Difference between revisions of "Lightbulb Worm"
CRudlstorfer (talk | contribs) |
CRudlstorfer (talk | contribs) |
||
| Line 5: | Line 5: | ||
The worm has the power to spread only through physical proximity and would also be able to destroy lightbulbs permanently. It only takes one infected lightbulb to be installed, and the worm can spread - through its ZigBee wireless connectivity - directly to the physical neighbors of this lamp. These newly infected lamps would again infect all their neighbor lamps. | The worm has the power to spread only through physical proximity and would also be able to destroy lightbulbs permanently. It only takes one infected lightbulb to be installed, and the worm can spread - through its ZigBee wireless connectivity - directly to the physical neighbors of this lamp. These newly infected lamps would again infect all their neighbor lamps. | ||
That leads to a massive chain reaction that spreads in an epidemic fashion and attacks whole cities. <ref name=" | That leads to a massive chain reaction that spreads in an epidemic fashion and attacks whole cities. <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
| Line 15: | Line 15: | ||
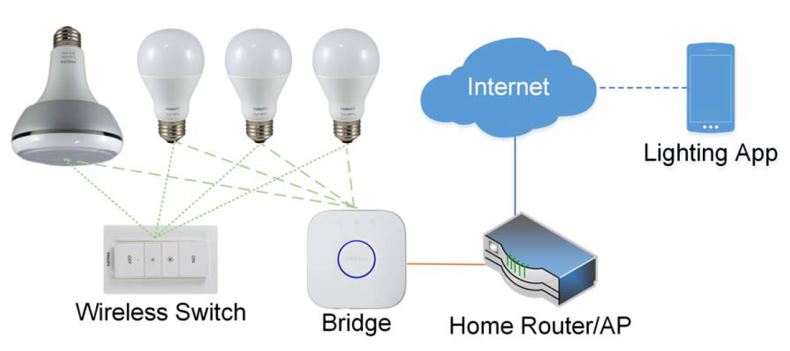
The lightbulbs are connected to a bridge device which creates a network the lightbulbs can join. The bridge controls all the lamps and also contains an IP link. Via the Router, it is connected to the Internet through which you can control your system with the Philips Hue Lightning App. <ref name="1"/> <ref name="2"/> <ref name="3"/> | The lightbulbs are connected to a bridge device which creates a network the lightbulbs can join. The bridge controls all the lamps and also contains an IP link. Via the Router, it is connected to the Internet through which you can control your system with the Philips Hue Lightning App. <ref name="1"/> <ref name="2"/> <ref name="3"/> | ||
[[File:PhilipsHue.jpg]] <ref name=" | [[File:PhilipsHue.jpg]] <ref name="ronenpaper"> | ||
Philips Hue lamps communicate with their controllers through the Zigbee protocol and use the ZigBee Light Link protocol. | Philips Hue lamps communicate with their controllers through the Zigbee protocol and use the ZigBee Light Link protocol. | ||
| Line 40: | Line 40: | ||
the PAN. | the PAN. | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== Security Features of Philips Hue == | == Security Features of Philips Hue == | ||
| Line 50: | Line 50: | ||
:Without the proximity check, any initiator that owns the ZLL master key could instruct lightbulbs to :reset to a factory new state or join a new PAN. | :Without the proximity check, any initiator that owns the ZLL master key could instruct lightbulbs to :reset to a factory new state or join a new PAN. | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== Ingredients of the Lightbulb Worm == | == Ingredients of the Lightbulb Worm == | ||
| Line 67: | Line 67: | ||
:So they just had to set the lightbulbs to a Factory New state and make the lightbulbs actively :search for ZigBee networks and are open to connection. | :So they just had to set the lightbulbs to a Factory New state and make the lightbulbs actively :search for ZigBee networks and are open to connection. | ||
:Setting them to a Factory New state was possible due to a software bug. | :Setting them to a Factory New state was possible due to a software bug. | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
| Line 78: | Line 78: | ||
- And also, the Bugs and Errors in the implementation of protocols (designed to prevent long-range take-over attacks) | - And also, the Bugs and Errors in the implementation of protocols (designed to prevent long-range take-over attacks) | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== Estimated Damage == | == Estimated Damage == | ||
| Line 96: | Line 96: | ||
Also, locating the source of the attack and also detecting the attack itself would be very difficult. | Also, locating the source of the attack and also detecting the attack itself would be very difficult. | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== Possible Attacks == | == Possible Attacks == | ||
| Line 109: | Line 109: | ||
:The LEDs can also be driven at frequencies that are creating discomfort in humans | :The LEDs can also be driven at frequencies that are creating discomfort in humans | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== Countermeasures == | == Countermeasures == | ||
| Line 121: | Line 121: | ||
- Negative testing to avoid implementation bugs | - Negative testing to avoid implementation bugs | ||
<ref name=" | <ref name="blackhat"/> <ref name="ronenarticle"/> <ref name="ronenpaper"/> | ||
== References == | == References == | ||
<references> | <references> | ||
<ref name=" | <ref name="blackhat"> | ||
Colin O'Flynn. A LIGHTBULB WORM? Details of the Philips Hue Smart Lighting Design. In Black Hat USA, 2016 | Colin O'Flynn. A LIGHTBULB WORM? Details of the Philips Hue Smart Lighting Design. In Black Hat USA, 2016 | ||
<ref name=" | <ref name="ronenarticle">Eyal Ronen, Colin O'Flynn, Adi Shamir, and Achi Or Weingarten. IoT Goes Nuclear: Creating a ZigBee Chain Reaction. In Proceedings – IEEE Symposium on Security and Privacy, 2017 </ref> | ||
<ref name=" | <ref name="ronenpaper"> Eyal Ronen, Adi Shamir, Achi Or Weingarten, and Colin O‘Flynn. IoT Goes Nuclear: Creating a Zigbee Chain Reaction. IEEE Security and Privacy, 2018 </ref> | ||
</references> | </references> | ||
Revision as of 16:35, 11 January 2022
What is a Lightbulb Worm?
The Lightbulb Worm is a construct that results from the research and attacks done by Colin O'Flynn, Eyal Ronen, Adi Shamir, and Achi-Or Weingarten. They provide the ingredients of the first worm that affects smart lighting systems.
The worm has the power to spread only through physical proximity and would also be able to destroy lightbulbs permanently. It only takes one infected lightbulb to be installed, and the worm can spread - through its ZigBee wireless connectivity - directly to the physical neighbors of this lamp. These newly infected lamps would again infect all their neighbor lamps. That leads to a massive chain reaction that spreads in an epidemic fashion and attacks whole cities. [1] [2] [3]
Philips Hue and Zigbee Light Link
The research and experiments of constructing the lightbulb worm have been done by using Philips Hue smart lighting systems and exploiting the implementation of their inbuilt ZigBee Light Link Protocol and firmware update mechanisms.
The Philips Hue smart lamp system works as follows:
The lightbulbs are connected to a bridge device which creates a network the lightbulbs can join. The bridge controls all the lamps and also contains an IP link. Via the Router, it is connected to the Internet through which you can control your system with the Philips Hue Lightning App. Cite error: Invalid <ref> tag; name cannot be a simple integer. Use a descriptive title Cite error: Invalid <ref> tag; name cannot be a simple integer. Use a descriptive title Cite error: Invalid <ref> tag; name cannot be a simple integer. Use a descriptive title
 Cite error: Closing
Cite error: Closing </ref> missing for <ref> tag
[3] </references>
- ↑ Cite error: Invalid
<ref>tag; no text was provided for refs namedblackhat - ↑ Cite error: Invalid
<ref>tag; no text was provided for refs namedronenarticle - ↑ 3.0 3.1 Eyal Ronen, Adi Shamir, Achi Or Weingarten, and Colin O‘Flynn. IoT Goes Nuclear: Creating a Zigbee Chain Reaction. IEEE Security and Privacy, 2018