Difference between revisions of "Lightbulb Worm"
(Added the reference) |
|||
| (60 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
== What is a Lightbulb Worm? == | |||
The Lightbulb Worm is a construct that results from the research and attacks done by Colin O'Flynn, Eyal Ronen, Adi Shamir, and Achi-Or Weingarten. | |||
They provide the ingredients of the first worm that affects smart lighting systems. | |||
The | The worm has the power to spread only through physical proximity and would also be able to destroy lightbulbs permanently. It only takes one infected lightbulb to be installed, and the worm can spread - through its ZigBee wireless connectivity - directly to the physical neighbors of this lamp. These newly infected lamps would again infect all their neighbor lamps. | ||
That leads to a massive chain reaction that spreads in an epidemic fashion and attacks whole cities. The critical mass to infect all lightbulbs within a urban area like Paris was estimated to around 15.000 lightbulbs. <ref name="ronenarticle"/> | |||
== Philips Hue and Zigbee Light Link == | |||
The | The research and experiments of constructing the lightbulb worm have been done by using Philips Hue smart lighting systems and exploiting the implementation of their inbuilt ZigBee Light Link Protocol and firmware update mechanisms. | ||
= | The Philips Hue smart lamp system works as follows: | ||
The lightbulbs are connected to a bridge device which creates a network the lightbulbs can join. The bridge controls all the lamps and also contains an IP link. Via the Router, it is connected to the Internet through which you can control your system with the Philips Hue Lightning App. <ref name="ronenpaper"/> | |||
[[File:PhilipsHue.jpg|thumb|none|600px|Philips Hue and ZLL Architecture <ref name="ronenpaper"/>]] | |||
Philips Hue lamps communicate with their controllers through the Zigbee protocol and use the ZigBee Light Link protocol. <ref name="ronenpaper"/> | |||
The ZigBee Light Link protocol is standardized by the ZigBee Alliance and is a very popular standard in the lighting industry because it provides network flexibility and scalability. | |||
It also offers high interoperability between products from different vendors. | |||
To enable high interoperability, the Touchlink Commissioning protocol is used. It makes the installation of the light bulbs very easy and intuitive. <ref name="wan13/> | |||
The Touchlink commissioning protocol creates PANs (Personal Area Networks) and directs every new device placed in proximity to a specific bridge to join the PAN. | |||
The new device receives an encryption key that is used to encrypt and authenticate messages within the PAN. | |||
This encryption key is unique for every PAN and encrypted by a “Master key." | |||
This “Master key" is a secret key, but it is used and stored on every ZLL certifed | |||
product. In the case for Philipps Hue products the same AES-CCM key was used on every device. This resulted in the fact that the team was able to send faulty OTA updates to each device since using the same key on each device does not offer any protection if this key is known to the attacker. | |||
The Touchlink protocol provides two message types with which the state of a lightbulb can be changed: | |||
The | |||
1. Reset to factory new request: If the target device receives this message | |||
with a valid Transaction ID, it is reset to a factory new state, and all Network information and keys are deleted. | |||
; | 2. Join (or start) network request: With this message, the device is instructed to join | ||
: | the PAN. <ref name="ronenpaper"/> | ||
== Security Features of Philips Hue == | |||
'''Encryption Mechanisms''' – see [[#Philips Hue and Zigbee Light Link|Philips Hue and ZigBee Light Link]] | |||
'''Proximity Check''' - prevents a takeover of lightbulbs in the nearest neighborhood. | |||
:The proximity check ensures that the initiator is physically very close to the target. | |||
:It must be passed successfully to connect lamps to the bridge. | |||
:Without the proximity check, any initiator that owns the ZLL master key could instruct lightbulbs to reset to a factory new state or join a new PAN. <ref name="ronenpaper"/> | |||
== Ingredients of the Lightbulb Worm == | |||
;Persistence of code execution on the lamps to take over the control of the lamps | |||
:The researchers achieved the Persistence of Code Execution by exploiting the (OTA - Over the Air) update mechanisms of the Philips Hue. And they did that by reverse engineering. | |||
:The reverse engineering was possible because the system was vulnerable to side channel analysis and also some parts of the encryption was already known. | |||
:So the team managed to upload selfwritten firmware on the lamps instead of the original firmware.<ref name="ronenpaper"/> | |||
;Lateral movement - the worm should spread automatically through proximity | |||
:The lateral movement had been achieved by passing the proximity check. | |||
:That was possible by exploiting the software implementation of the Touchlink protocol and a feature of the ZLL protocol. | |||
:ZLL devices should also be able to join other ZigBee networks, where no ZLL is used. When no ZLL is used, there is also no proximity check. | |||
:So they just had to set the lightbulbs to a Factory New state and make the lightbulbs actively search for ZigBee networks and are open to connection. | |||
:Setting them to a Factory New state was possible due to a software bug which could have been found with negative testing during the Zigbee certification process. <ref name="ronenpaper"/> | |||
== Security Issues of the Philips Hue System == | |||
* Use of a '''single symmetric encryption key''' shared across many devices to protect the firmware update process | |||
* The attacks were also possible because the hardware is '''vulnerable to side-channel analysis''' | |||
* And also, the '''bugs and errors in the implementation of protocols''' (designed to prevent long-range take-over attacks) <ref name="ronenpaper"/> | |||
== Estimated Damage == | |||
To estimate the actual damage of such an attack, the researchers calculated how many smart lamps would have to be installed to launch the attack. | |||
Result: Paris, the critical mass would be around 15,000 lamps (installed within a distance of about 100 meters). | |||
That is not an unrealistic amount of lamps concerning the popularity of Philips Hue. | |||
So the researchers assumed that cities might be already vulnerable to such attacks. <ref name="ronenpaper"/> | |||
This attack is even more remarkable because there is no internet communication used. | |||
The worm only spreads through physical proximity and is independent of established networking structures – so once created, the worm is probably impossible to stop. | |||
System administrators usually try to stop such an attack by isolating subnetworks from each other, which in this case would not be possible because only ZigBee communication is used, which is not monitored or protected. | |||
Also, locating the source of the attack and also detecting the attack itself would be very difficult. <ref name="ronenpaper"/> | |||
== Possible Attacks == | |||
;Bricking Attacks | |||
:Unlike usual DoS irreversible, all devices would have to be replaced | |||
;Wireless Network Jamming | ;Wireless Network Jamming | ||
: | :ZigBee runs over the IEEE 802.15.4 standard, which uses the 2.4 GHz, license-free band (continuous wave signal from 'test mode' could overlap other channels) | ||
;Data infiltration and exfiltration | ;Data infiltration and exfiltration | ||
: | ;Affect peoples health | ||
:The light can be programmed in such a blinking rate which causes epileptic seizures | |||
:The LEDs can also be driven at frequencies that are creating discomfort in humans <ref name="ronenpaper"/> | |||
== Countermeasures == | == Countermeasures == | ||
* Unique keys per lightbulb | |||
: | |||
: | * Asymetric cryptography for software verification | ||
* Reducing the amount of damage a leaked key might be able to cause | |||
* Negative testing to avoid implementation bugs <ref name="ronenpaper"/> | |||
== Zigbee Protocol Overview == | |||
* ZigBee is a low-power, low-data-rate wireless communication protocol. | |||
* Used in smart homes, industrial automation, and sensor networks. | |||
* Operates in 2.4 GHz frequency band with mesh network communication. | |||
== Zigbee Architecture == | |||
* Architecture includes Application, Application Interface, Security, Network, Medium Access Control, and Physical Layer. | |||
== Zigbee Addressing and Frames == | |||
* Uses short (16-bit) and long (64-bit) addresses for device identification. | |||
* Packet-based communication with data frames, acknowledgment frames, and command frames. | |||
== Zigbee Security and Sniffing == | |||
* Features encryption and authentication for secure device communication. | |||
* Tools like Wireshark and nRF52840 dongle mentioned for Zigbee sniffing. | |||
=== Initial Steps for Experimentation === | |||
* Details on using nRF Connect for Desktop, firmware installation, and programming the nRF52840 Dongle. | |||
* Installation of nRF Sniffer capture plugin in Wireshark discussed. | |||
* [https://www.nordicsemi.com/Products/Development-hardware/nrf52840-dongle nRF52840 Dongle - Nordic Semiconductor] | |||
* [https://github.com/NordicSemiconductor/nRF-Sniffer-for-802.15.4 nRF Sniffer for 802.15.4 - GitHub Repository] | |||
* [https://infocenter.nordicsemi.com/index.jsp?topic=%2Fug_sniffer_802154%2FUG%2Fsniffer_802154%2Fintro_802154.html nRF Sniffer for 802.15.4 Introduction - Nordic Semiconductor Infocenter] | |||
== | == References == | ||
<references> | |||
<ref name="ronenarticle">Eyal Ronen, Colin O'Flynn, Adi Shamir, and Achi Or Weingarten. IoT Goes Nuclear: Creating a ZigBee Chain Reaction. In Proceedings – IEEE Symposium on Security and Privacy, 2017 </ref> | |||
<ref name="wan13"> Jianfeng Wang. Zigbee light link and its applicationss. IEEE Wireless Communications, 2013 </ref> | |||
<ref name="ronenpaper"> Eyal Ronen, Adi Shamir, Achi Or Weingarten, and Colin O‘Flynn. IoT Goes Nuclear: Creating a Zigbee Chain Reaction. IEEE Security and Privacy, 2018 </ref> | |||
</references> | |||
== Further Information == | |||
* Colin O'Flynn. A LIGHTBULB WORM? Details of the Philips Hue Smart Lighting Design. In Black Hat USA, 2016 | |||
[[Category:Documentation]] | [[Category:Documentation]] | ||
[[Category:Basic]] | [[Category:Basic]] | ||
Latest revision as of 19:40, 7 January 2024
What is a Lightbulb Worm?
The Lightbulb Worm is a construct that results from the research and attacks done by Colin O'Flynn, Eyal Ronen, Adi Shamir, and Achi-Or Weingarten. They provide the ingredients of the first worm that affects smart lighting systems.
The worm has the power to spread only through physical proximity and would also be able to destroy lightbulbs permanently. It only takes one infected lightbulb to be installed, and the worm can spread - through its ZigBee wireless connectivity - directly to the physical neighbors of this lamp. These newly infected lamps would again infect all their neighbor lamps. That leads to a massive chain reaction that spreads in an epidemic fashion and attacks whole cities. The critical mass to infect all lightbulbs within a urban area like Paris was estimated to around 15.000 lightbulbs. [1]
Philips Hue and Zigbee Light Link
The research and experiments of constructing the lightbulb worm have been done by using Philips Hue smart lighting systems and exploiting the implementation of their inbuilt ZigBee Light Link Protocol and firmware update mechanisms.
The Philips Hue smart lamp system works as follows: The lightbulbs are connected to a bridge device which creates a network the lightbulbs can join. The bridge controls all the lamps and also contains an IP link. Via the Router, it is connected to the Internet through which you can control your system with the Philips Hue Lightning App. [2]
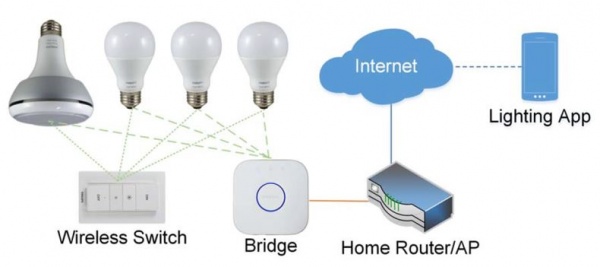
Philips Hue lamps communicate with their controllers through the Zigbee protocol and use the ZigBee Light Link protocol. [2]
The ZigBee Light Link protocol is standardized by the ZigBee Alliance and is a very popular standard in the lighting industry because it provides network flexibility and scalability. It also offers high interoperability between products from different vendors. To enable high interoperability, the Touchlink Commissioning protocol is used. It makes the installation of the light bulbs very easy and intuitive. [3]
The Touchlink commissioning protocol creates PANs (Personal Area Networks) and directs every new device placed in proximity to a specific bridge to join the PAN. The new device receives an encryption key that is used to encrypt and authenticate messages within the PAN. This encryption key is unique for every PAN and encrypted by a “Master key."
This “Master key" is a secret key, but it is used and stored on every ZLL certifed product. In the case for Philipps Hue products the same AES-CCM key was used on every device. This resulted in the fact that the team was able to send faulty OTA updates to each device since using the same key on each device does not offer any protection if this key is known to the attacker.
The Touchlink protocol provides two message types with which the state of a lightbulb can be changed:
1. Reset to factory new request: If the target device receives this message with a valid Transaction ID, it is reset to a factory new state, and all Network information and keys are deleted.
2. Join (or start) network request: With this message, the device is instructed to join the PAN. [2]
Security Features of Philips Hue
Encryption Mechanisms – see Philips Hue and ZigBee Light Link
Proximity Check - prevents a takeover of lightbulbs in the nearest neighborhood.
- The proximity check ensures that the initiator is physically very close to the target.
- It must be passed successfully to connect lamps to the bridge.
- Without the proximity check, any initiator that owns the ZLL master key could instruct lightbulbs to reset to a factory new state or join a new PAN. [2]
Ingredients of the Lightbulb Worm
- Persistence of code execution on the lamps to take over the control of the lamps
- The researchers achieved the Persistence of Code Execution by exploiting the (OTA - Over the Air) update mechanisms of the Philips Hue. And they did that by reverse engineering.
- The reverse engineering was possible because the system was vulnerable to side channel analysis and also some parts of the encryption was already known.
- So the team managed to upload selfwritten firmware on the lamps instead of the original firmware.[2]
- Lateral movement - the worm should spread automatically through proximity
- The lateral movement had been achieved by passing the proximity check.
- That was possible by exploiting the software implementation of the Touchlink protocol and a feature of the ZLL protocol.
- ZLL devices should also be able to join other ZigBee networks, where no ZLL is used. When no ZLL is used, there is also no proximity check.
- So they just had to set the lightbulbs to a Factory New state and make the lightbulbs actively search for ZigBee networks and are open to connection.
- Setting them to a Factory New state was possible due to a software bug which could have been found with negative testing during the Zigbee certification process. [2]
Security Issues of the Philips Hue System
- Use of a single symmetric encryption key shared across many devices to protect the firmware update process
- The attacks were also possible because the hardware is vulnerable to side-channel analysis
- And also, the bugs and errors in the implementation of protocols (designed to prevent long-range take-over attacks) [2]
Estimated Damage
To estimate the actual damage of such an attack, the researchers calculated how many smart lamps would have to be installed to launch the attack.
Result: Paris, the critical mass would be around 15,000 lamps (installed within a distance of about 100 meters). That is not an unrealistic amount of lamps concerning the popularity of Philips Hue. So the researchers assumed that cities might be already vulnerable to such attacks. [2]
This attack is even more remarkable because there is no internet communication used.
The worm only spreads through physical proximity and is independent of established networking structures – so once created, the worm is probably impossible to stop.
System administrators usually try to stop such an attack by isolating subnetworks from each other, which in this case would not be possible because only ZigBee communication is used, which is not monitored or protected.
Also, locating the source of the attack and also detecting the attack itself would be very difficult. [2]
Possible Attacks
- Bricking Attacks
- Unlike usual DoS irreversible, all devices would have to be replaced
- Wireless Network Jamming
- ZigBee runs over the IEEE 802.15.4 standard, which uses the 2.4 GHz, license-free band (continuous wave signal from 'test mode' could overlap other channels)
- Data infiltration and exfiltration
- Affect peoples health
- The light can be programmed in such a blinking rate which causes epileptic seizures
- The LEDs can also be driven at frequencies that are creating discomfort in humans [2]
Countermeasures
- Unique keys per lightbulb
- Asymetric cryptography for software verification
- Reducing the amount of damage a leaked key might be able to cause
- Negative testing to avoid implementation bugs [2]
Zigbee Protocol Overview
- ZigBee is a low-power, low-data-rate wireless communication protocol.
- Used in smart homes, industrial automation, and sensor networks.
- Operates in 2.4 GHz frequency band with mesh network communication.
Zigbee Architecture
- Architecture includes Application, Application Interface, Security, Network, Medium Access Control, and Physical Layer.
Zigbee Addressing and Frames
- Uses short (16-bit) and long (64-bit) addresses for device identification.
- Packet-based communication with data frames, acknowledgment frames, and command frames.
Zigbee Security and Sniffing
- Features encryption and authentication for secure device communication.
- Tools like Wireshark and nRF52840 dongle mentioned for Zigbee sniffing.
Initial Steps for Experimentation
- Details on using nRF Connect for Desktop, firmware installation, and programming the nRF52840 Dongle.
- Installation of nRF Sniffer capture plugin in Wireshark discussed.
- nRF52840 Dongle - Nordic Semiconductor
- nRF Sniffer for 802.15.4 - GitHub Repository
- nRF Sniffer for 802.15.4 Introduction - Nordic Semiconductor Infocenter
References
- ↑ Eyal Ronen, Colin O'Flynn, Adi Shamir, and Achi Or Weingarten. IoT Goes Nuclear: Creating a ZigBee Chain Reaction. In Proceedings – IEEE Symposium on Security and Privacy, 2017
- ↑ 2.00 2.01 2.02 2.03 2.04 2.05 2.06 2.07 2.08 2.09 2.10 2.11 Eyal Ronen, Adi Shamir, Achi Or Weingarten, and Colin O‘Flynn. IoT Goes Nuclear: Creating a Zigbee Chain Reaction. IEEE Security and Privacy, 2018
- ↑ Jianfeng Wang. Zigbee light link and its applicationss. IEEE Wireless Communications, 2013
Further Information
- Colin O'Flynn. A LIGHTBULB WORM? Details of the Philips Hue Smart Lighting Design. In Black Hat USA, 2016