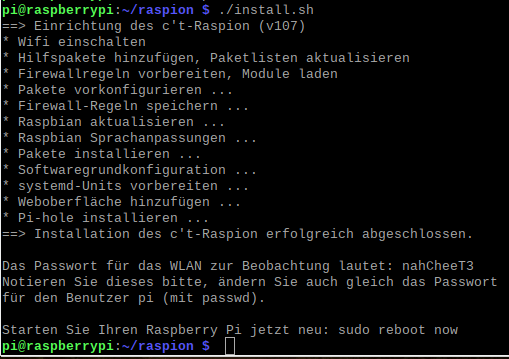
Install c't'-Raspion on Raspberry PI
Requirements
- Raspberry PI with Raspbian OS
- Internet connection
Description
Step 1: System Update
In the command line interface enter:
sudo apt-get update && sudo apt-get upgrade
Step 2: Download
Download the latest version of Raspion:
wget ct.de/s/x5Pm -O raspion.zip
Step 3: Installation
Unzip:
unzip raspion.zip
Install:
cd raspion ./install.sh or bash install.sh
At the end of the installation there is the wifi name and password of the c't-Raspion.
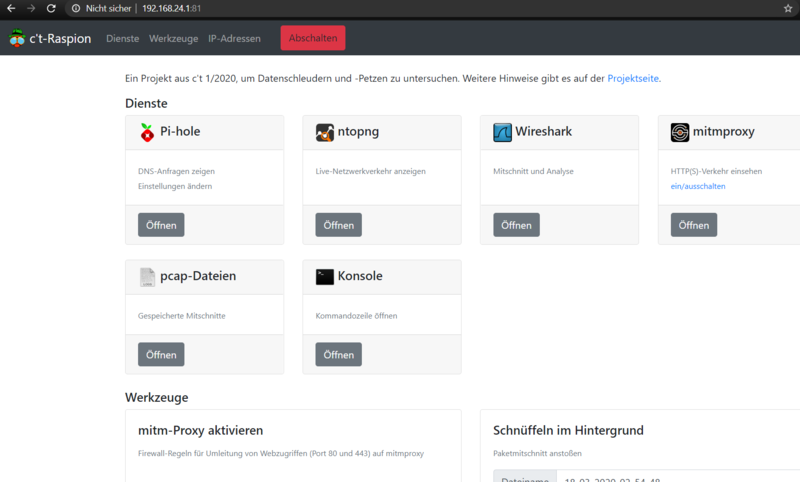
Launch c't-Raspion web interface
Atfer connecting to the wifi of the c't'-Raspion go to http://<ip-address of your Raspberry-PI>:81
Services of the c't-Raspion
Pi-hole
Pi-hole shows DNS-Requests. They can also be blocked.
ntopng
They include the involved communication partners, the network protocol and information on duration and volume. ntopng does not show the contents of the packages. But it analyses the flows and provides information about which application is communicating, such as Skype, BitTorrent etc., and provides statistics.
Wireshark
Wireshark offers a deeper analysis of the network traffic as ntopng. The program allows recording and analyzing network traffic down to the last bit and can be operated via browser as a special feature of c't-Raspion. The recorded network traffic will be saved in pcap-files.
mitmproxy
The mitm-Proxy can loop into the communication between the local and remote devices by the c't-Raspion redirecting all access from the internal network on TCP ports 80 and 443 to the mitm-Proxy. It takes the redirected accesses to port 8080 towards. The redirection is handled by firewall rules, which can be activated and deactivated as required by clicking in the c't-Raspion web interface.
Ikea Tradfri Setup Sniff
For testing purposes an iphone was cleaned as far as possible. All uninstalable services were erased and synchronization plans were deactivated. However iphones are not that good for this kind of tests because after all cleaning there were still some connections to apple servers.
To use pihole for capturing the dns queries of the Tradfri Gateway itself you may use an USB networkadapter or an external router as wifi bride. Otherwise you cannot use the Tradfri Gateway due to the lack of connection possibilities. As an workaround outside the Raspion software package classic arpspoofing was used.
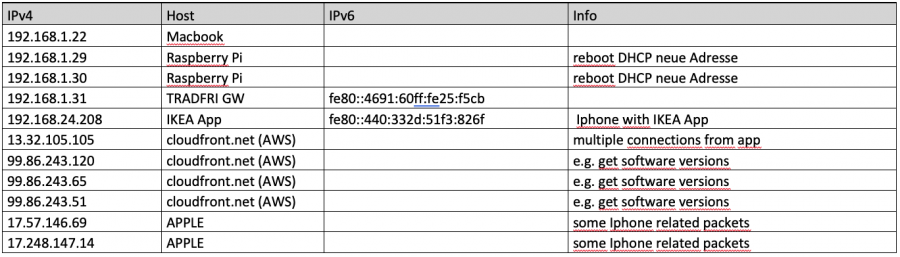
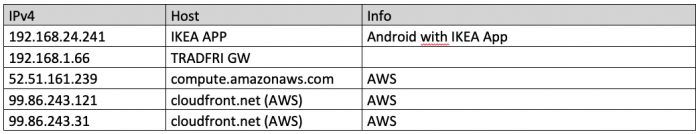
Preliminary overview IP addressess:
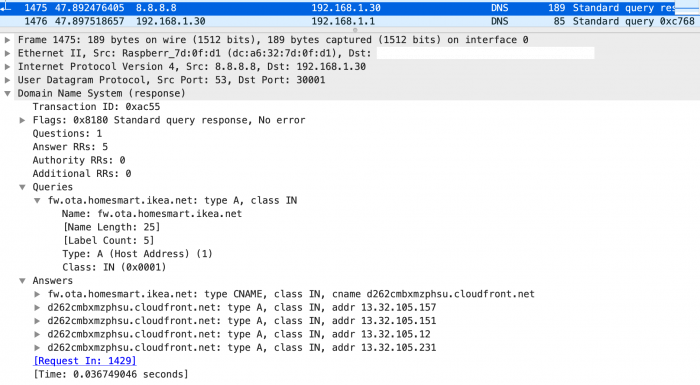
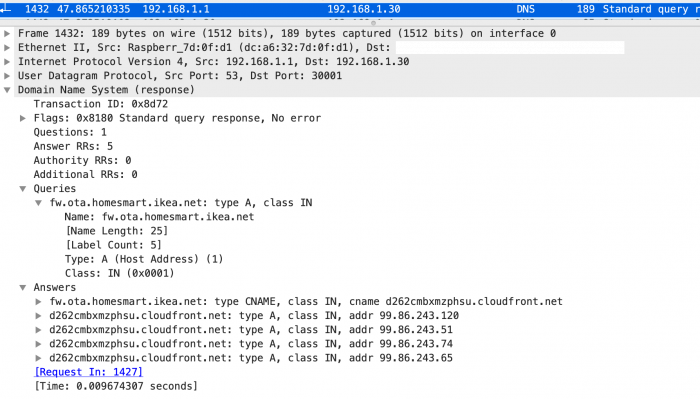
Immediately after power on the app is sending dns requests to get ip addresses for fw.ota.homesmart.ikea.net. In the dns answer the ip's to d262cmbxmzphsu.cloudfront.net were included which is an address belonging to amazons aws.
Also an http get request can be found:
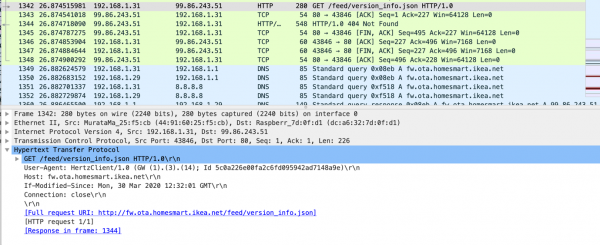
The data from fw.ota.homesmart.ikea.net/feed/version_info.json are not that spectacular. As the name implies it only consists of version information.
As soon as the Ikea Smart Home App starts the setup it tries to find a Tradfri Gateway with mDNS queries.
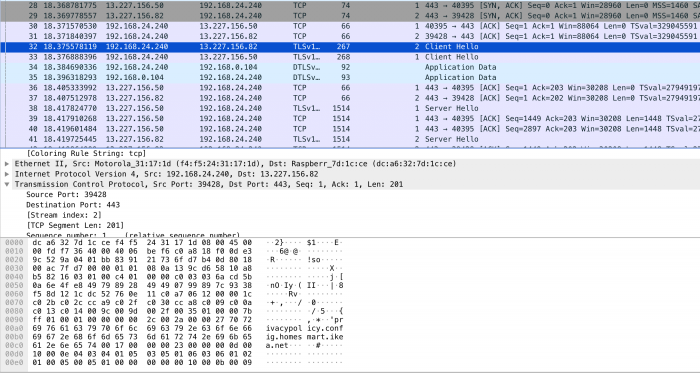
The mDNS queries are not forwarded through our pihole setup so this technique finding the Tradfri Gateway fails. The app itself provides another way to find the Tradfri Gateway by entering the ip address directly. After submitting the input the app finds the gateway and asks you to scan the QR code on the bottom side of the divce or to enter the security code which can be found near the QR code.
The QR code contains the security code which is used as the pre shared key of the DTLS connection. As soon as the app gets the security code the app and the gateway are initiating the DTLS connection. All applicationdata is send over this encrypted connection.
Same implies to connections of additional smart home devices: All data is sent over the encrypted connection.
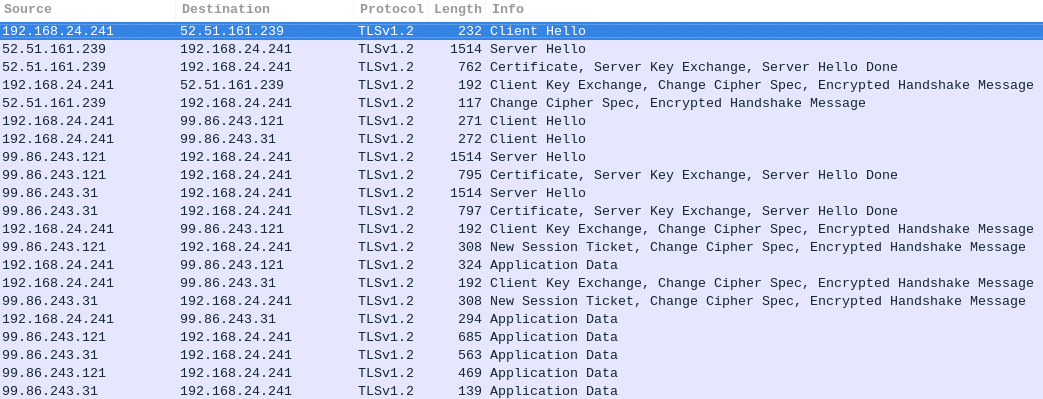
As far as the initial setup goes there are only a few connections to the internet. This connections are all from app to some aws cloud addresses. It seems this is relating to the setup of a new device:
Data Transmission when using TRADFRI
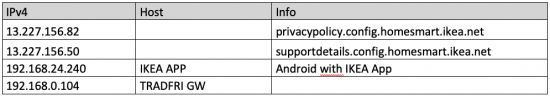
The IKEA TRADFRI Gateway was connected via LAN cable while the mobile phone running the IKEA app was connected wirelessly to the same network. Overview of IP addresses used:
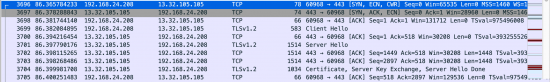
Wireshark was used to record the traffic (using arpspoof because the IKEA TRADFRI Gateway requires a LAN connection so it is not possible to just monitor the Raspion WiFi) which was then filtered.
It turns out that TRADFRI is rather well-behaved when it comes to sending data.
For the most part it uses encrypted (DTLS) communication internally between the Gateway and the mobile phone. To initially find the Gateway after opening the mobile app, an MDNS request is sent out via multicast (224.x.x.x).
However, 2 external connections or destinations could also be found:
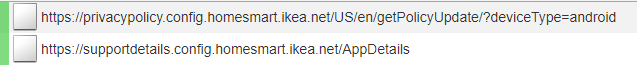
- IP address 13.227.156.82 / privacypolicy.config.homesmart.ikea.net (as the url indicates, this has the current policy one has to agree to before using the app)
- IP address 13.227.156.50 / supportdetails.config.homesmart.ikea.net (this is where the secure certificates are located, apparently).
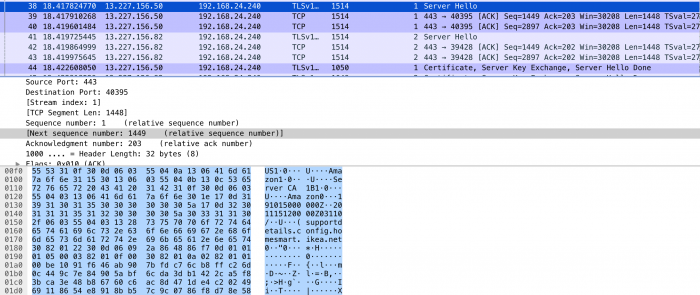
Wireshark caps
privacypolicy.config.homesmart.ikea.net Client Hello:
supportdetails.config.homesmart.ikea.net ServerHello:
Certificate Information
The Server Hello contains the information regarding the .cer and .crl:
http://ocsp.rootca1.amazontrust.com http://crt.rootca1.amazontrust.com/rootca1.cer http://crl.rootca1.amazontrust.com/rootca1.crl
Starfield Technologies, Inc.; Starfield Services Root Certificate Authority
Also:
http://crl.sca1b.amazontrust.com/sca1b.crl http://ocsp.sca1b.amazontrust.com http://crt.sca1b.amazontrust.com/sca1b.crt
That's pretty much it. We couldn't find any unwanted connections.
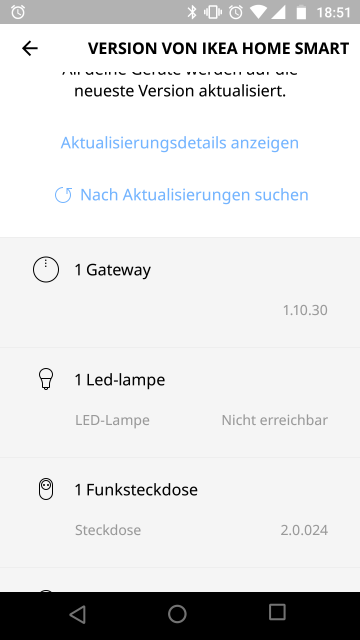
The app also checks for updates for the used devices, this is also indicated in the app when it happens, so this is very transparent. It is indicated in the app when an update is happening or when the app is checking for new updates as can be seen in the screenshot below. If a device happens to be unavailable, e.g. because it is currently disconnected/turned off, then the app does not report back the current version but instead says the device is unreachable ('Nicht erreichbar')
Kommunikation entschlüsseln
Bei diesem Versuch wird geschaut ob es möglich ist die Kommunikation, zwischen der IKEA App und dem IKEA Gateway mitzuhören. Nur mit einem Packet Sniffer ist dies nicht möglich, da die Kommunikation per DTLS verschlüsselt wird. Es kam zum Einsatz der MITM Proxy, welcher bei dem c’t-Raspion dabei ist.
IP overview:
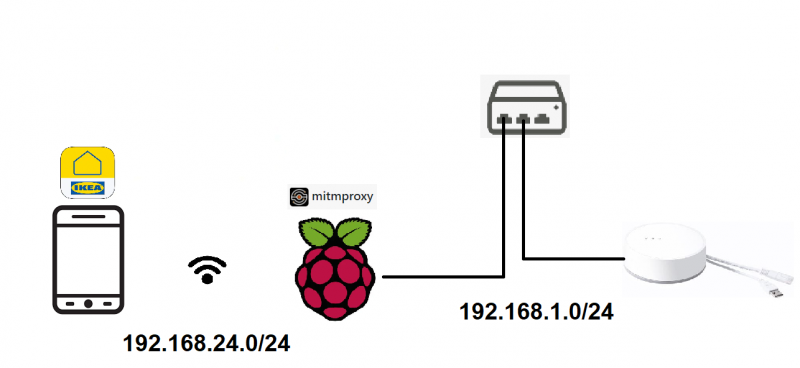
Aufbau
Android kann als eine Virtuelle Maschine betrieben werden, oder es kann auch ein Smart Phone benutzt werden welches die IKEA Smarthome App installiert hat. Wenn es als Virtuelle Maschine betrieben wird, ist drauf zu achten, dass der Bridge Mode benutzt wird, da dann die VM eine eigene IP erhält. Dies hat den Vorteil, dass man nur den Traffic analysieren muss, welcher von Android erzeugt wird und nicht dem des Host Systems. Um den MITM benutzten zu können, müssen die Zertifikaten zu dem Key-Store hinzugefügt werden. Dies kann getan werden in dem man die Website mitm.it ansurft. Ist man in dem richtigen Netzwerk sieht man folgendes Fenster.
Hier wählt man das richtige Betriebssystem und lädt die Zertifikate herunter.
Die offizielle Dokumentation findet man hier[1].
Findings
Beim Starten der App kann man in Wireshark stehen, dass der Handshake für die DTLS Verbindung durchgeführt wird.
Ebenso kann man beobachten, dass mehrere Verbindungen mit verschiedenen Servern nach draußen aufgebaut werden.
Die Nachrichten zu diesen Servern können durch den MITM entschlüsselt werden.
Beide Nachrichten beinhalten eine JSON-Datei.
{
"descriptionText": "That’s why we have updated the terms and conditions. Please agree below in order to continue. You can find the updated legal information in Settings or you can read more below.", "lastUpdatedTimestampCookie": 1568799375000, "lastUpdatedTimestampPP": 1568798738000, "lastUpdatedTimestampTnC": 1568798786000, "titleText": "We’ve changed the name of our app! "
} {
"versionCode": "44", "versionName": "1.11.3"
}
Im debug log kann beobachtet werden, dass weitere TLS Verbindung aufgebaut werden jedoch nicht entschlüsselt werden können.
192.168.24.241:59332: Client Handshake failed. The client may not trust the proxy's certificate for data.logentries.com. 192.168.24.241:59332: ClientHandshakeException('Cannot establish TLS with client (sni: data.logentries.com): TlsException("(-1, \'Unexpected EOF\')")') ::ffff:192.168.24.241:58971: serverdisconnect -> ('99.86.243.4', 443) 192.168.24.241:59332: clientdisconnect ::ffff:192.168.24.241:40204: serverdisconnect -> ('99.86.243.50', 443) 192.168.24.241:58971: clientdisconnect 192.168.24.241:40204: clientdisconnect 192.168.24.241:41657: clientconnect ::ffff:192.168.24.241:41657: Establish TLS with client 192.168.24.241:50453: clientconnect ::ffff:192.168.24.241:50453: serverconnect -> ('99.86.243.36', 443) 192.168.24.241:42222: clientconnect ::ffff:192.168.24.241:42222: serverconnect -> ('99.86.243.4', 443) ::ffff:192.168.24.241:42222: Establish TLS with server ::ffff:192.168.24.241:50453: Establish TLS with server ::ffff:192.168.24.241:42222: ALPN selected by server: - ::ffff:192.168.24.241:42222: Establish TLS with client ::ffff:192.168.24.241:50453: ALPN selected by server: - ::ffff:192.168.24.241:50453: Establish TLS with client ::ffff:192.168.24.241:42222: ALPN for client: b'http/1.1' ::ffff:192.168.24.241:50453: ALPN for client: b'http/1.1' ::ffff:192.168.24.241:50453: request -> Request(GET /US/en/getPolicyUpdate/?deviceType=android) ::ffff:192.168.24.241:42222: request -> Request(GET /AppDetails) ::ffff:192.168.24.241:42222: response -> Response(200 OK, application/json, 44b) ::ffff:192.168.24.241:50453: response -> Response(200 OK, application/json, 374b)
Die DTLS Verbindung zwischen der App und dem Gateway, erscheint jedoch nicht in dem Log des MITM.