Hak5 Key Croc
Summary
This article describes the Hak5 Key Croc, a smart hardware keylogging device.
Key Croc Basics
The Key Croc has to be connected to the target device via USB. Once it is installed between a PC and its keyboard, it starts its booting process, indicated by the LED changing its color. After it has booted, the LED is turned off and the Key Croc is now in Attack Mode.
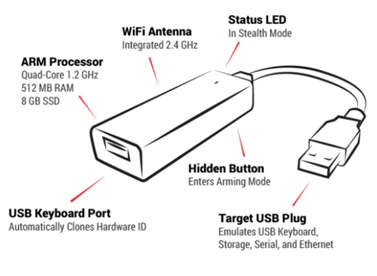
Attack Mode
Attack Mode is visible from the outside by the LED being turned off. In this mode, the Key Croc clones the hardware identifier of the keyboard connected to it and poses as this keyboard. Thus, each keystroke entered via the keyboard is sent to the PC, but also recorded in the Key Croc’s loot file. Payloads may be triggered by typing the required keyword. Pressing the hidden button on the back of the Key Croc will cause it to enter Arming Mode.
Arming Mode
Arming Mode is visible from the outside by the LED blinking blue. In Arming Mode, no further keystrokes are recorded and payloads can’t be activated anymore. Instead, the Key Croc emulates a USB flash disk and a serial device, allowing the user to access it via the device’s file manager. A password and timeout to enter the Arming Mode can be configured in the Key Croc’s config file, if they aren’t configured the Key Croc will enter Arming Mode as soon as the button is pressed.
Key Croc's File System
- config.txt – configuration file
- upgrade.html – shortcut to software update documentation
- version.txt – current version
- docs/ – license and quick start guide
- languages/ – hosts keymap files used for recording and injection
- library/ – hosts inactive payloads
- loot/ – hosts captured keystrokes and other logs
- payloads/ – hosts active payloads
- tools/ – used to install additional packages
LED Colors
- Green – Booting up
- Red – Error
- Cyan – Configuring Wi-Fi per config.txt
- Magenta – Configuring Keylogger
- Blue – Arming Mode
- Yellow – Disk Full
- White – No Keyboard Detected
Payloads
The Key Croc offers the possibility to execute payloads on the targeted device. To be able to get activated, the payloads have to exist as either .txt or .sh files in the payloads/ directory on the Key Croc. Payloads that aren’t currently used can be stored in the library/ directory. Most payloads activate on MATCH, meaning that if a certain string is typed, the payload will be triggered. The date and time of activation of a payload is logged in the associated log file in the loot/ folder. The language used in the payloads is Ducky Script 2.0, or QUACK. Payloads can be written by the pentester themselves, or downloaded from the Hak5 GitHub repository. EXAMPLE
Tools
Additional pentesting tools like Metasploit might be installed on the Key Croc. Installation requires an active WiFi connection (which can be configured in the config.txt) and can be done via SSH, Cloud C2, or serial connection. After installation, these tools can be found in the tools/ directory.