IP Cameras Pentesting Report
Summary
This Article is a comprehensive descirption of a pentesting process regarding three IP Cameras ABUS PPIC32020, Blink-Mini and TP-Link NC200. In the further course of this Report the Methology of the Information Gathering Process will be pointed out, afterwards the gathered information will be analysed. With the analysis of the gathered information vulnerabilities will be pointed out. We will form attack vectors, exploit this vulnerabilites and recommend countermesaures for the vendors to make their systems more secure.
Requirements
In order to perform the Exploits the following tools were needed.
- Operating System:
- Kali Linux 2022.2
- Tools:
- Cameras:
Description
In this chapter, we will demonstrate how we were able to extract information about the target devices, form attack vectors and exploit them afterwards.
Methodology
Step 1: NMAP
We used NMAP to gather as much information as possible about the target systems. This includes IP Addresses, open Ports, Operating Systems, Services and many more. This part is crucial to gain a better understanding of how the camera works and is neccessary to perform sophisticated attacks to extract information or gain access.
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym Fyodor Vaskovich).[4] Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses.[5]
Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection,[6] vulnerability detection,[6] and other features. Nmap can adapt to network conditions including latency and congestion during a scan. [1]
To gather information about the target systems we used the following commands:
nmap -sP [Network Address/Subnetmask] Network Scan --> To discover the IP addresses of the target system inside the LAN nmap -sS -F [IP Address] TCP-SYN-Port-Scan (Host-Fast-Scan) --> Discovers open ports on target system nmap -sV [IP Address] Service Scan --> To discover the services listening on the open ports nmap -O [IP Address] Operating System Scan --> Guesses the Operating System running on target host (Based on OS Fingerprints) nmap -Pn -sV --script vuln [IP Address] Discovers possible vulnerabilities based on already known exploits for the specific service
Step 2: Man in the Middle (MitM)
In order to get a better understanding of how the architecture of the service provided by the IP Cameras works, we mounted a Man in the Middle Attack to gain information about how and where the camera connects to and how it deliveres their service to the endpoints (in our case the ABUS Camera used a Smartphone App to connect and configure the camera and the two other used Web Services). To mount the MitM attack we utilized ARP Spoofing which can easily be done with the arpspoof command.
arpspoof -i [Your network interface] -t [Target IP] [The IP you pretend to be]
In order to be able to completely execute the MitM attack, you need to enable IP forwarding otherwise the packets would be sent to you but would never arrive at their destination. To do this, enter the following command:
sysctl -w net.ipv4.ip_forward=1
If the attack was mounted correctly, you should be able to capture the traffic between the two endpoints you mounted the attack (e.g. with Wireshark).
In our case, we mounted two MitM attacks, the first one between the camera and the gateway, the second one between the smartphone or endpoint and the gateway to understand fully where and how the service connects to to provide its capabilities.
Step 3: Reverse DNS Lookup & Geo Locator
When viewing the captured traffic we stumbled over a lot of remote IP Addresses where the communication takes place. Therefore, we wanted to know the Domain of the Webservice the Camera is communicating with. To achieve this, we used the following, free to use, tools:
Step 4: Look through the, open source, firmware of the cameras (if available)
To finish our research we searched for any open and available firmware packages of any of the given cameras provided by the manifacturer.
Firmware:
- ABUS PPIC32020
- TP-Link NC200
- Blink Mini (no open and accessible firmware found)
Gathered Information
NMAP
First of all, it is important to state that the ABUS Camera used two IP interfaces for their connection to the different services therefore two IP addresses needed to be investigated. Why and how this camera uses and needs two addresses will be discussed afterwards.
| NMAP Command | ABUS PPIC32020 | TP-Link NC200 | Blink Mini |
|---|---|---|---|
| Port Scan | 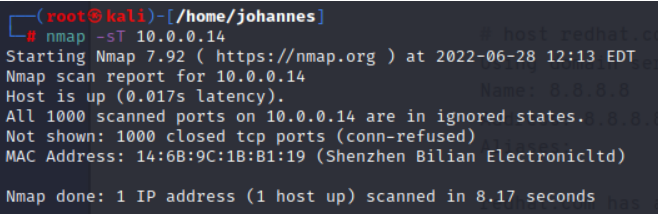 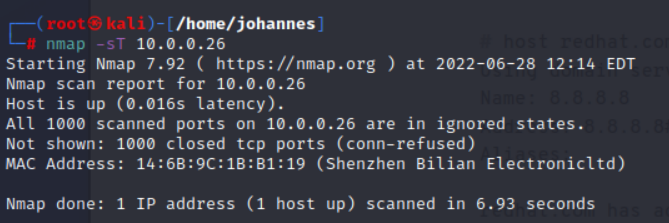 We can see that all ports on both IP Addresses are closed. |
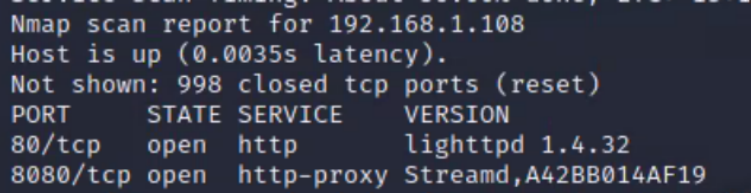 We can see that two ports (http and http-proxy) are open with the services lighttpd running. This indicates that the Camera hosts a web service. |
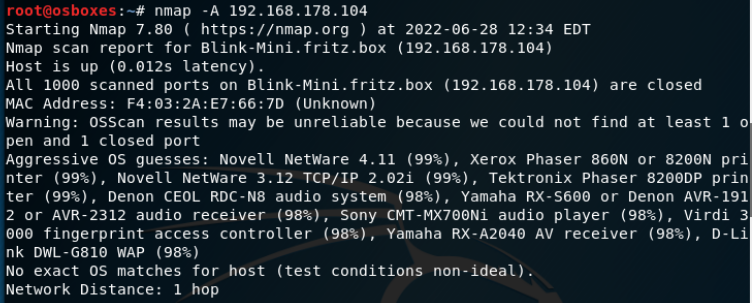 We can see that no ports are open and accessible. |
| OS Scan | 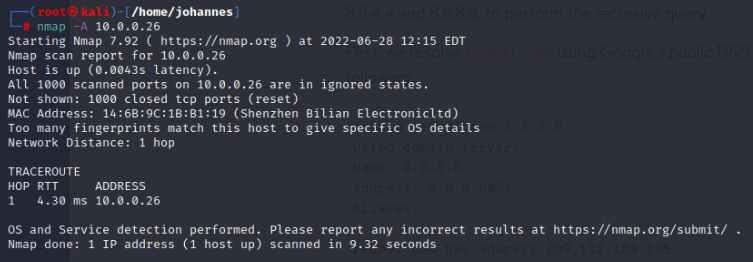 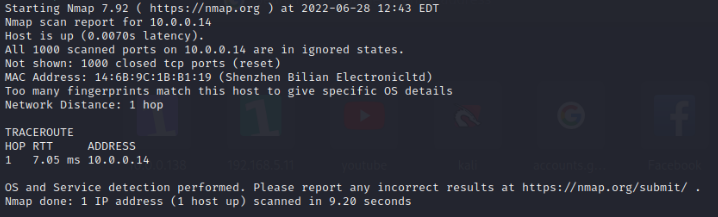 No OS Detection available since there are to many OS fingerprints. Same result with aggressive OS Guess. |
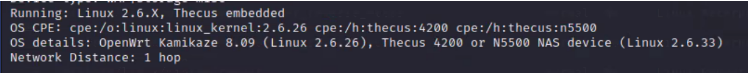 OS Details: OpenWrt Kamikaze 8.09 |
 No definite OS Guess, some suggestions. |
| Vulnerability Scan | 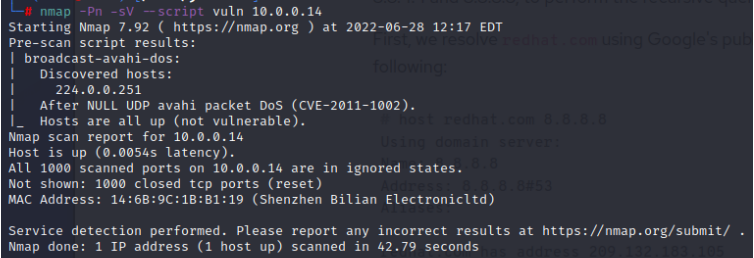 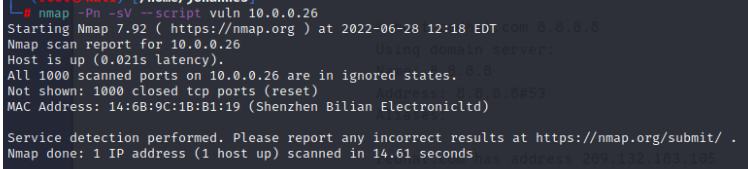 Only output: CVE-2011-1002. |
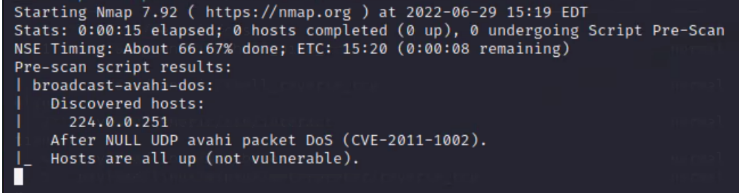 Only output: CVE-2011-1002 |
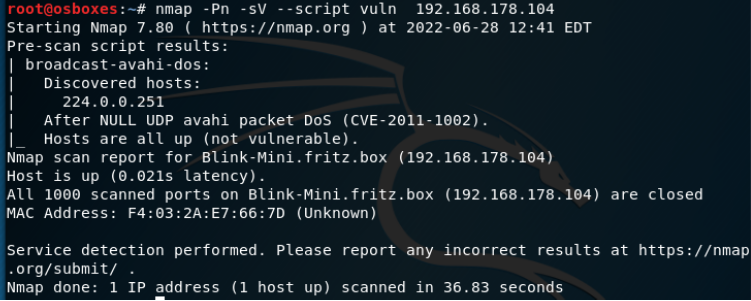 Only output: CVE-2011-1002 |
Man in the Middle, Reverse DNS Query and Geo Location
- ABUS PPIC32020
- Smartphone App connects to:
- 142.251.39.74
- Domain: bud02s39-in-f10.1e100.net.
- Located in: Budapest, Ungarn
- 35.169.53.92
- Domain: ec2-35-169-53-92.compute-1.amazonaws.com.
- Located in: Dallas, Texas, United States
- 44.195.176.7
- Domain: ec2-44-195-176-7.compute-1.amazonaws.com.
- Located in: Ashburn, Virginia, United States
- 142.251.39.74
- Camera connects to:
- 176.34.104.236
- Domain: ec2-176-34-104-236.eu-west-1.compute.amazonaws.com
- Located in: Dublin, Leinster, Ireland
- 239.255.255.250
- Multicast Address used by SSDP
- 176.34.104.236
- Smartphone App connects to:
Behaviour of ABUS PPIC32020
- Smartphone located inside Network:
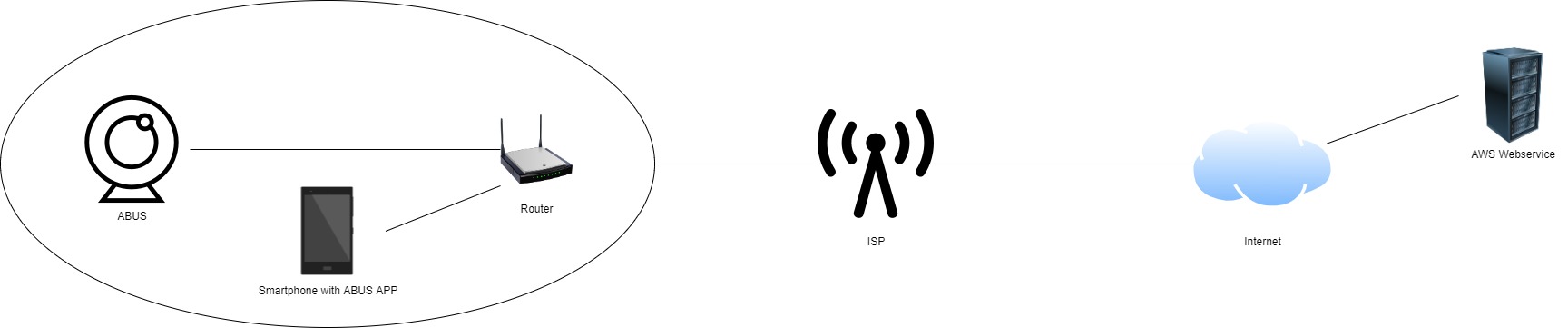 If the smartphone with the app is located inside the network and wants to connect to the camera, the main data stream stays inside the LAN.
If the smartphone with the app is located inside the network and wants to connect to the camera, the main data stream stays inside the LAN.
- Smartphone located outside Network:
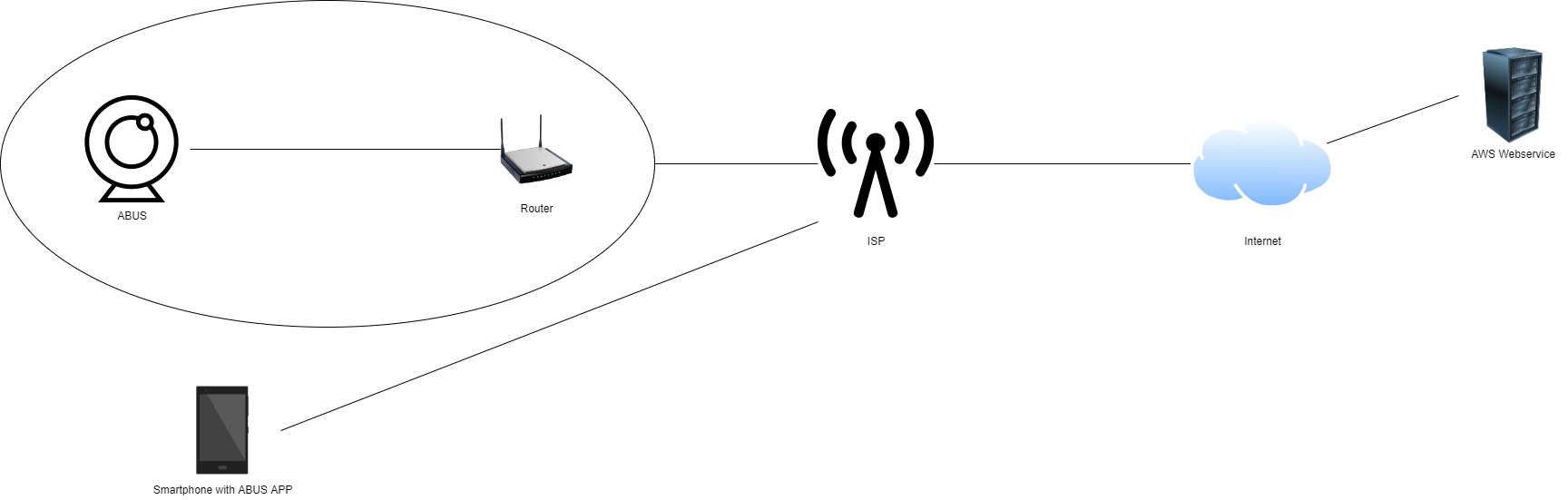 If the smartphone with the app is located outside the network and wants to connect to the camera, the main data stream gets hosted to an AWS Cloud Server where the App fetches the data.
If the smartphone with the app is located outside the network and wants to connect to the camera, the main data stream gets hosted to an AWS Cloud Server where the App fetches the data.
Exploitation
Euer part :)
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)