Cross-Site-Scripting (XSS)
Cross-Site-Scripting (XSS)
Attackers use Webapplications injecting client-side code to gain data from users, like cookies or private information. It's also possible to trigger actions on websites, redirect to other sites or hide advertisements. A short game with which some options can be seen easily: XSS game
Types
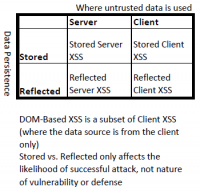
There are two ways to classify XSS attacks. Up until 2012 the types DOM-based (Type 0), stored/persistent (Type I) and reflected/non-persistent (Type II) were used. As these three types can overlap the research community started to use the terms Server XSS and Client XSS from 2012 on.
Persistent (Type I)
This can occur if user input is permanently stored on a server or in the web browser. The victims get the data then directly from there.
Reflected (Type II)
Malicious code is directly injected using the request. Hereby the data sent by an http-Request is directly used to perfom actions.
DOM Based (Type 0)
DOM Based attacks were added in 2005 and are attacks that take place entirely within the web browser.
Prevention
- Never trust user input
- Recursive sanitization
- Encoding