KeeLoq
Summary
This documentation includes a brief introduction into KeeLoq and pentesting with the PandwaRF Rogue Pro on garage doors.
Requirements
- PandwaRF Rogue Pro
- PandwaRF App for Android (updated Android Version)
- Kaiju Gate Openers Pack (Pro License)
Description
KeeLoq is a lightweight block cipher owned by Microchip and it was invented in the 1980’s at the South-African company Nanoteq Ltd. Keeloq is implemented in a wide range of security applications. It is widely used as a remote key-less entry system. A remote keyless entry is an electronic access system that can be controlled from the distance, which means remote.
Registers
A register in general is a device which is used to store information.
Keeloq consists of two different registers:
- 64 bit key register – Circular-Shift Register and
- 32 bit text register – Nonlinear-Feedback-Shift Register.
Circular-Shift Registers
The information and data is stored in the format of multiple bits. The transformation of these information is made with the help of shift registers. Circular-shift registers calculate the bits of the register around the two ends without any loss.
Nonlinear-Feedback-Shift Register
A nonlinear-feedback shift register is a shift-register with an input bit that is a non-linear function of its previous state. It executes the single-bits for 528 rounds. The output sequence is an output sequence of the feedback shift register given by the function.
Block Ciphers
Keeloq is a lightweight block cipher for remote keyless entry systems. A block cipher is a method of data encryption, which uses a cryptographic key and algorithm to produce ciphertext. The block cipher processes fixed-size blocks at once, as alternate to a stream cipher, which encrypts data one bit at a time. Most modern block ciphers are invented to encrypt data in fixed-size blocks of either 64 or 128 bits. A block cipher uses a symmetric key to encrypt and decrypt a block of data. Additionally,it requires an initialization vector which is added to the input plaintext in order to increase the keyspace of the cipher and make it more difficult to use brute force to break the key. Block ciphers are built in the ’Feistel’ cipher structure. Block cipher has a specific number of rounds and keys for generating ciphertext.
Protocols
Keeloq consists of two different protocols:
- Hopping Code and
- Identification Friend or Foe (IFF).
Hopping Code
When hopping code is used, the code transmitted from the transmitter to the receiver is unique every time. At the core of this code hopping technology is a counter that increments with each button press. The en- and the decoder share a 16-bit synchronized counter value and a 64-bit symmetric key. The encoder encrypts the next counter value for authentication and sends it afterwards to the decoder. The decoder decrypts the message and verifies the received counter value if it is inside the open window of length 16.
Encoder Operation:
- Reaction on Buttonpress
- Encryption of the synchronization counter, discrimination value and button information
- Encryption using Hopping Code, thereby this code portion will change every transmission.
Decoder Operation:
- Learn and store information: Check value of the serial number, encoder decryption key, current synchronization counter value, manufacturer’s code. If two nonsequential codes were received or if two codes were not decoded within 30 seconds, the learning will be terminated. To enter the learning sequence, the transmitter is activated two times. After the learning a learn-status-string will be transmitted.
- Validation: For the validation, wait for the transmission, check the serial number, and compare it to determine if the transmitter is already learned.
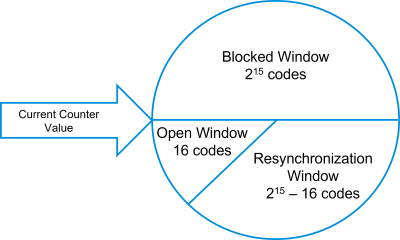
Synchronization of Encoder and Decoder:
- It might come to a desynchronization between encoder and decoder because the encoder can transmit while being out-of-range of the decoder.
- To counteract against this eventualities, different ranges of counter values are defined by the counter.
- In blocked Window the decoder does not perform anything because the decoder rejects the transmission.
- In resynchronization window the decoder stores the value and waits for the value increased by one.
- In open window the decoder accepts the transmission and performs the requisite function.
Identification Friend or Foe (IFF)
The IFF protocol is an effective anti-cloning technique and it is a challenge-response protocol. Thereby the main processor sends a large random number, called “challenge” (x), to the replaceable module. The replaceable module is a module which applies a formula to the challenge. Afterwards it computes a response and send it back to the main processor. The main processor compares the different values, the returned value and the computed value. The main processor accepts the new module as compatible (authenticated) if the formula which is used in the replaceable module is correct. The Keeloq IFF is based on the block cipher which is a 64-bit key encryption engine and on the 32-bit data blocks, which are represented as challenge and response.
Pentesting with PandwaRF Rogue Pro and Kaiju Gate Openers Pack
Step 1
- Install the application on your Android Phone. It can be downloaded from the Google Play Store.
- Open the Device and attach the antenna.
- Connect the PandwaRF via USB-C to your phone. The connection to the device should be established automatically, once it is connected to the phone.
- Open the application.
Step 2
- Open the Spectrum Analyser and press the button Start. Then use the gate opener and press the button to open the gate. The Spectrum Analyser captures the frequency and additional information.
- Open the RX/TX Radio Data and scroll down to the end. Press the button Capture and additionally a ctivate the gate opener several times until enough data is captured (it is seen on RX progress).
- The captured data can be seen on the end of the screen. Additionally the analyser knows the used pattern, which is KeeLoq (rolling code).
Step 3
- Click on "Analyze".
- Further choose "Fixed Code (local). There the information about the gate opener can be seen.
- To open the gate with PandwaRF Rogue Pro, click on "Rolling Code". The analysis of the rolling code should start with Kaiju automatically. It can last for several minutes.
- If Kaiju is finished with the analysis, several codes can be seen on the screen. This are the rolling codes, which are used to open the gate. The first one is marked as already used and cannot be taken to open the gate.
- Click on one subjacent codes and use it to open the garage door.
Side Notes:
- The execution of the analysis with Kaiju Gate Openers Pack is only possible at a few garage doors, it depends on the manufacturer and type.
- Since only the PandwaRF Rogue Pro is available, it is not possible to show the analysed rolling code after the analysis of Kaiju. To show the cracked encryption, the PandwaRF Rogue Gov with the Kaiju license would be necessary.
- Further, it is not possible to open car doors with the Kaiju Gate Openers Pack.
Used Hardware
- Android Smartphone
- PandwaRF Rogue Pro
References
- https://www.techtarget.com/whatis/definition/Remote-keyless-entry-RKE
- Nicolas T. Courtois. Self-similarity attacks on block ciphers and application to keeloq. In Cryptography and Security: From Theory to Applications, pages 55–66, 2012. 17, 18
- Steven Dawson. Code hopping decoder using a pic16c56. In Microchip, AN661, pages 2–6. 13
- Lucio Di Jasio. Using keeloq® to validate subsystem compatibility. In Microchip, AN827, pages 1–4. 14, 15, 26
- Sushil Jajodia Henk C.A. van Tilborg. Keeloq. In Encyclopedia of Cryptography and Security, page 671–673, 2011. 1, 2
- Sushil Jajodia Henk C.A. van Tilborg. Keeloq. In Encyclopedia of Cryptography and Security, pages 846–848, 2011. 4
- Microchip. Keeloq® code hopping decoder. In Microchip, HCS515, pages 2–6. 8, 10, 11, 12, 13, 26
- Microchip. Keeloq® code hopping encoder. In Microchip, HCS301, pages 4–16. 7, 8, 9, 13, 26
- Oleksandr Potii, Nikolay Poluyanenko, Igor Stelnyk, Iryna Revak, Sergii Kavun, and Tetiana Kuznetsova. Nonlinear-feedback shift registers for stream ciphers. In 2019 IEEE 2nd Ukraine Conference on Electrical and Computer Engineering (UKRCON), pages 906–911, 2019. 3
- Tomasz Rachwalik, Janusz Szmidt, Robert Wicik, and Janusz Zab locki. Generation of nonlinear feedback shift registers with special-purpose hardware. In 2012 Military Communications and Information Systems Conference (MCC), pages 1–4, 2012. 3, 26
- Christian Toma. Introduction to ultimate keeloq® technology. In Microchip, AN1683, pages 2–17. 7, 8