Cross-Site-Scripting (XSS)
Cross-Site Scripting (XSS)
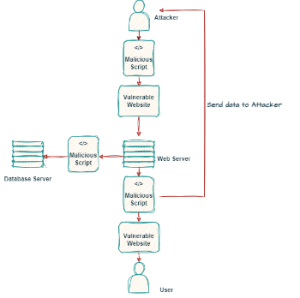
Cross-Site Scripting is a class of web application vulnerabilities, which is still one of the most common security vulnerabilities in web applications and can be used to compromise the confidentiality, integrity, and availability of the application. In general, XSS vulnerabilities allow an attacker to execute script code in the web browser of the victim and can be used to gain data from users, like cookies or private information. The different types are listed below. It is also possible to trigger actions on websites, redirect to other sites or hide advertisements. A short game with which some options can be seen easily: XSS game
Types
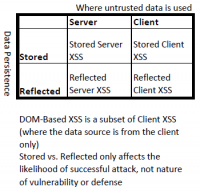
There are two ways to classify XSS attacks. Up until 2012 the types DOM-based (Type 0), stored/persistent (Type I) and reflected/non-persistent (Type II) were used. However, due to the potential overlap among these three types, the research community introduced the terms Server XSS and Client XSS from 2012 onward.
Stored (Type I)
Stored XSS, also known as persistent XSS, occurs when the application or API stores unvalidated user input on the server, for example, in a database, comment field, visitor log, etc. This stored input is later retrieved and displayed by another user or administrator who requests the stored information.
Reflected (Type II)
Reflected XSS is a non-persistent attack and is used to steal session cookies from a user. With Reflected XSS, the application or API includes unchecked and unmasked input from the user as part of the HTML output. If the attack was successful, the attacker could execute arbitrary HTML and a scripting language such as Javascript in the victim's browser. Typically, a user will have to click on a malicious link to do this. The attacker tries to bring this harmful link to the victim, via advertising, e-mail etc.
DOM Based (Type 0)
DOM-based Cross-Site Scripting (XSS) is a type of XSS attack that occurs when malicious code is injected directly into the Document Object Model (DOM) of the web application. DOM-based XSS attacks can occur when user-supplied data is used to generate client-side JavaScript code without proper input validation. The malicious code is then sent to a user's browser, where it is executed. DOM-based XSS attacks can be used to gain access to sensitive information, perform malicious activities, and even hijack the user’s browser.
XSS attack consequences
A Cross-Site Scripting (XSS) attack can have various severe consequences, including:
Data Theft: Stealing sensitive user data such as login credentials, session tokens, and personal information.
Identity Theft: Stealing user identities to take over their accounts, resulting in fraudulent activity.
Session Hijacking: Taking control of user sessions and accessing their accounts without the user's knowledge.
Malware Propagation: Injecting the malicious code into websites, which is then executed by unsuspecting users, resulting in the spread of malware.
Phishing: XSS can be employed to display fake login forms or deceptive content on legitimate websites, leading to phishing attacks.
Content Manipulation: Manipulation of website content to send users false information or carry out malicious actions on their behalf.
Reputation Damage: Cross-Site Scripting (XSS) attacks have the potential to damage user confidence in a website or application, particularly in cases where personal information is exposed.
Prevention
The prevention of these vulnerabilities is the responsibility of the programmer. Programmers should adopt secure programming practices, such as context-sensitive server-side output encoding, to ensure the prevention of malicious script injections through incorrect or unchecked entries.
Effective prevention measures include:
Input validation: Rigorous validation of user input before acceptance and processing by the server is crucial to prevent cross-site scripting attacks.
Output encoding: Encoding all output data (using HTML entities) is another effective measure to prevent cross-site scripting. This ensures proper display in the user's browser.
Content Security Policy (CSP): Implementing a Content Security Policy defines rules for the types of content a website can load, contributing to preventing cross-site scripting attacks.
Use of tokens: Employing random character strings (tokens) to identify users can help prevent cross-site scripting attacks, ensuring that only authorized users access the website.
Disabling script execution: While disabling script execution on the server, especially for certain scripting languages like JavaScript or VBScript, can help prevent cross-site scripting, it is rarely used due to the widespread use of JavaScript.
Secure Password Policies: It is recommended to use complex passwords and consider introducing multi-factor authentication for an additional layer of security.
Session Management: The application of session management, such as session timeout, involves configuring actions related to sessions.
Security Patching: Ensuring that all software, including web servers, databases and frameworks, are kept up to date with the latest security patches. Regular updates and patches should be applied to fix known vulnerabilities in the system.
Security Audits and Code Reviews: Conducting regular security audits and code reviews to help identify and remediate potential vulnerabilities. Third-party security assessments can provide an independent assessment of your application's security posture.
References
- https://owasp.org/www-community/attacks/xss/
- https://cheatsheetseries.owasp.org/cheatsheets/DOM_based_XSS_Prevention_Cheat_Sheet.html
- https://owasp.org/www-project-top-ten/2017/A7_2017-Cross-Site_Scripting_(XSS)
- https://portswigger.net/web-security/cross-site-scripting
- https://www.sans.org/white-papers/988/
- https://learn.microsoft.com/en-us/aspnet/core/security/cross-site-scripting?view=aspnetcore-8.0
- https://www.wallarm.com/what/a7-cross-site-scripting-xss-2017-owasp