Hak5 Packet Squirrel
Summary
The Packet Squirrel is the perfect pen testing tool because it operates as an Ethernet Man in the Middle and comes preloaded with three exploit scripts.
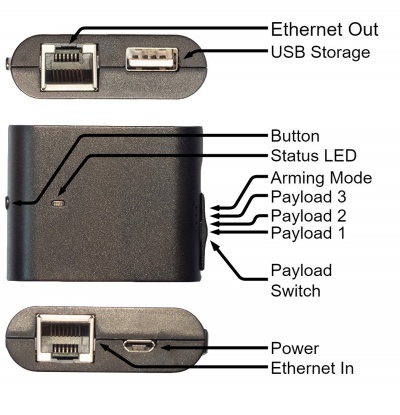
File:Packet Squirrel Connectors.jpg
Description
The Packet Squirrel has an switch to choose between the three exploit payloads for logging the TCP dump, Using VPN Tunnelling and for DNS spoofing or to est it in arming mode.
An arming mode (switch in 4th position) you can easily access the device by ssh to root@172.16.32.1 with the password hak5squirrel. It is also able to gain ssh access to the device during the attack modes with the IP address of the outgiong Ethernet interface.
Basic Cable Setup
- Plug the victims Ethernet cable into the "Ethernet In" Port
- Plug the gateway Ethernet cable into the "Ethernet Out" Port
- Power the device by plugging in the power cable
TCP/UDP Dumping Mode
- A USB Stick with an NTFS file system needs to be plugged in the USB-A Port before the Squirrel is Powered up.
- Flip the first position (which is nearest to the micro USB power in).
- Connect the Ethernet cable of the victim into the Ethernet port, which is at the same side as the power in USB connector and Connect the Gateway Ethernet cable to the other Port.
- Plug the power cable in and wait the one minute long start up sequence. The device can be either by the victim be self or by an USB power bank.
- The data traffic will be captured, if the LED starts blinking Yellow. If otherwise the LED circles between red, green and blue, then the USB stick has the wrong file system.
- Stop the capturing process by pressing the Button. Then the device takes some seconds to write it to the USB Storage. As soon as the LED glows red the saving process ended and you are good to go
- you can now analyse the captured pcap file with wireshark.
DNS Spoofing Mode
- For this mode we have to start in arming mode (switch at fourth position)
- After gaining access with ssh we change to the DNS spoofing directory with
cd /payloads/switch2. - There we can define the Spoofed domain names by editing the spoofhost file
Example: address=/abc.com/216.58.207.164 This Example would DNS spoof abc.com with an google IP, but this didn't work because Browser checks the Certificates and discovers the Spoofed IP.
- Unplug the Packet Squirrel and shift the switch to the second position.
- Plug it in and wait until the startup sequence is finished and the LED starts blinking yellow.
OpenVPN Mode
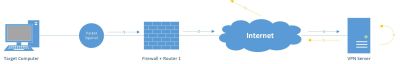
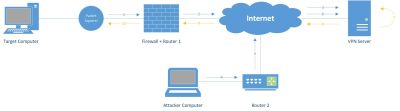
The VPN payload implements VPN access mode and VPN tunnelling mode. If you want to Setup your own OpenVPN (OVPN) server follow the instructions at the hak5 webpage. For the purpose of testing we use use an existing server from freeopenvpn.org.
- Start by selecting the desired server and download the the OVPN access certificate.
- Set the Packet Squirrel in Arming Mode and connect to its shell
- Copy the certificate with
scp user@server:downloadfolder/filename.ovpn /root/payloads/switch3/config.ovpn - Steer to the directory with
cd /root/payloads/switch3/ - Edit the config.ovpn at line 30 to
auth-user-pass credentials.txt - Add an credentials file with
nano credentials.txtand add the two lines:freeopenvpn<the displayed password>
- Before starting the VPN we choose the VPN mode:
- Open the
payload.sh - Set the
For_Clients=to0for Access Mode1for Tunneling Mode
- Open the