Difference between revisions of "Hak5 Plunder Bug"
Jump to navigation
Jump to search
| Line 1: | Line 1: | ||
== Summary == | == Summary == | ||
[[File:.jpg |thumb|right|400px||Plunder Bug]] | [[File:.jpg |thumb|right|400px||Plunder Bug]] | ||
[[File:PlunderBugTapping.jpg |thumb|right| | [[File:PlunderBugTapping.jpg |thumb|right|500px||Plunder Bug Network Deployment]] | ||
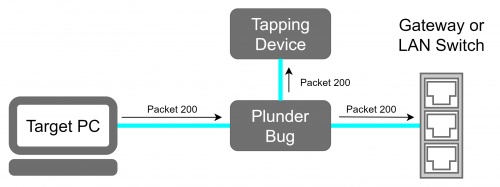
This device is an Pocket sized LAN tap. This device is being used for passive eavesdropping and is small enough to be placed everywhere without being recognized. | This device is an Pocket sized LAN tap. This device is being used for passive eavesdropping and is small enough to be placed everywhere without being recognized. | ||
Revision as of 07:56, 3 June 2020
Summary
File:.jpg
Plunder Bug
This device is an Pocket sized LAN tap. This device is being used for passive eavesdropping and is small enough to be placed everywhere without being recognized.
Description
The Plunder Bug is an simplistic form of the Hak5 Packet Squirrel. It allows the user to Tap network traffic and to access it for network scanning.
Deployment
Enter these commands in the shell
echo foo echo bar
Step 2
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)