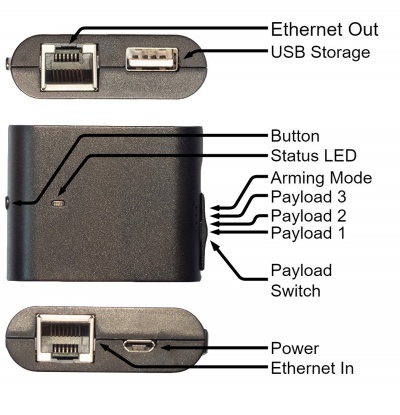
Hak5 Packet Squirrel
Summary
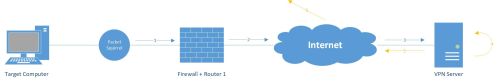
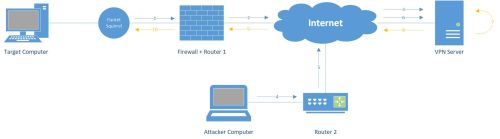
The Packet Squirrel operates as an Ethernet Man in the Middle and comes preloaded with three exploit scripts.
Description
The Packet Squirrel has an switch to choose between the three exploit payloads for logging the TCP dump, Using VPN Tunnelling and for DNS spoofing, or arming mode.
An arming mode (switch in 4th position) you can easily access the device with ssh root@172.16.32.1 with the password hak5squirrel. It is possible to gain ssh access to the device during the attack modes with the IP address of the outgiong Ethernet interface as well.
Basic Cable Setup
- Plug the victims Ethernet cable into the "Ethernet In" Port
- Plug the gateway Ethernet cable into the "Ethernet Out" Port
- Power the device by plugging in the power cable
TCP/UDP Dumping Mode
- A USB Stick with an NTFS file system needs to be plugged in the USB-A Port before the Squirrel is Powered up.
- Flip the first position (which is nearest to the micro USB power in).
- Connect the Ethernet cable of the victim into the Ethernet port, which is at the same side as the power in USB connector and Connect the Gateway Ethernet cable to the other Port.
- Plug the power cable in and wait the one minute long start up sequence. The device can be either powered by the victim machine or by an USB power bank.
- The data traffic will be captured, if the LED starts blinking Yellow. If otherwise the LED circles between red, green and blue, then the USB stick has the wrong file system.
- Stop the capturing process by pressing the Button. Then the device takes some seconds to write the tcpdum to the USB Storage. As soon as the LED glows red the saving process has ended and you are good to go.
- You can now analyse the captured pcap file with wireshark.
DNS Spoofing Mode
- For this mode we have to start in arming mode (switch at fourth position)
- After gaining access with ssh we change to the DNS spoofing directory with
cd /payloads/switch2. - There we can define the Spoofed domain names by editing the
spoofhostfile
Example: address=/abc.com/216.58.207.164 #This Example would DNS spoof abc.com with an google IP, but this didn't work because Browser checks the Certificates and discovers the Spoofed IP.
- Unplug the Packet Squirrel and shift the switch to the second position.
- Plug it in and wait until the startup sequence is finished and the LED starts blinking yellow.
OpenVPN Mode
The VPN payload implements VPN access mode and VPN tunnelling mode. If you want to Setup your own OpenVPN (OVPN) server follow the instructions at the hak5 webpage. For the purpose of testing we use use an existing server from freeopenvpn.org.
- Start by selecting the desired server and download the the OVPN access certificate.
- Set the Packet Squirrel in Arming Mode and connect to its shell
- Copy the certificate with
scp user@server:downloadfolder/filename.ovpn /root/payloads/switch3/config.ovpn - Steer to the directory with
cd /root/payloads/switch3/ - Edit the config.ovpn at line 30 to
auth-user-pass credentials.txt - Add an credentials file with
nano credentials.txtand add the two lines:freeopenvpn<the displayed password>
- Before starting the VPN we choose the VPN mode:
- Open the
payload.sh - Set the
For_Clients=to0for Access Mode1for Tunneling Mode
- Open the
- Now set the Switch the the third Position and plug power out and in again
- You are good to go, if the yellow LED starts to flash after the boot up sequence
Access Mode
Access mode allows the squirrel to access the VPN Network via the Secure Shell
If the connection was established if the command ifconfig tun0 show the following output when it is issued at the Packet Squirrels Shell.
tun0
Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.231.245 P-t-P:192.168.231.245 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:12 errors:0 dropped:0 overruns:0 frame:0
TX packets:8 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:1404 (1.3 KiB) TX bytes:608 (608.0 B)
The Access Mode can be used to access an Private network that is used for testing and pen testing purposes like an honeypot virtual machine.
Tunneling Mode
The Tunnelling mode encapsulates all the traffic and sends it to the VPN Server, from where it is send to the internet. VPN Tunnelling allows users to disguise their IP address you can check your current IP address with ipchicken.com.
Creating your own Payloads
The Packet Squirrel allows us to create our own attack payloads by loading them to the USB stick and naming them Switch1 to Switch3.
It allows as to create payload in python, bash or PHP. For Python and Bash it is important to use the interpreter directive Python: #!/usr/bin/python, bash: #!/usr/bin/bash.
Bash scripts can access the following pre-installed tools:
- openvpn
- autossh
- tcpdump
- meterpreter-https
- cron
- nmap
- ncat-ssl
- ncat
- sshfs
- tcpdump
- wget
For more information go to the hak5.org webpage.