Information Gathering Tools
Summary
This is a draft. Comparing various available information gathering tools in Kali and comparing differences to ParrotOS. This document is NOT a documentation of the tools, it is merely a comparison and practical evaluation of the tools for an average security specialist or a security newbie wanting to start using the tools.
Requirements
- Operating system: Kali Linux 2021.1 amd64, Parrot Security 4.10 amd64
Disclaimer: all possible examples and tests done have been done in VMWare in a Kali Linux and ParrotOS VM.
Tools
Spiderfoot
This is a reconnaissance framework that uses many modules for information gathering, working on the OSINT principle. You can access a GUI by starting the framework on a port on localhost and accessing that address via web browser once it starts:
$ spiderfoot -l 127.0.0.1:5001
You can then set up a new scan, where you would give the program a target: this can be a domain/sub-domain name, IPv4 or IPv6 address, hostname, subnet, ASN, e-mail address, phone number, a person's actual name or username. This gives a really wide spectrum on options, some of which will be demonstrated below.
scan www.fh-campuswien.ac.at for a full scan, where you "get anything and everything about the target":
Execution takes a fairly long time, depending on the size of the target and the information available on the internet to that target. This specific inquiry took several hours to complete and collect all information.
Results:
Legion
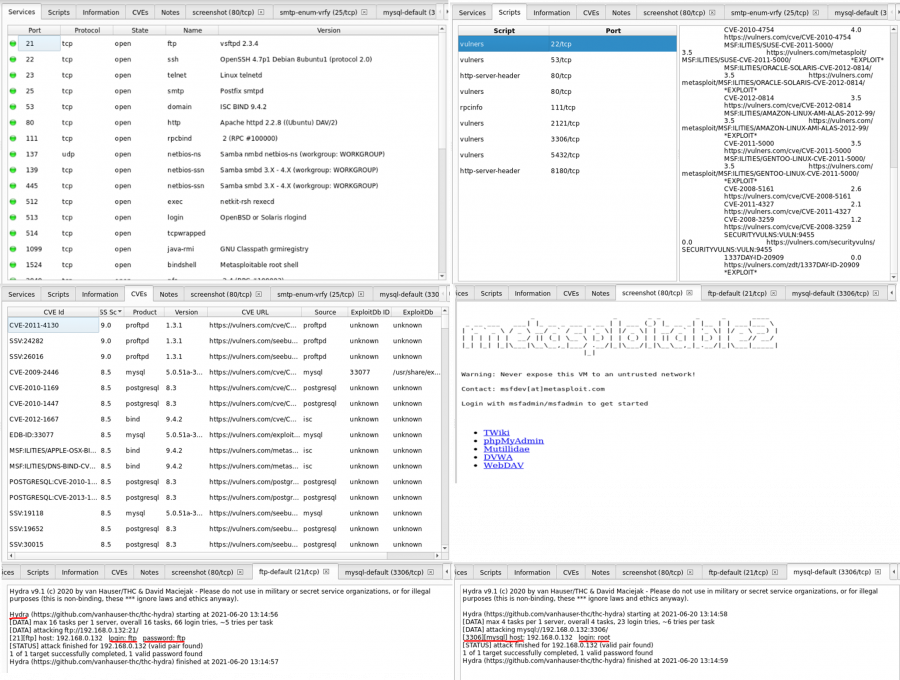
Legion is a GUI tool, a network penetration testing framework, that offers many options. It automatically detects CVEs and provides nmap, Vulners, whataweb, webslayer, sslyzer, SMBenum, dirbuster, nikto, Hydra and other additional scripts. Its execution takes up to a couple of minutes. A demonstration:
scan www.fh-campuswien.ac.at
No CVEs have been found.
Below is a comparison with the Metasploitable2 machine that can be found in the same subnet, so that it is clear how the vulnerabilities are shown in an actual weak system:
It is safe to say that it is a very powerful and useful tool, also very user friendly and quite fast. Maybe not the best for domains in the internet because it won't offer much more information than nmap and whois lookup, but when you look at the metasploitable output, so a scan of a server, you can see how much information is shown. The implementation of Hydra also gets you the cracked passwords in the vulnerabilities which is very useful.
DMitry
DMitry is a CLI tool to gather information about a host - possible subdomains, uptime information, tcp port scan, email addresses, whois lookups etc. It is mostly used to reveal information that exists through search engines about the owner or host of a web page, i.e. for social engineering attacks.
When using the portscan option, the results show less open ports than doing that same TCP scan with nmap.
DMitry:
HostIP:192.168.0.130 HostName: Gathered TCP Port information for 192.168.0.130 Port State 23/tcp open Portscan Finished: Scanned 150 ports, 148 ports were in state closed
Nmap:
Nmap scan report for 192.168.0.130 Host is up (0.20s latency). Not shown: 996 closed ports PORT STATE SERVICE 23/tcp open telnet 554/tcp open rtsp 843/tcp open unknown 5001/tcp open commplex-link MAC Address: 7C:DD:90:AF:4E:7D (Shenzhen Ogemray Technology) Nmap done: 1 IP address (1 host up) scanned in 2.33 seconds
To find out information about a domain, you need either the IP or the domain same.
Whois lookup on the other hand gets you some nice useful results. Below is an example of using dmitry -w www.fh-campuswien.ac.at on the college website of FH Campus Wien www.fh-campuswien.ac.at, and it just goes to show that it is exactly the same output as if you were to type whois fh-campuswien.ac.at
HostIP:91.213.77.62 HostName:www.fh-campuswien.ac.at Gathered Inic-whois information for fh-campuswien.ac.at --------------------------------- domain: fh-campuswien.ac.at registrar: registrant: FCW1942152-NICAT admin-c: tech-c: NLTU11579014-NICAT nserver: ns.nextlayer.at remarks: 81.16.150.30 nserver: ns2.nextlayer.at remarks: 81.16.151.30 changed: 20171003 19:16:08 source: AT-DOM personname: organization: fh campus wien street address: Favoritenstrasse 226 postal code: A-1100 city: Vienna country: Austria phone: +43160668771000 fax-no: +43160668771009 e-mail: office@fh-campuswien.ac.at nic-hdl: FCW1942152-NICAT changed: 20100323 17:12:46 source: AT-DOM personname: Hostmaster Hostmaster organization: next layer Telekommunikationsdienstleistungs- und BeratungsGmbH street address: Mariahilfer Guertel 37- 7 postal code: 1150 city: Vienna country: Austria phone: +43517649 e-mail: hostmaster@nextlayer.at nic-hdl: NLTU11579014-NICAT changed: 20170929 13:17:54 source: AT-DOM
Overall a nice tool, useful for beginners who don't have experience with the basic tools yet. However to an experienced IT Security specialist, the tools that DMitry is based on, like nmap and whois would be the better choice to use here, since they just offer you the same output. One drawback however is that you need to install whois separately, whilst DMitry will be in the preinstalled set of tools. When it comes to portscan, it offers pretty insufficient results in DMitry.
This tool is fairly outdated nowadays, although it used to be very good a few years ago. Now there are better alternatives.
Nmap
Nmap is known to be a very powerful tool for information gathering and vulnerability scanning. It offers loads of options, offering for example for host discovery, scans (TCP, UDP, IP...), service/version detection, OS detection, firewalls/IDS evasion and spoofing, script scanning etc. Since this is not meant to be a full documentation of the tools, but rather an evaluation overview, compared to the other tools nmap is the one main tool that most of the other secondary tools are using and it is very powerful.
Recon-ng
Maltego
Netdiscover
Ike-scan
What's different in ParrotOS?
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)