Metasploit with Armitage
Summary
This documentation describes how to use Armitage GUI with the Metasploit Framework.
Armitage is a Java-based graphical user interface and serves as a free frontend for the Metasploit Framework. The software was first developed by Raphael Mudge in 2013. It is used for the visualization of vulnerable systems, provides suitable exploits and tools for post-exploitation. Access on a single Metasploit RPC instance is possible through multiple Armitage clients. Therefore, teamwork is possible sharing same data, i.e. workspaces and sessions with common event logs. Armitage is a Team Red cooperation, a group of moral hackers (White Hats), whose declared goal is to detect security vulnerabilities before they can be discovered and exploited by destructive hackers (Black Hats). In addition to such projects, the American company offers security audits as well as customized training.
Requirements
- Operating system: Kali Linux amd64 2019.2
- Packages: Metasploit Framework
In order to complete these steps, you should have followed Metasploit Framework MSF before.
Attack Process
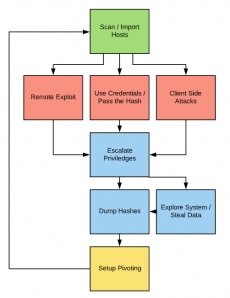
Armitage is able to perform network scans via NMAP but the import of data from external tools is also supported. Hosts are displayed within a GUI workspace. Afterwards the hosts can be compared with the exploit database provided by Metasploit. If no matching exploits can be found, a so-called Hail Mary Attack is possible. In this case, all available exploits from the database are executed without necessary knowledge of the target system. However, this method leaves traces in the network or on hosts. After a successful attack the available post exploitation tools can be used. Once the necessary rights to the system have been obtained or already existed (root exploit), keyloggers can be installed or existing password hash files can be read from the file system. The execution of remote shells is also possible, e.g.: the installation of further malware. Especially interesting is the possibility to use pivot systems, these are systems that have already been compromised within a network and are used for further attacks in the local network. For this purpose Armitage offers support for the SOCKS proxy modules provided by the Metasploit Framework.
First Start
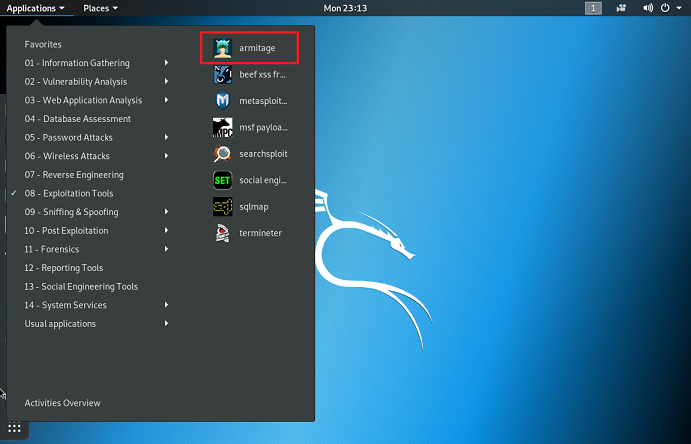
After successful login to our kali linux desktop, the Armitage GUI can be started as follows.
Select 08 - Exploitation Tools - armitage:
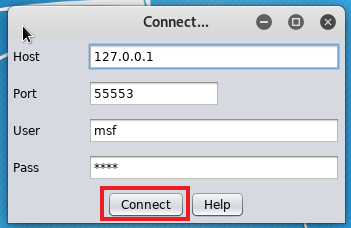
Afterwards start with the 'Connect' Button:
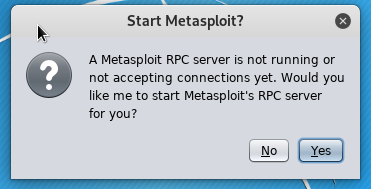
If the metasploit RPC service was not started already, start it with 'Yes':
Example Attack with Armitage
Afterwards we will show an example attack with the Armitage GUI.
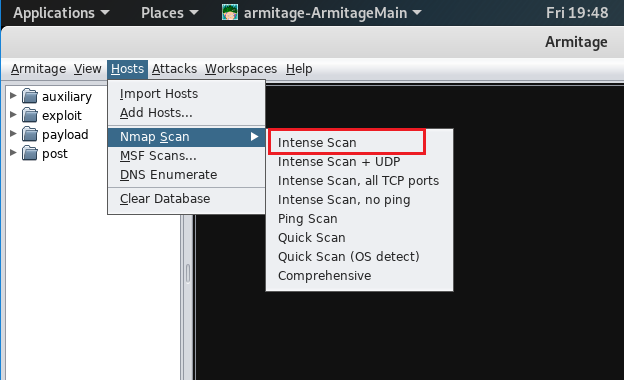
Network Discovery with NMAP
Start with an NMAP 'Intense Scan' within your local network. This will scan for services on well known ports and provides service and os detection:
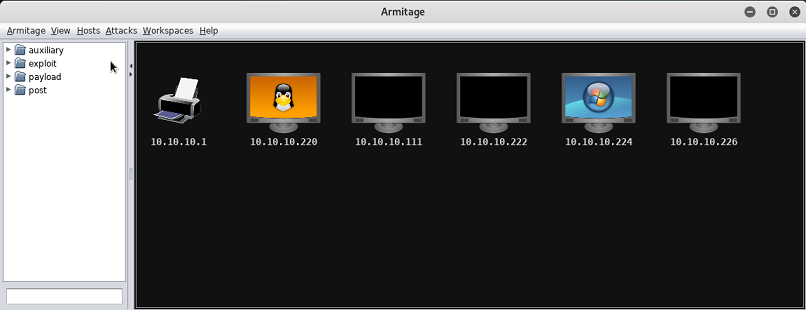
Afterwards detected hosts will be shown in your workspace:
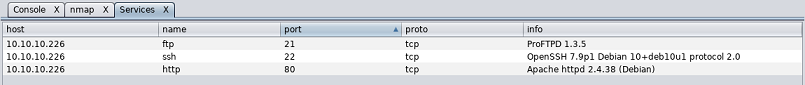
You can check services with a right click on the host:
Attack ProFTPD Service
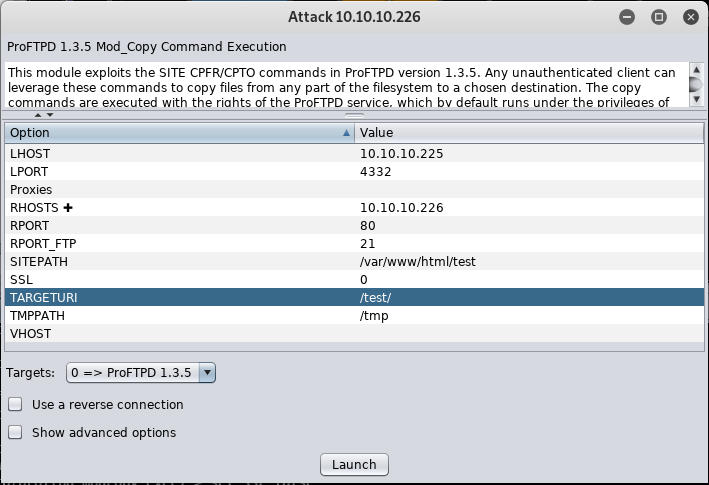
For our demonstration we will use the Exploit CVE-2015-3306, a well known vulnerability in the mod_copy module of ProFTPD.
With a right click on the host, the Exploit 'proftpd_mod_copy' can be selected and executed:
After a successful attack the host picture will look as follows:
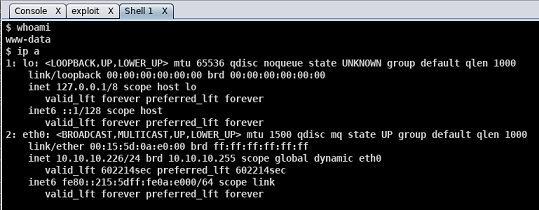
Now we can use the active session for a remote shell: