Difference between revisions of "Lucky 13"
JSchwinger (talk | contribs) |
JSchwinger (talk | contribs) (Lucky 13 is a timing attack on TLS/DTLS discovered in 2012 by Nadhem AlFardan and Kenny Paterson.) |
||
| Line 1: | Line 1: | ||
== The | Lucky 13 is a timing attack on TLS/DTLS discovered in 2012 by Nadhem AlFardan and [http://www.isg.rhul.ac.uk/%7Ekp Kenny Paterson]. In 2013 they published their findings and released their [http://www.isg.rhul.ac.uk/tls/TLStiming.pdf whitepaper]. The attack is shown to only work on LAN and is hindered by noise on the network (unwanted traffic). | ||
To understand the attack, first explanation of a few concepts is needed. | |||
== Basics == | |||
Cipher Block Chaining (CBC) and MAC-then-encrypt are being used in the DTLS record protocol. | |||
=== Cipher Block Chaining (CBC) === | |||
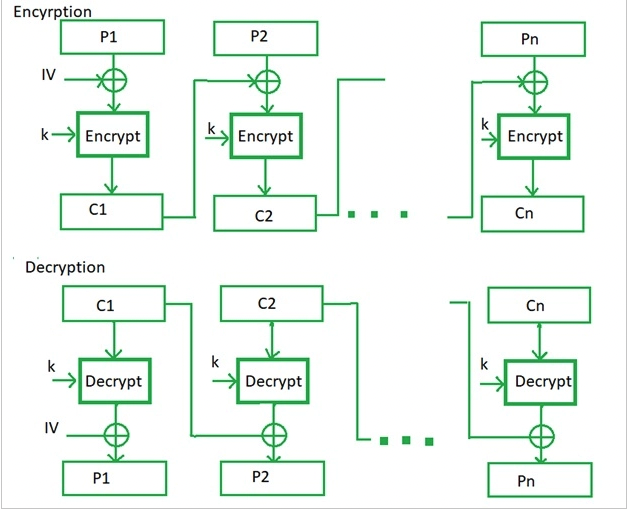
CBC is a method of encrypting plaintext. It takes a block of clear text and adds it (bit-by-bit) to the previous encryption. | |||
IV = Initialization Vector is a (pseudo)random sequence of characters added to an encryption key. The IV should be different for any two messages encrypted with the same cryptography key. | |||
First step is to divide the pain text into block size (size depends on underlying symmetric encryption algorithm). Plain text (<math>P_i</math>) and previous ciphertext (<math>\C_{i−1}</math>) are combined with an XOR operation. Then it gets encrypted with the key. ''Repeat''. | |||
In the first step we do not have any ciphertext (<math>C_i</math>) so we use the IV (initialization vector) for this one. | |||
<math>E</math> stands for the encryption process. | |||
This leaves us with this formula: | |||
<math>C_i = E(P_i \oplus C_{i-1})</math> | |||
[[File:CBC_example.png]] | |||
Revision as of 15:35, 21 December 2021
Lucky 13 is a timing attack on TLS/DTLS discovered in 2012 by Nadhem AlFardan and Kenny Paterson. In 2013 they published their findings and released their whitepaper. The attack is shown to only work on LAN and is hindered by noise on the network (unwanted traffic).
To understand the attack, first explanation of a few concepts is needed.
Basics
Cipher Block Chaining (CBC) and MAC-then-encrypt are being used in the DTLS record protocol.
Cipher Block Chaining (CBC)
CBC is a method of encrypting plaintext. It takes a block of clear text and adds it (bit-by-bit) to the previous encryption.
IV = Initialization Vector is a (pseudo)random sequence of characters added to an encryption key. The IV should be different for any two messages encrypted with the same cryptography key. First step is to divide the pain text into block size (size depends on underlying symmetric encryption algorithm). Plain text () and previous ciphertext (Failed to parse (MathML with SVG or PNG fallback (recommended for modern browsers and accessibility tools): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle \C_{i−1}} ) are combined with an XOR operation. Then it gets encrypted with the key. Repeat. In the first step we do not have any ciphertext () so we use the IV (initialization vector) for this one. stands for the encryption process.
This leaves us with this formula: