Difference between revisions of "Hak5 Plunder Bug"
| Line 32: | Line 32: | ||
=== Sniffing Data === | === Sniffing Data === | ||
==== Local Access ==== | |||
If you can access the tapping device locally, open wire shark and use the ethernet interface which gets deployed from the Plunder Bug with the USB cable. | |||
==== Remote Access ==== | |||
You can capture | |||
'''Sniffing Node''' | |||
# Make sure that tcpdump and ssh-server is installed | |||
'''Wireshark Machine''' | |||
# Configure the SSH Remote capture Interface | |||
# Server Tab: | |||
## Enter IP | |||
## Enter Port (usually 22) | |||
# Server Tab: | |||
## Enter Username & Password | |||
# Capture Tab: | |||
## Enter Capturing Interface into Remote Interface | |||
==== Dumping all Data ==== | |||
== Used Hardware == | == Used Hardware == | ||
Revision as of 09:12, 3 June 2020
Summary
This device is an Pocket sized LAN tap. This device is being used for passive eavesdropping and is small enough to be placed everywhere without being recognized.
Description
The Plunder Bug is an simplistic form of the Hak5 Packet Squirrel. It allows the user to Tap network traffic and to access it for network scanning.
Deployment
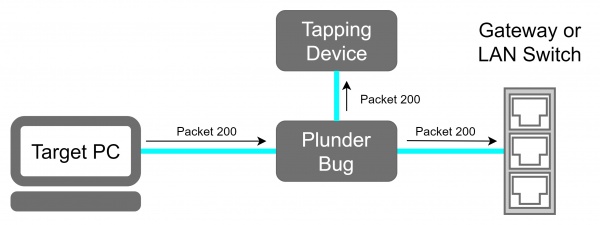
- Connect the Ethernet port of the victim machine with one of the two Ethernet Ports of the Plunder Bug via an short Ethernet cable.
- Connect the other Ethernet port with the with the Ethernet cable which was previously plugged in the victim device.
- Power up the Plunder Bug by Connecting the USB-C female to USB-A male cable with an device which is under your control (preferably a raspberry pi with an battery shield).
Plunder Bug Modes
The Plunder Bug Allows us to run it in two modes "muted" and "unmuted". The Plunder Bug is mirroring all network traffic and sends it to the USB-C port, when its operating in the muted mode. The unmuted mode gives the USB-C device an IP address that the tapping device is able to connect to the internet or running network scans.
To change between the Plunder Bug modes downlaod the shell script from downloads.hak5.org: Usage:
- make it executable with
chmod +x ./plunderbug.sh - run the script as root or superuser:
./plunderbug.sh [options]
Options:
--mute to use mute mode
--unmute to use unmuted mode
Sniffing Data
Local Access
If you can access the tapping device locally, open wire shark and use the ethernet interface which gets deployed from the Plunder Bug with the USB cable.
Remote Access
You can capture Sniffing Node
- Make sure that tcpdump and ssh-server is installed
Wireshark Machine
- Configure the SSH Remote capture Interface
- Server Tab:
- Enter IP
- Enter Port (usually 22)
- Server Tab:
- Enter Username & Password
- Capture Tab:
- Enter Capturing Interface into Remote Interface
Dumping all Data
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)