Difference between revisions of "Heartbleed"
Jump to navigation
Jump to search
APuchinger (talk | contribs) |
APuchinger (talk | contribs) |
||
| Line 46: | Line 46: | ||
== Attack == | == Attack == | ||
The result of a Hearbleed Bug is shown in the following picture. | The result of a Hearbleed Bug is shown in the following picture. | ||
[[File:HeartbleedAttack.png]] | |||
=== Interpretation === | |||
The left hand column represents the HEAP address, the middle column contains the fetched data in a hexadecimal representation. | |||
The right hand column is the actual readable output. Here may stand user credentials, banking informations or even the encryption method. | |||
(Reminder: the attacked server must implement an OpenSSL version between 1.0.1 and 1.0.1.f) | |||
Revision as of 20:46, 17 January 2022
Summary
This page explains the background information of the "Heartbleed"- bug. The purpose of this documentation is not to guide attackers to reproduce the heartbleed attack, it should only highlight the functionality.
Requirements
- Webserver e.g. (nginx / apache)
- OpenSSL between version 1.0.1 and 1.0.1f (Download from https://github.com/openssl/openssl/branches/all)
Background
- HTTP communication usually takes place over TCP/IP connections
- TCP is reliable but, a continuous data exchange is needed.
- HTTPS Websites are encrypted with SSL
- The Webserver has available sockets which allows connections to clients
- Webserver have timers, after a set time of x - seconds the session gets closed if the client is inactive
- To keep the session alive, the web-browser sends heartbeat requests which are processed by the server
Heartbeat
- Is an extension in OpenSSL
- Special data package
- Possible size: 16 Bytes < Heartbeat Message < 64Kb
- “Heartbeat Requests” are sent from Webbrowser to Webserver to keep the session alive
- The server answers with a “Heartbeat Respond” which contains the exact same dataset
Example
Web browsers (client) sends a length and a message
- Web browser sends message with length 5: ‘hello’
- Web server responds with the exact same message : ‘hello’
Heartbleed
- Choose heartbeat request size as a minimum and claim it to the maximum
- The heartbeat request can be executed multiple times in a row
- Rebuild picture of servers RAM
Example
- Web browser sends message with length 65536: ‘hello’
- The server read a full 64 KiB from memory and sends it to the client
- Web server allocates a dataslot of 64 KiB and copies the message ‘hello’ in the first place. The rest of the 65536 - ‘hello’ size is appended with data in the RAM.
- mThe Web server responds with the filled 64 KiB dataslot (including content of RAM).
Attack
The result of a Hearbleed Bug is shown in the following picture.
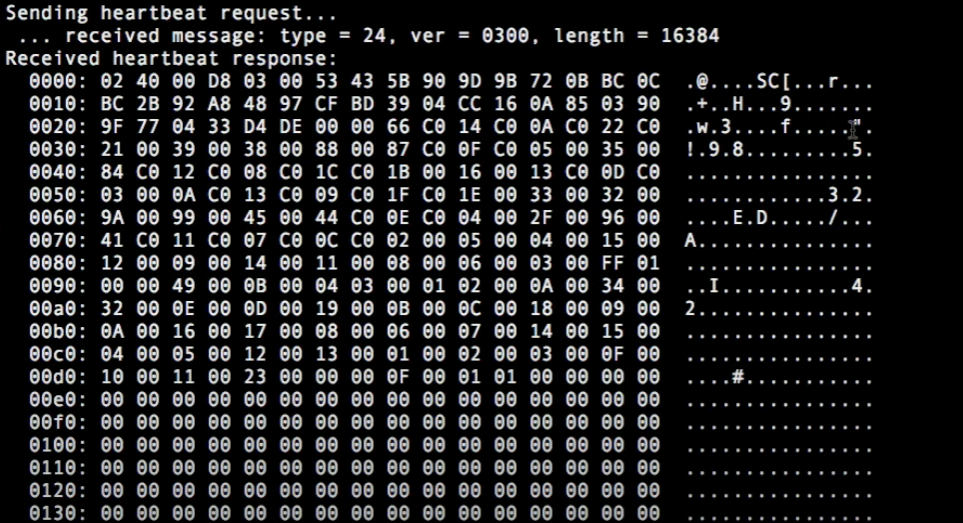
Interpretation
The left hand column represents the HEAP address, the middle column contains the fetched data in a hexadecimal representation. The right hand column is the actual readable output. Here may stand user credentials, banking informations or even the encryption method.
(Reminder: the attacked server must implement an OpenSSL version between 1.0.1 and 1.0.1.f)