Mipow Playbulb: Bluetooth Connection Sniffing
Summary
This documentation explains the basics of Bluetooth hacking perfomed on the MiPow Playbulb Candle with the GATT Tool and Bluetooth Sniffing with the Ubertooth One
Requirements
- Bluetooth adapter which can use BLUETOOTH Low Energy (BTLE)
- A computer running a Linux distribution e.g. raspberry pi 3
- The Ubertooth One
- Wire Shark
- hcitool
Description
Prerequisites
Ensure that the Bluetooth sender is running.
sudo service bluetooth status
If the output shows (dead) use the following command.
sudo service bluetooth restart
Check if the hcitool finds your Bluetooth sender
hcitool dev hciconfig -a
Retrieve the Bluetooth Address of the victim device via the hcitool
Depending on the Bluetooth Technology (BR/EDR or LE) the device use there are two commands to scan the Bluetooth addresses.
hcitool scan hcitool lescan
The BLE Scan outputs the Address of the The MiPow Playbulb Candle as follows:
hcitool lescan DC:48:4B:0F:AC:E6 (unknown) DC:48:4B:0F:AC:E6 PLAYBULB
Connect to the victim device and reading its characteristics with the GATT Toll
Before you can start using the GATT Tool you need to know the Bluetooth Address of the victim device. For gathering this information you can use the hcitool, which is described above.
The GATT Tool has an powerful interactive mode. During this mode the devices stay connected and you can use more than one handle sequentially.
sudo gatttool -I <Bluetooth interface> -b <BD_ADDR> connect
To get the name of your Bluetooth interfaces use hciconfig, which is described above.
The Interactive mode also allows to list the characteristics of the connected device and control them.
Connecting the Device in Interactive mode
sudo gatttool -I hci1 -b <BD_ADDR> connect
“hci1” is the Bluetooth sender name and can differ on your device.
Reading the Characteristic which the victim devices have.
characteristics [1] handle: 0x0002, char properties: 0x0a, char value handle: 0x0003, uuid: 00002a00-0000-1000-8000-00805f9b34fb [2] handle: 0x0004, char properties: 0x02, char value handle: 0x0005, uuid: 00002a01-0000-1000-8000-00805f9b34fb [3] handle: 0x0006, char properties: 0x02, char value handle: 0x0007, uuid: 00002a04-0000-1000-8000-00805f9b34fb [4] handle: 0x0009, char properties: 0x22, char value handle: 0x000a, uuid: 00002a05-0000-1000-8000-00805f9b34fb [5] handle: 0x000d, char properties: 0x10, char value handle: 0x000e, uuid: 00002a37-0000-1000-8000-00805f9b34fb [6] handle: 0x0010, char properties: 0x02, char value handle: 0x0011, uuid: 0000fff8-0000-1000-8000-00805f9b34fb [7] handle: 0x0012, char properties: 0x0a, char value handle: 0x0013, uuid: 0000fff9-0000-1000-8000-00805f9b34fb [8] handle: 0x0014, char properties: 0x06, char value handle: 0x0015, uuid: 0000fffa-0000-1000-8000-00805f9b34fb [9] handle: 0x0016, char properties: 0x06, char value handle: 0x0017, uuid: 0000fffb-0000-1000-8000-00805f9b34fb [10] handle: 0x0018, char properties: 0x06, char value handle: 0x0019, uuid: 0000fffc-0000-1000-8000-00805f9b34fb [11] handle: 0x001a, char properties: 0x0a, char value handle: 0x001b, uuid: 0000fffd-0000-1000-8000-00805f9b34fb [12] handle: 0x001c, char properties: 0x0a, char value handle: 0x001d, uuid: 0000fffe-0000-1000-8000-00805f9b34fb [13] handle: 0x001e, char properties: 0x0a, char value handle: 0x001f, uuid: 0000ffff-0000-1000-8000-00805f9b34fb [14] handle: 0x0021, char properties: 0x12, char value handle: 0x0022, uuid: 00002a19-0000-1000-8000-00805f9b34fb [15] handle: 0x0025, char properties: 0x02, char value handle: 0x0026, uuid: 00002a25-0000-1000-8000-00805f9b34fb [16] handle: 0x0027, char properties: 0x02, char value handle: 0x0028, uuid: 00002a27-0000-1000-8000-00805f9b34fb [17] handle: 0x0029, char properties: 0x02, char value handle: 0x002a, uuid: 00002a26-0000-1000-8000-00805f9b34fb [18] handle: 0x002b, char properties: 0x02, char value handle: 0x002c, uuid: 00002a28-0000-1000-8000-00805f9b34fb [19] handle: 0x002d, char properties: 0x02, char value handle: 0x002e, uuid: 00002a29-0000-1000-8000-00805f9b34fb [20] handle: 0x002f, char properties: 0x02, char value handle: 0x0030, uuid: 00002a50-0000-1000-8000-00805f9b34fb [21] handle: 0x0032, char properties: 0x0a, char value handle: 0x0033, uuid: 00001013-d102-11e1-9b23-00025b00a5a5 [22] handle: 0x0034, char properties: 0x08, char value handle: 0x0035, uuid: 00001018-d102-11e1-9b23-00025b00a5a5 [23] handle: 0x0036, char properties: 0x12, char value handle: 0x0037, uuid: 00001014-d102-11e1-9b23-00025b00a5a5 [24] handle: 0x0039, char properties: 0x02, char value handle: 0x003a, uuid: 00001011-d102-11e1-9b23-00025b00a5a5
Analyzing the Characteristics with the GATT Tool
The MiPow Playbulb Candle uses many Characteristics which are defined by the Bluetooth Standard:
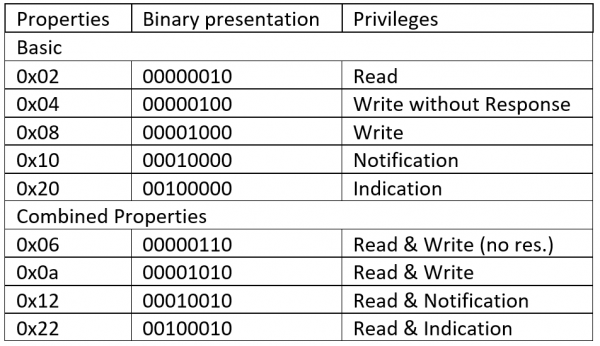
The Properties must be read as the following chart shows:
[1] Read and Write the Device Name
Read the device name:
char-read-hnd 3 Characteristic value/descriptor: 50 4c 41 59 42 55 4c 42
Convert Hex to ASCII:
50 4c 41 59 42 55 4c 42 -> PLAYBULB
Rename the Device:
char-write-req 3 4861636B65640A Characteristic value was written successfully char-read-hnd 3 Characteristic value/descriptor: 48 61 63 6b 65 64 0a
[2] Read the Device Appearance
char-read-hnd 5 Characteristic value/descriptor: 40 03
0x4003 is not in the standard appearances defined
[3] Read the Peripheral Preferred Connection Parameters
char-read-hnd 7 Characteristic value/descriptor: 10 00 20 00 00 00 58 02
[14] Read the Battery Level
char-read-hnd 22 Characteristic value/descriptor: 64
Convert Hex to Dez:
64 hex is 100 dez -> Battery Level is at 100%
[15] Read the Serial Number String
char-read-hnd 26 Characteristic value/descriptor: 42 54 4c 33 30 30
Convert Hex to ASCII:
42 54 4c 33 30 30 -> BTL300
[16] Read the Hardware Revision String
char-read-hnd 28 Characteristic value/descriptor: 43 53 52 31 30 31 78 20 41 30 35
Convert Hex to ASCII:
43 53 52 31 30 31 78 20 41 30 35 -> CSR101x A05
[17] Read the Firmware Revision String
char-read-hnd 2a Characteristic value/descriptor: 42 54 4c 33 30 30 5f 76 36
Convert Hex to ASCII:
42 54 4c 33 30 30 5f 76 36 -> BTL300_v6
[18] Read the Software Revision String
char-read-hnd 2c Characteristic value/descriptor: 41 70 70 6c 69 63 61 74 69 6f 6e 20 76 65 72 73 69 6f 6e 20 32 2e 34 2e 33 2e 32 36
Convert Hex to ASCII: 41 70 70 6c 69 63 61 74 69 6f 6e 20 76 65 72 73 69 6f 6e 20 32 2e 34 2e 33 2e 32 36 -> Application version 2.4.3.26
[19] Read the Manufacturer Name String
char-read-hnd 2e Characteristic value/descriptor: 4d 69 70 6f 77 20 4c 69 6d 69 74 65 64
Convert Hex to ASCII:
4d 69 70 6f 77 20 4c 69 6d 69 74 65 64 -> Mipow Limited
[20] Read the PnP ID
char-read-hnd 30 Characteristic value/descriptor: 01 0a 00 4c 01 00 01
Analyzing the Characteristics with the Ubertooth One
Before you start make sure that your Ubertooth One has the newest firmware installed. To update your Ubertooth One read this Documentation.
To Sniff the Victim device, we use the follow command:
ubertooth-btle -f <BD_ADDR>
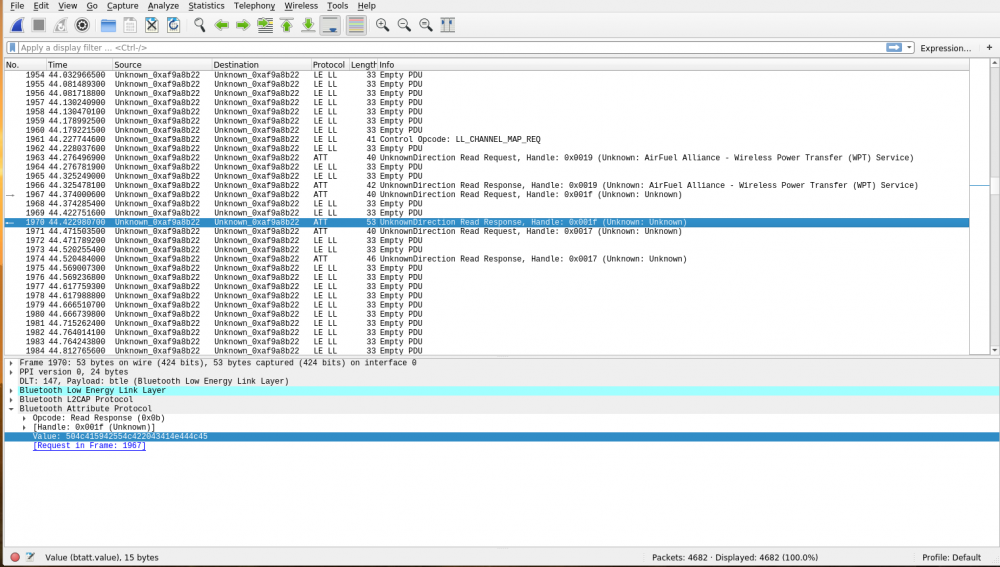
We put the Output of this command into a pipe to monitor the sniffed data in Wireshark
mkfifo /tmp/pipe ubertooth-btle -f <BD_ADDR> -c /tmp/pipe
On a other terminal we start Wireshark
sudo wireshark -I /tmp/pipe
If the protocol of the sniffed data says PPP follow this documentation Now we connect the Victim device to a Smartphone. The Ubertooth may not be able to follow the jump pattern of the connection, so disconnect and reconnect your smartphone until the data stream doesn’t stop.
It was possible to figure out what the handles 0x17 and 0x19 were used for:
[10] Read and write the RGB Values
The light isn’t a usual RGB light with only 3 LEDs for each colour, it has an extra one for natural white light at about 3500k. The RGB Code is encoded like:
WWRRGGBB
The hex values reach from 0 to 255 (ff) which allows 16 Million colour combinations. The brightness is also adjusted by lowering the colour values.
It is also possible to write the colour with the GATT Tool by using this command:
char-write-cmd 19 WWRRGGBB
[10] Read and write the Colour Effects
There are 5 colour effects which the bulb can make
- Candle Flickering
- Blinking
- Pulsating
- Rainbow
- Slow Rainbow
Colour and speeds of this can also be adjusted by the app. The value of the handle 0x17 can be deciphered like:
WWRRGGBBEE00SS00
Where:
WWRRGGBB is the WRGB code like in handle 0x19 EE is the effect SS is the speed of the effect(00 fast, ff slow)
Effect values are:
00 Blinking 01 Pulsating 02 Rainbow 03 Slow Rainbow 04 Candle Flickering On 05 Candle Flickering Off ff No Effect
It is also possible to write the colour with the GATT Tool by using this command:
char-write-cmd 17 WWRRGGBBEE00SS00
Sniffing the connection establishment with wireshark
First the Smart phone reads the 0x17 handle (Effects).
Then it reads 0x1f handle which is unknown.
At least it reads the 0x19 handle (Colour).
The Smart phone knows if the candle is in Colour or effect mode by the effect value in the 0x17 handle.
This connection recording shows there is no authentication and encryption in this device, which made it possible to write a python script that can control the PlayBulb.
The script can be found on my gitlab
Used Hardware
- raspberry pi 3 b+
- Ubertooth One
References
- Character Properties: http://dev.ti.com/tirex/content/simplelink_cc2640r2_sdk_1_35_00_33/docs/ble5stack/ble_user_guide/html/doxygen/group___s_n_p___p_r_o_p___b_i_t_m_a_p_s___d_e_f_i_n_e_s.html
- Standardized Characteristics: https://www.bluetooth.com/specifications/gatt/characteristics/
- Ubertooth github: https://github.com/greatscottgadgets/ubertooth/