Nmap
Summary
Nmap (Network Mapper) is a free and open-source tool for network discovery and security auditing. Nmap can be used to identify hosts and services on a computer network, thus creating a “map” of the network. It can also be used to detect open ports and services, operating systems, and even live hosts on a network.
Description
Nmap uses various techniques such as IP address sweep, TCP and UDP port scans, and other methods to identify hosts and services on a network. It can also be used to detect firewalls, intrusion detection systems, and other security features. Nmap is also useful for troubleshooting network issues, as it can help identify misconfigured devices or other problems.
Nmap can be run on various operating systems, including Windows, Linux, and MacOS. It also offers a command line interface, a graphical user interface, and can be integrated into other tools and scripts.
In addition to the features mentioned above, Nmap also offers various advanced features such as:
• OS detection: Nmap can detect the operating system of a host by sending specific packets and analyzing the responses. • Version detection: Nmap can detect the version of the services running on a host. • Scripting Engine (NSE): NSE allows users to write and execute scripts to automate tasks and gather additional information about hosts and services on a network. • Output formats: Nmap can output the results of a scan in various formats such as XML or plain text. • Performance optimization: Nmap offers various options to optimize the speed and efficiency of a scan.
Nmap can be run on a single host, a range of IP addresses, or even a list of IP addresses. It can also be used to scan for hosts on a specific subnet.
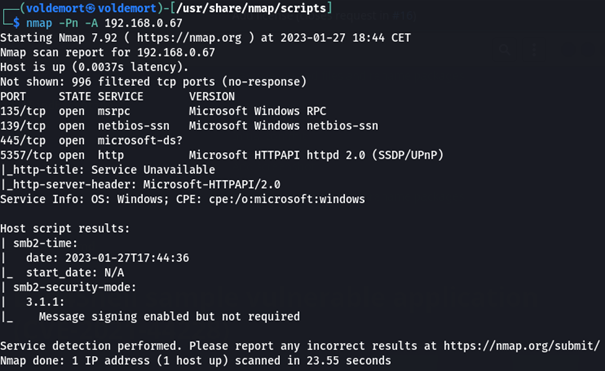
Example of nmap output on a specific host:
Nmap Script Engine
The Nmap Scripting Engine (NSE) is a powerful feature of Nmap that allows users to write scripts in Lua to automate tasks and gather additional information about hosts and services on a network. These scripts can be used to perform a wide range of tasks such as:
• Vulnerability detection: NSE scripts can be used to detect known vulnerabilities in a host or service.
• Information gathering: NSE scripts can gather additional information about a host or service, such as the type of web server running or the version of the operating system.
• Brute-forcing: NSE scripts can be used to perform brute-force attacks on services such as SSH or Telnet.
NSE scripts can be run individually or in combination with other scripts. Nmap ships with a large number of built-in scripts that can be used for various tasks. Additionally, the Nmap community has written and shared many more scripts that can be downloaded and used.
Using NSE scripts can greatly enhance the functionality of Nmap and allow for more detailed and efficient network scans.
Here are a few examples of how NSE can be used:
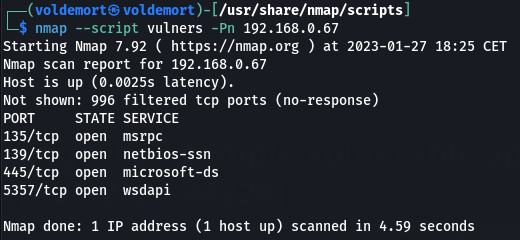
• Vulnerability detection: One of the most popular NSE scripts is "vulners", which can be used to detect known vulnerabilities in a host or service. This script uses a vulnerability database to check for known vulnerabilities and can be run with the command "nmap --script vulners [target]"
• Information gathering: The "http-title" script can be used to gather the title of a website. The script sends an HTTP request to the target and parses the response to extract the title. This script can be run with the command "nmap --script http-title [target]"
• Brute-forcing: The "ssh-brute" script can be used to perform a brute-force attack on an SSH service. The script tries to log in to the SSH service using a list of username and password combinations. This script can be run with the command "nmap --script ssh-brute [target]".
• Script for specific service: The "smb-enum-shares" script will enumerate the shared resources on the SMB service. This script can be run with the command "nmap --script smb-enum-shares [target]".
• Script for specific operating system: The "smb-os-discovery" script can be used to determine the operating system of a Windows host. This script can be run with the command "nmap --script smb-os-discovery [target]".
Example of usage of vulners script: