of operation are Output Feedback Mode(OFB), Cipher Feedback Mode(CFB), Electronic Code Book(ECB) and Cipher Block Chaining(CBC). The key exchange was done with a Diffi Hellmann algorithm. | |||
It was developed by the NSA and declared secret. This prohibited civilian experts from analysing the algorithm. | |||
Skipjack should replace the DES algorithm that was the standard at the time and was considered not to be secure anymore. | |||
==Escrowed Encryption Standard== | |||
The most important feature of the Clipper Chip was the possibility to retrieve the session key. This should allow law enforcement agencies to encrypt communication that was obtained for example via wiretaping. | |||
The Clipper Chip needed that both parties send a Law Enforcement Access Field(LEAF) with every communication. Agencies that were authorized could then retrieve the key from the LEAF and decrypt the communication. | |||
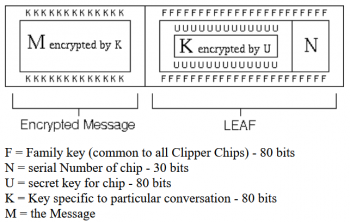
==The LEAF== | ==The LEAF== | ||
For the construction of the LEAF, the following information was needed: | |||
*Unit ID: an unique identifier for each Clipper Chip | |||
*Session key: the key that was used to encrypt the communication | |||
*additionaly a 16 Bit cheksum was added at the end of the LEAF | |||
The session key was encrypted with an unit key, the whole LEAF itself was the also encrypted with a family key. | |||
The unit key was split in two parts and each part was stored at one of the two escrow agencies. | |||
When a Clipper Chip secured device, communicates in safe (encrypted) mode, a LEAF (Law Enforcement Access Field) is exchanged. | When a Clipper Chip secured device, communicates in safe (encrypted) mode, a LEAF (Law Enforcement Access Field) is exchanged. | ||
[[File:LEAF.png|350px|text-top|thumb|alt=ALT|The LEAF|none]] | [[File:LEAF.png|350px|text-top|thumb|alt=ALT|The LEAF|none]] | ||
If a LEAF does not pass integrity checks or no LEAF is sent the use of the safe mode is not possible. | |||
If a LEAF does not pass integrity checks | |||
==The encryption and decryption process== | ==The encryption and decryption process== | ||
| Line 30: | Line 45: | ||
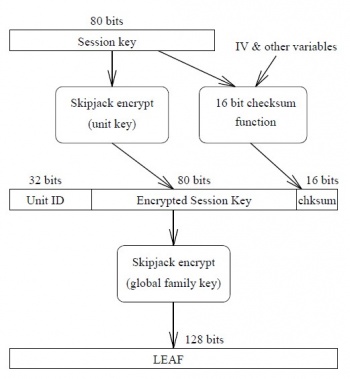
'''The encryption:''' | '''The encryption:''' | ||
1. The | 1. The communication is encrypted with the session key. | ||
2. The LEAF is | 2. The session key is then encrypted with the unit key. | ||
3. With the unit ID, the encrypted session key and the checksum the LEAF is created. | |||
4. The LEAF itself is the encrypted with the family key. | |||
'''The decryption:''' | '''The decryption:''' | ||
1. The LEAF is decrypted with the family-key, which reveals: the unit-id, the unit-key encrypted session-key and the LEAF checksum. | |||
2. Law enforcement agencies can obtain the unit key from the escrow agencies. Therefor they need the unit id to get the unit key. | |||
3. With the unit key the session key can be decrypted. | |||
4. With the session key, the whole communication can be decrypted. | |||
=Vulnerability= | =Vulnerability= | ||
The Escrowed Encryption System used in the Clipper Chip had several vulnerabilities | The Escrowed Encryption System used in the Clipper Chip had several vulnerabilities that undermined its purpose to encrypt communication safely while giving authorised 3rd parties access. | ||
The 1st publicised vulnerabilities were described by Matt Blaze in a paper called "Protocol Failure in the Escrowed Encryption Standard". Where Balze described (alongside a thorough analysis of the encryption techniques used within the Clipper Chip) | The 1st publicised vulnerabilities were described by Matt Blaze in august 1994 in a paper called "Protocol Failure in the Escrowed Encryption Standard". Where Balze described (alongside a thorough analysis of the encryption techniques used within the Clipper Chip) methods to prevent access to the session key for 3rd parties. The vulnerabilities he showed did were not a security issue as it did not allow to decrypt the communication, but prevented the EES from providing the session key to 3rd parties. | ||
The paper distinguished between the communication between so called "rogue applications" and between "rogue applications" and official application. Rogue applications are self written applications, that uses the Clipper Chip for encryption. | |||
==Communication between rogue applications== | |||
This was the easiest way to prevent access to the session key for 3rd parties. | |||
One method was called LEAF obscuring. Here the LEAF itself was additionally encrypted with another algorithm, so 3rd parties were not able to decrypt the LEAF. | |||
The second method was called LEAF Feedback. The idea was to not sent the LEAF with the communication. Both sides created a LEAF and send it to themself instead of sending it with the encrypted communication. | |||
==Communication between rogue and official applications== | |||
The second method was more complex. It allowed communication between a rogue (tampered) device and an official device. | |||
The idea behind this was to send a valid LEAF which did not contain the session key used to encrypt the communication. | |||
One possible method was to create a LEAF with another key, that was different to the used session key. This LEAF would be considered to be valid by the counterpart. | |||
As the LEAF was only validated by the 16 Bit checksum, it was also possible to just create a random string as LEAF. It would take in average 2^16 tries to generate a valid LEAF with this method. | |||
=Consequences= | |||
These vulnerabilities and the growing public backlash regarding the key escrowing and privacy concerns lead to the failure of the Clipper Chip. Companys were not willing to use the Clipper Chip for their products and people were not willing to use it. Only one product was build with the Clipper chip, the AT&T TSD-3600-E. Only a few thousand units were build and delivered to U.S. Government Agencies. | |||
By 1996 the Clipper Chip was abandoned. | |||
=Recent developments= | |||
Edward Snowden's 2013 revelations exposed NSA's global surveillance program, prompting tech giants like Google and Apple to enhance encryption. Apple fortified iPhones with unique mathematical algorithms, securing emails, photos, and contacts. Google followed suit, strengthening encryption across services. | |||
A 2023 report reveals U.S. government demands from Apple and Google for push notification data, which could be then readable and identifying individuals. This is sparking concerns from US Senator Ron Wyden about privacy and transparency in the ongoing debate on security versus individual freedoms. | |||
= References = | = References = | ||
| Line 64: | Line 94: | ||
* https://www.epic.org/crypto/clipper/white_house_statement_2_94.html | * https://www.epic.org/crypto/clipper/white_house_statement_2_94.html | ||
* https://www.epic.org/crypto/clipper/foia/att3600_2_9_93.html | * https://www.epic.org/crypto/clipper/foia/att3600_2_9_93.html | ||
* https:// | * Blaze, M.(1994).Protocol Failure in the Escrowed Encryption Standard | ||
* https://csrc.nist.gov/CSRC/media//Projects/Cryptographic-Algorithm-Validation-Program/documents/skipjack/skipjack.pdf | |||
* https://www.cryptomuseum.com/crypto/att/tsd3600/index.htm | |||
* https://www.theguardian.com/world/interactive/2013/nov/01/snowden-nsa-files-surveillance-revelations-decoded#section/1 | |||
* https://www.nytimes.com/2014/09/27/technology/iphone-locks-out-the-nsa-signaling-a-post-snowden-era-.html | |||
* https://www.404media.co/us-government-warrant-monitoring-push-notifications-apple-google-yahoo/ | |||
[[Category:Documentation]] | [[Category:Documentation]] | ||
Latest revision as of 20:04, 8 January 2024
Summary
This document shows an overview about the Clipper Chip, which was part of the capstone program. The chip was introduced by the U.S. Government in 1993. Its use was abandoned in 1996 and its algorithm has been declassified in 1998.
Description
The Clipper Chip is a small Chipset, that was developed by the NSA (National Security Agency) and advertised by the U.S. Government, in the early 90´s. The idea was, that the Chipset would be integrated in Communication devices like telephones or personal computers and to securely encrypt their Communication, while giving the U.S. Government the possibility to decrypt the communication. This was done by the use of a Key Escrow Algorithm.
Origin
According to official U.S. Government Documents, the origins of the Clipper Chip program, can be traced to the "Computer Security act of 1987". This Act was meant to ammend legislation of the Year 1949, to create security standards for non-military computer systems. in 1993 The U.S. Government introduced an initiative, that should provide security for communication of non-classified data with a special Chipset, called the Clipper Chip. The goal was to at first equip the DoJ (Department of Justice) with phones containing the Clipper Chip and then extend its use to the US high-tech industry.
Functionality
For the encryption of the communication the Clipper Chip uses the Skipjack-algorithm. For the key escrow, the Escrowed Encryption Standard was used.
Skipjack Algorithm
The Skipjack algorithm is a blockcipher with a blocksize of 64 bit. The key length was 80 bit. It supported modes of operation are Output Feedback Mode(OFB), Cipher Feedback Mode(CFB), Electronic Code Book(ECB) and Cipher Block Chaining(CBC). The key exchange was done with a Diffi Hellmann algorithm. It was developed by the NSA and declared secret. This prohibited civilian experts from analysing the algorithm. Skipjack should replace the DES algorithm that was the standard at the time and was considered not to be secure anymore.
Escrowed Encryption Standard
The most important feature of the Clipper Chip was the possibility to retrieve the session key. This should allow law enforcement agencies to encrypt communication that was obtained for example via wiretaping. The Clipper Chip needed that both parties send a Law Enforcement Access Field(LEAF) with every communication. Agencies that were authorized could then retrieve the key from the LEAF and decrypt the communication.
The LEAF
For the construction of the LEAF, the following information was needed:
- Unit ID: an unique identifier for each Clipper Chip
- Session key: the key that was used to encrypt the communication
- additionaly a 16 Bit cheksum was added at the end of the LEAF
The session key was encrypted with an unit key, the whole LEAF itself was the also encrypted with a family key. The unit key was split in two parts and each part was stored at one of the two escrow agencies.
When a Clipper Chip secured device, communicates in safe (encrypted) mode, a LEAF (Law Enforcement Access Field) is exchanged.
If a LEAF does not pass integrity checks or no LEAF is sent the use of the safe mode is not possible.
The encryption and decryption process
The encryption:
1. The communication is encrypted with the session key.
2. The session key is then encrypted with the unit key.
3. With the unit ID, the encrypted session key and the checksum the LEAF is created.
4. The LEAF itself is the encrypted with the family key.
The decryption:
1. The LEAF is decrypted with the family-key, which reveals: the unit-id, the unit-key encrypted session-key and the LEAF checksum.
2. Law enforcement agencies can obtain the unit key from the escrow agencies. Therefor they need the unit id to get the unit key.
3. With the unit key the session key can be decrypted.
4. With the session key, the whole communication can be decrypted.
Vulnerability
The Escrowed Encryption System used in the Clipper Chip had several vulnerabilities that undermined its purpose to encrypt communication safely while giving authorised 3rd parties access. The 1st publicised vulnerabilities were described by Matt Blaze in august 1994 in a paper called "Protocol Failure in the Escrowed Encryption Standard". Where Balze described (alongside a thorough analysis of the encryption techniques used within the Clipper Chip) methods to prevent access to the session key for 3rd parties. The vulnerabilities he showed did were not a security issue as it did not allow to decrypt the communication, but prevented the EES from providing the session key to 3rd parties.
The paper distinguished between the communication between so called "rogue applications" and between "rogue applications" and official application. Rogue applications are self written applications, that uses the Clipper Chip for encryption.
Communication between rogue applications
This was the easiest way to prevent access to the session key for 3rd parties. One method was called LEAF obscuring. Here the LEAF itself was additionally encrypted with another algorithm, so 3rd parties were not able to decrypt the LEAF. The second method was called LEAF Feedback. The idea was to not sent the LEAF with the communication. Both sides created a LEAF and send it to themself instead of sending it with the encrypted communication.
Communication between rogue and official applications
The second method was more complex. It allowed communication between a rogue (tampered) device and an official device. The idea behind this was to send a valid LEAF which did not contain the session key used to encrypt the communication. One possible method was to create a LEAF with another key, that was different to the used session key. This LEAF would be considered to be valid by the counterpart. As the LEAF was only validated by the 16 Bit checksum, it was also possible to just create a random string as LEAF. It would take in average 2^16 tries to generate a valid LEAF with this method.
Consequences
These vulnerabilities and the growing public backlash regarding the key escrowing and privacy concerns lead to the failure of the Clipper Chip. Companys were not willing to use the Clipper Chip for their products and people were not willing to use it. Only one product was build with the Clipper chip, the AT&T TSD-3600-E. Only a few thousand units were build and delivered to U.S. Government Agencies. By 1996 the Clipper Chip was abandoned.
Recent developments
Edward Snowden's 2013 revelations exposed NSA's global surveillance program, prompting tech giants like Google and Apple to enhance encryption. Apple fortified iPhones with unique mathematical algorithms, securing emails, photos, and contacts. Google followed suit, strengthening encryption across services.
A 2023 report reveals U.S. government demands from Apple and Google for push notification data, which could be then readable and identifying individuals. This is sparking concerns from US Senator Ron Wyden about privacy and transparency in the ongoing debate on security versus individual freedoms.
References
- https://www.epic.org/crypto/clipper/white_house_statement_2_94.html
- https://www.epic.org/crypto/clipper/foia/att3600_2_9_93.html
- Blaze, M.(1994).Protocol Failure in the Escrowed Encryption Standard
- https://csrc.nist.gov/CSRC/media//Projects/Cryptographic-Algorithm-Validation-Program/documents/skipjack/skipjack.pdf
- https://www.cryptomuseum.com/crypto/att/tsd3600/index.htm
- https://www.theguardian.com/world/interactive/2013/nov/01/snowden-nsa-files-surveillance-revelations-decoded#section/1
- https://www.nytimes.com/2014/09/27/technology/iphone-locks-out-the-nsa-signaling-a-post-snowden-era-.html
- https://www.404media.co/us-government-warrant-monitoring-push-notifications-apple-google-yahoo/