Difference between revisions of "Lucky 13"
JSchwinger (talk | contribs) (Lucky 13 is a timing attack on TLS/DTLS discovered in 2012 by Nadhem AlFardan and Kenny Paterson.) |
JSchwinger (talk | contribs) |
||
| Line 21: | Line 21: | ||
[[File:CBC_example.png]] | [[File:CBC_example.png]] | ||
=== MAC-then-encrypt === | |||
MAC provides '''message authentication'''. Sender and receiver share a symmetric key. | |||
* The sender uses some publicly known MAC algorithm, inputs the message and the secret key K and produces a MAC value. | |||
* Send it. | |||
* On receipt of the message and the MAC, the receiver feeds the received message and the shared secret key K into the MAC algorithm and re-computes the MAC value. | |||
* The receiver now checks equality of freshly computed MAC with the MAC received from the sender. If they match, then the receiver accepts the message and assures himself that the message has been sent by the intended sender. | |||
[[File:MAC-then-encrypt.png]] | |||
== DTLS Record Protocol == | |||
[[File:DTLS Protocol.png]] | |||
=== Encryption === | |||
<math></math> | |||
<math>R</math> = individual record (payload) | |||
MAC calculation: | |||
<math>T = \mathtt{SQN}||\mathtt{HDR}||R</math> | |||
SQN and HDR are prepended and are 13 bytes long: | |||
* SQN = 8-byte | |||
* HDR = 5-byte | |||
** version field = 2-byte | |||
** type = 1-byte | |||
** length = 2-byte | |||
<math>T</math> is the resulting MAC. | |||
Next, the plaintext (<math>P</math>) is created to encrypt with the following formula: | |||
<math>P = R||T||\mathtt{pad}</math> | |||
''pad'' stands for "padding" which is appended to the plaintext. The size of the padding is to fit the block size of the selected block cipher (3DSE = 8 bytes/ AES = 16 bytes). Padding may span over several blocks. Padding added in TLS and DTLS must consist of <math>p+1</math> copies of the same byte value <math>p</math>. The Range for <math>p</math> is <math>0 \le p \le 255</math>. For example, 1 times “0x00” or 3 times “0x02”. | |||
Now the plaintext is being encrypted with CBC-mode: | |||
<math>C_j=E_{K_e}(P_j \oplus C_{j-1})</math> | |||
<math>P_j</math> is the information we want to encrypt. <math>_j</math> identifies the different blocks we want to encrypt. <math>C_0</math> is our starting point (IV). <math>K_e</math> is for the block cipher <math>E</math>. | |||
Put together the data encrypted and being transmitted is: | |||
<math>\mathtt{HDR}||C</math> | |||
<math>C</math> being the cipher text and HDR including version, type and length field. No sequence number (SQN) being transmitted. | |||
=== Decryption === | |||
<math>P_j=D_{K_e}(C_j) \oplus C_{j-1}</math> | |||
<math>D</math> = Decryption algorithm of the block cipher. | |||
<math>P_j</math> is the Plaintext we receive. | |||
The decryption is performed block by block. When finished, the padding is removed and the MAC is being checked. Finally, the sequence number can be checked. | |||
== HMAC == | |||
TLS and DTLS exclusively use the HMAC algorithm. HMAC-MD5, HMAC-SHA-1, and | |||
HMAC-SHA-256 are supported in TLS 1.2. | |||
Fomula: | |||
<math></math> | |||
<math>T = H((K_a \oplus \mathtt{opad})||H((K_a \oplus \mathtt{ipad})||M))</math> | |||
<math>T</math> = MAC tag | |||
<math>M</math> = Message | |||
<math>K_a</math> = Key | |||
<math>H</math> = Algorithm | |||
HMAC applies the specified hash algorithem twice in an iterated fashion. | |||
''opad'' and ''ipad'' are specific 64-byte values (padding) that combined with the Key are exaclty 64 bytes. The hash function uses an encoding step called ''Merkle-Damg ̊ard strengthening''. | |||
HMAC is computed of 64 byte blocks. This block takes 8 bytes for the header and at least 1 byte of padding. | |||
55 bytes of data is the maximum a single block can take. A Message of the length up to 55 bytes need 4 comparison function evaluations to complete: 2 in the hash operation, 2 in the outer hash operation. | |||
Messages from 55 up to (64+55=) 119 bytes give us two 64-byte block. This means that the we have 3 inner hash operations and 2 outer hash operations. For more blocks (3 and more) we can assume you add 1 operation per block. Remember that every operation takes some amount of time to be computed. Operations are in the sub-μ seconds spectrum | |||
Revision as of 17:43, 21 December 2021
Lucky 13 is a timing attack on TLS/DTLS discovered in 2012 by Nadhem AlFardan and Kenny Paterson. In 2013 they published their findings and released their whitepaper. The attack is shown to only work on LAN and is hindered by noise on the network (unwanted traffic).
To understand the attack, first explanation of a few concepts is needed.
Basics
Cipher Block Chaining (CBC) and MAC-then-encrypt are being used in the DTLS record protocol.
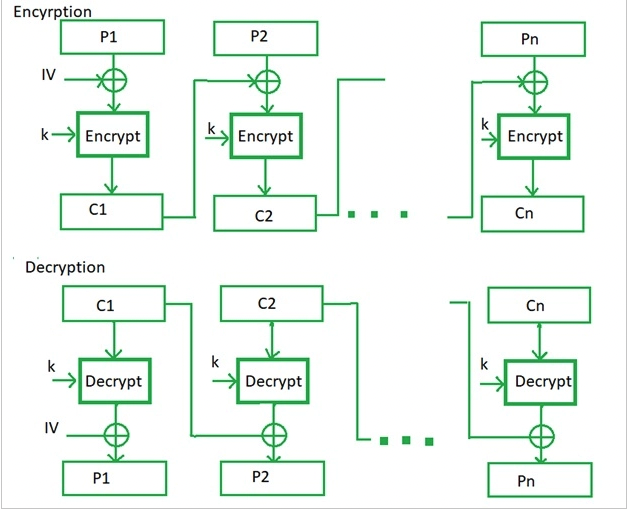
Cipher Block Chaining (CBC)
CBC is a method of encrypting plaintext. It takes a block of clear text and adds it (bit-by-bit) to the previous encryption.
IV = Initialization Vector is a (pseudo)random sequence of characters added to an encryption key. The IV should be different for any two messages encrypted with the same cryptography key. First step is to divide the pain text into block size (size depends on underlying symmetric encryption algorithm). Plain text () and previous ciphertext (Failed to parse (syntax error): {\displaystyle \C_{i−1}} ) are combined with an XOR operation. Then it gets encrypted with the key. Repeat. In the first step we do not have any ciphertext () so we use the IV (initialization vector) for this one. stands for the encryption process.
This leaves us with this formula:
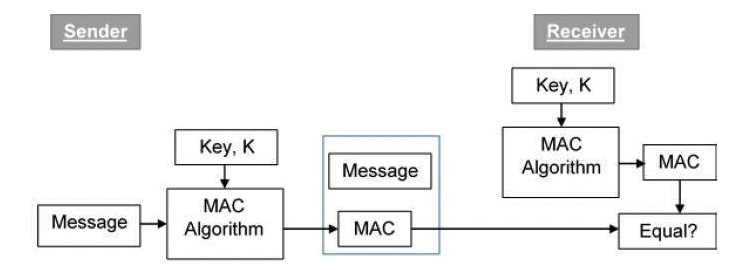
MAC-then-encrypt
MAC provides message authentication. Sender and receiver share a symmetric key.
- The sender uses some publicly known MAC algorithm, inputs the message and the secret key K and produces a MAC value.
- Send it.
- On receipt of the message and the MAC, the receiver feeds the received message and the shared secret key K into the MAC algorithm and re-computes the MAC value.
- The receiver now checks equality of freshly computed MAC with the MAC received from the sender. If they match, then the receiver accepts the message and assures himself that the message has been sent by the intended sender.
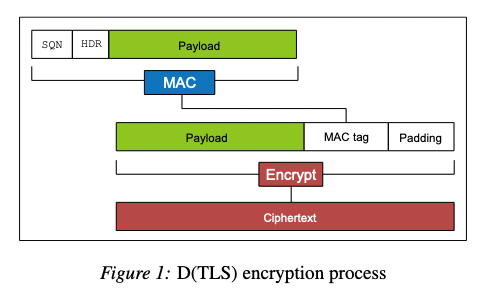
DTLS Record Protocol
Encryption
= individual record (payload)
MAC calculation:
SQN and HDR are prepended and are 13 bytes long:
- SQN = 8-byte
- HDR = 5-byte
- version field = 2-byte
- type = 1-byte
- length = 2-byte
is the resulting MAC.
Next, the plaintext () is created to encrypt with the following formula:
pad stands for "padding" which is appended to the plaintext. The size of the padding is to fit the block size of the selected block cipher (3DSE = 8 bytes/ AES = 16 bytes). Padding may span over several blocks. Padding added in TLS and DTLS must consist of copies of the same byte value . The Range for is . For example, 1 times “0x00” or 3 times “0x02”.
Now the plaintext is being encrypted with CBC-mode:
is the information we want to encrypt. identifies the different blocks we want to encrypt. is our starting point (IV). is for the block cipher .
Put together the data encrypted and being transmitted is:
being the cipher text and HDR including version, type and length field. No sequence number (SQN) being transmitted.
Decryption
= Decryption algorithm of the block cipher. is the Plaintext we receive. The decryption is performed block by block. When finished, the padding is removed and the MAC is being checked. Finally, the sequence number can be checked.
HMAC
TLS and DTLS exclusively use the HMAC algorithm. HMAC-MD5, HMAC-SHA-1, and HMAC-SHA-256 are supported in TLS 1.2.
Fomula:
= MAC tag = Message = Key = Algorithm
HMAC applies the specified hash algorithem twice in an iterated fashion.
opad and ipad are specific 64-byte values (padding) that combined with the Key are exaclty 64 bytes. The hash function uses an encoding step called Merkle-Damg ̊ard strengthening.
HMAC is computed of 64 byte blocks. This block takes 8 bytes for the header and at least 1 byte of padding. 55 bytes of data is the maximum a single block can take. A Message of the length up to 55 bytes need 4 comparison function evaluations to complete: 2 in the hash operation, 2 in the outer hash operation. Messages from 55 up to (64+55=) 119 bytes give us two 64-byte block. This means that the we have 3 inner hash operations and 2 outer hash operations. For more blocks (3 and more) we can assume you add 1 operation per block. Remember that every operation takes some amount of time to be computed. Operations are in the sub-μ seconds spectrum