Difference between revisions of "OPTIGA Trust E evaluation kit"
m (→References) |
|||
| (19 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
== Summary == | == Summary == | ||
This article gives an overview about the functions and use case of the Optiga Trust E Evaluation Kit. The XMC4500 chip from the board enables a secure communication in the IoT environment by providing integrity of the data. This can be achieved with the help of cryptographic certificates. | |||
In the end a short conclusion about the poor usability of the board is given. By now, the board can only be used with an x64-based Windows machines and programming the microcontroller requires a good basic knowledge in this field. Infineon's support is also not really given anymore for the Kit. | |||
== Used Hardware/Software == | |||
<p>Infineon requests the user to register at www.infineon.com under the myInfineon portal to get all relevant information and software regarding the actual kit. However the XMC4500 Relax Kit can not be registered anymore on the myInfineon platform. Therefore, the DAVE IDE has to be installed manually. The link for the DAVE installer is provided below. Alternatively, the Keil MDK can be used.</p> | |||
=== Infineon development tools === | |||
<p> | <p>Download-Link for Dave ™ version 4.5 (Windows only)</p> | ||
[https://softwaretools.infineon.com/tools/com.ifx.tb.tool.daveide DAVE version 4.5] | |||
< | <p>Download-Link for Example Codes</p> | ||
<p> | [https://www.infineon.com/cms/en/product/promopages/aim-mc/dave_downloads.html DAVE Code Examples] | ||
[https://github.com/Infineon/arduino-optiga-trust-e ARDUINO Code Examples] | |||
<p> First Steps </p> | |||
[https://www.infineon.com/dgdl/Infineon-DAVE_Quick_Start-GS-v02_00-EN.pdf?fileId=5546d4624cb7f111014d059f7b8c712d Quick Start - Simple LED Blinky] | |||
The DAVE ™ package contains the IDE and all required libraries. There's also a quick start tutorial for DAVE in the installation folder. | |||
<br/> | |||
=== Datasheets === | |||
https:// | <ul> | ||
<li>[https://www.infineon.com/cms/de/product/evaluation-boards/optiga-trust-e-eval-kit/ Optiga Trust E Evaluation Kit Overview]</li> | |||
<li>[https://www.infineon.com/dgdl/Board_Users_Manual_XMC4500_Relax_Kit-V1_R1.2_released.pdf?fileId=db3a30433acf32c9013adf6b97b112f9 XMC4500 Board User’s Manual]</li> | |||
<li>[https://www.infineon.com/dgdl/Infineon-OPTIGA%20TRUST%20E%20SLS%2032AIA-DS-v01_00-EN.pdf?fileId=5546d4625e37f35a015e56cfb42f5b81 Optiga Trust E Datasheet]</li> | |||
<li>[https://www.infineon.com/dgdl/Infineon-OPTIGA_Trust_E_DesignIn_Application_Note_V1_0-AN-v01_00-EN.pdf?fileId=5546d4625d5945ed015d6043dff8543a Application Note for Optiga Trust E]</li> | |||
<li>[https://www.infineon.com/dgdl/Infineon-OPTIGA_Trust_E_SLS32AIA-PB-v09_17-EN.pdf?fileId=5546d4624e765da5014eaabac63f5a38 Optiga Trust E Product Brief]</li> | |||
<li>[https://usermanual.wiki/Document/OPTIGATrustXSolutionReferenceManualv135.2125473546/view/ Optiga Trust E/X Reference Manual]</li> | |||
</ul> | |||
<br/> | <br/> | ||
=== OPTIGA ™ Trust E-Evaluation Kit === | |||
[[Optiga_Trust_E_Evaluation_Kit]] | |||
The Infineon Technologies OPTIGA ™ Trust E-Evaluation Kit evaluates and demonstrates Security for IoT peripherals. The kit features a PC plug-in board based on the XMC microcontroller and comes with a free to use GitHub repo software based on the open-source-application [http://www.arduino.cc Arduino]. The OPTIGA ™ Trust E Evaluation Kit allows the user to try out OPTIGA Trust E applications, including authentication, adding cryptographic certificates, and read/write data. | |||
The | The OPTIGA ™ Trust E Evaluation Kit helps protect services, business models and user experience. This security solution uniquely identifies objects and protects PKI networks based on their one-way authentication mechanism. In addition, the Board protects the quality and safety of products. | ||
The OPTIGA Trust E is based on Elliptic Curve Cryptography (ECC) with 256-bit, AES128 and SHA-256. This security technology greatly enhances the security of the entire system. In addition, the OPTIGA Trust E covers a wide range of applications to protect the authentication, security and confidentiality of embedded devices. These include mutual authentication, secure communication, data store protection, lifecycle management, secured updates, and platform integrity protection. | |||
The OPTIGA | |||
The out-of-the-box facility, with full system integration and pre-programmed essentials, reduces design, integration and deployment requirements. As a ready-to-use solution, the OPTIGA Trust E comes with OS, embedded application and full host-side integration support. | The out-of-the-box facility, with full system integration and pre-programmed essentials, reduces design, integration and deployment requirements. As a ready-to-use solution, the OPTIGA Trust E comes with OS, embedded application and full host-side integration support. | ||
== | ==== Characteristics ==== | ||
== | |||
<ul> | <ul> | ||
<li>High-end security controller</li> | <li>High-end security controller</li> | ||
<li>One-way authentication with ECDSA</li> | <li>One-way authentication with ECDSA</li> | ||
<li>Mutual authentication with DTLS client (standard RFC 6347)</li> | <li>Mutual authentication with DTLS client (standard RFC 6347)</li> | ||
| Line 61: | Line 67: | ||
</ul> | </ul> | ||
== | |||
==== Security Features ==== | |||
Cryptographic support: | |||
<ul> | |||
<li>ECC256</li> | |||
<li>AES128</li> | |||
<li>SHA-256</li> | |||
<li>TRNG (TrueRandomNumberGenerator)</li> | |||
<li>DRNG (DigitalRandomNumberGenerator)</li> | |||
</ul> | |||
==== Functions ==== | |||
The Board provides three main functions for the user: | |||
<ul> | <ul> | ||
<li> | <li>One-Way Authentication</li> | ||
<li> | <li>Cryptographic Certificates</li> | ||
<li> | <li>Read and Write Data</li> | ||
</ul> | </ul> | ||
== AES - Advanced Encryption Standard == | |||
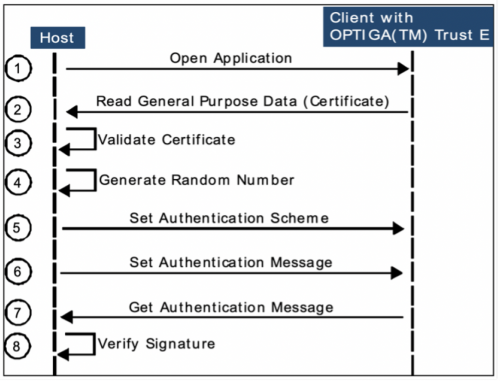
[[File:One-Way_Authentication.png|500px|https://www.infineon.com/dgdl/Infineon-OPTIGA_Trust_E_DesignIn_Application_Note_V1_0-AN-v01_00-EN.pdf?fileId=5546d4625d5945ed015d6043dff8543a]] | |||
Step 1 to 3: The host sends an "Open Application" command to the client to start the authentication process. The client reads and verifies the certificate. To verify the certificate, all intermediate certificates and the trusted root certificate are required. | |||
Step 4 to 8: The security of the authentication process depends heavily on the quality of the random numbers. In case of repetitions in the pattern, a replay attack may occur. To prevent this, the random numbers are signed with the kit's private key in step 4. Finally, the signature is verified using the public key from the previously obtained device certificate. To successfully authenticate a client, the decrypted signature message and the random number (originally sent) must match. | |||
==Used Technology== | |||
==== AES - Advanced Encryption Standard ==== | |||
Advanced Encryption Standard, AES for short, is a symmetric encryption method. Since the end of 2001, Rijndeal has been officially standardized as AES in the US by NIST (National Institute of Standards and Technology). It is used for the encryption of documents and communication connections. AES is not patented and therefore freely usable. | Advanced Encryption Standard, AES for short, is a symmetric encryption method. Since the end of 2001, Rijndeal has been officially standardized as AES in the US by NIST (National Institute of Standards and Technology). It is used for the encryption of documents and communication connections. AES is not patented and therefore freely usable. | ||
Rijndael and AES are block ciphers based on a substitution-permutation network (SPN). The procedure alternates between substitution and permutation at each step. The transformation of the plaintext occurs in several rounds of the same structure. The plaintext is not processed as a whole, but in blocks. | Rijndael and AES are block ciphers based on a substitution-permutation network (SPN). The procedure alternates between substitution and permutation at each step. The transformation of the plaintext occurs in several rounds of the same structure. The plaintext is not processed as a whole, but in blocks. | ||
For Rijndael, block length and key length can be independently 128, 160, 192, 224 or 256 bits. For AES, the block length is set to 128 bits and the key size to 128 (10 rounds), 192 (12 rounds), and 256 bits (14 rounds). | For Rijndael, block length and key length can be independently 128, 160, 192, 224 or 256 bits. For AES, the block length is set to 128 bits and the key size to 128 (10 rounds), 192 (12 rounds), and 256 bits (14 rounds). | ||
The AES decryption necessarily requires that the same steps be followed as with encryption. Just in reverse order. It is, in a way, a weakness of AES. | The AES decryption necessarily requires that the same steps be followed as with encryption. Just in reverse order. It is, in a way, a weakness of AES. | ||
== ECC - Elliptic Curve Cryptography == | ==== ECC - Elliptic Curve Cryptography ==== | ||
Crypto-systems and methods based on elliptic curves are referred to as ECC methods. ECC procedures have been part of the NIST (National Institute of Standards and Technology) standards since 1999. ECC methods are among the asymmetric encryption methods. The number after the hyphen refers to the key length. Typical applications of ECC are the key exchange and signature procedures. Also, Mozilla Foundation products (including Firefox, Thunderbird) support ECC with min. 256 bit key length. | Crypto-systems and methods based on elliptic curves are referred to as ECC methods. ECC procedures have been part of the NIST (National Institute of Standards and Technology) standards since 1999. ECC methods are among the asymmetric encryption methods. The number after the hyphen refers to the key length. Typical applications of ECC are the key exchange and signature procedures. Also, Mozilla Foundation products (including Firefox, Thunderbird) support ECC with min. 256 bit key length. | ||
Roughly speaking, ECC methods are based on operations with pairs of points on certain elliptic curves. Despite the complexity, the mathematics behind the ECC methods has been sufficiently well researched. Most cryptographers recommend ECC methods to be preferred. | Roughly speaking, ECC methods are based on operations with pairs of points on certain elliptic curves. Despite the complexity, the mathematics behind the ECC methods has been sufficiently well researched. Most cryptographers recommend ECC methods to be preferred. | ||
The use of elliptic curves requires that both communication partners support the same curve. That means you can not just use any curve. It has to be a specific one. | The use of elliptic curves requires that both communication partners support the same curve. That means you can not just use any curve. It has to be a specific one. | ||
== SHA - Secure Hash Algorithm (SHA-1 / SHA-2 / SHA-3) == | ==== SHA - Secure Hash Algorithm (SHA-1 / SHA-2 / SHA-3) ==== | ||
The Secure Hash Algorithm, SHA for short, and all its versions, are cryptographic hash functions. These are used to calculate a check value for any digital data (messages) and are among other things the basis for creating a digital signature. The check value is used to ensure the integrity of a message. If two messages produce the same check value, the equality of the messages should be guaranteed in their normal discretion, without prejudice to specific attempted manipulation of the messages. That's why we require a cryptographic hash function, the property of collision safety: it should be virtually impossible to create two different messages with the same test value. | The Secure Hash Algorithm, SHA for short, and all its versions, are cryptographic hash functions. These are used to calculate a check value for any digital data (messages) and are among other things the basis for creating a digital signature. The check value is used to ensure the integrity of a message. If two messages produce the same check value, the equality of the messages should be guaranteed in their normal discretion, without prejudice to specific attempted manipulation of the messages. That's why we require a cryptographic hash function, the property of collision safety: it should be virtually impossible to create two different messages with the same test value. | ||
SHA was developed by the US secret service NSA on behalf of the US standardization authority NIST. SHA is used in all popular web applications and network protocols. PGP, SSL, IPsec and S / MIME. And of course with different signature methods. For example, for signing certificates. | SHA was developed by the US secret service NSA on behalf of the US standardization authority NIST. SHA is used in all popular web applications and network protocols. PGP, SSL, IPsec and S / MIME. And of course with different signature methods. For example, for signing certificates. | ||
The original SHA is referred to as SHA-1 to distinguish it from its successors SHA-2 and SHA-3. SHA-3 should not replace SHA-2, but is an alternative. Should SHA-2 be broken at some point, you can go to SHA-3. | The original SHA is referred to as SHA-1 to distinguish it from its successors SHA-2 and SHA-3. SHA-3 should not replace SHA-2, but is an alternative. Should SHA-2 be broken at some point, you can go to SHA-3. | ||
==== Cryptographic Certificates ==== | |||
Cryptographic Certificates are a way to map a public key to a corresponding entity. In this case, the entity can be anything (a person, a server, a thing). By using certificates the user can be 100% sure that the messages were really sent by the corresponding entity. | |||
Certificates must be verified by the Kit. This process is part of the "One-Way Authentication". The Kit needs to verify all certificates up to the "Certificate Authority" (CA). The CA is the end of the the certificate chain and all communication partners need to trust this Authority. | |||
== Application Field == | |||
The Optiga Trust E Evaluation Kit was designed so support any kind of IoT Application. Here are some examples where the Kit could be used: | |||
<ul> | |||
<li>Industrial Control and Automation</li> | |||
<li>Consumer Electronics</li> | |||
<li>Smart Home</li> | |||
<li>Medical Equipment</li> | |||
</ul> | |||
<p>The Kit is build to support the Security of any IoT peripheral. Most of the devices do not have their own security protocol implemented because of the huge limitations in IoT. However, the underlying microcontroller programming and the missing support from Infineon are the reasons why the board was never widely used in private environment. </p> | |||
== Objective and results of the project == | == Objective and results of the project == | ||
=== Getting started with DAVE === | |||
The first objective was to test a simple Led toggling program to determine wether the XMC4500 board is working as it is supposed to. To do that the DAVE ™ 4 environment was used as it is recommended by Infineon. After the download and installation of Dave ™ 4 according to the Quick installation guide that came with the download, the Segger JLink needs to be installed and the libraries need to be updated as well. The first example code can be tested by downloading it on the Dave application itself, then building and debugging it. In this case, there was a problem. The microcontroller was not recognized by the program, the JLink couldn't be found. Following approaches were taken: | |||
<ul> | |||
<li>update the Segger JLink</li> | |||
<li>checking the preferences of Dave ™ 4</li> | |||
<li>trying other example codes</li> | |||
<li>contact the Infineon Support</li> | |||
<li>etc.</li> | |||
</ul> | |||
It has turned out, that DAVE 4 is not compatible with the latest J-Link driver. Also the promised GUI from the Infineon-website does not exist. After talking to the support of Infineon it was clear that there is no "Demo Software" for private usage. | |||
The next approach was to see if the microcontroller would run on Keil MDK, A simple LED blinking examples code was installed and successfully run on the Keil environment. This meant that the microcontroller was actually able to connect to the PC. The next move was to try out older versions of Dave (Dave ™ 3), which also didn't work. So an older version of the Segger JLink was installed, and finally the board could be connected to Dave, it worked on both Dave ™ 3 and Dave ™ 4. The LED toggling code worked properly. | |||
=== Functions === | |||
AES: The AES example code can be installed through the Dave ™ 4 Project Library. The installation is described on the corresponding Readme-file. Another problem appeared after running the code trough the debugger. The application was supposed to let the Led blink if the values of the key and the decryption output matched. But even though they did the Led still wouldn't toggle. The approach was to configure USART to be able to connect the microcontroller with TeraTerm so that the user can see if the algorithm worked correctly. But because of the fact that the XMC4500 was only recognized by the Dave application and not by the PC itself, there was no COM-Port found by TeraTerm. Therefore the final step was to set one of the other Leds as the output and to let the Led blink at the start and turn it off after the values matched by setting the 'Initial Output Level' of the Digital I/O pin to high. | |||
ECC & SHA: There are no example codes distributed from Infineon for the ECC and SHA algorithms, but a few C example codes can be found on the internet. The example codes that were tested for these projects can be found on the 'References' part of this aritcle. There were error messages on all of these example codes. Almost all the time the problem was the included library. Either there were some files missing or the files coulnd't be found on that path. Another problem was that the code was not compatible with the Dave ™ 4 interface. The example codes were modified to try to solve these error messages. Either the paths of the files were changed or new library files were added. But with each modification, new error messages popped up. For this project especially the Optiga Trust X Framework code on Github seemed to be a good choice for cryptographical algorithms for Dave ™ 4. But, again, the problem was to integrate the two branches of the code, develop & master, so that the library files were complete. But even though the paths to the files were changed in the code or/and the location of these files were changed, the error messages couldn't still be resolved. There are probably other underlying problems for these errors. | |||
=== Conclusion === | |||
Unpredictable Problems with Dave ™ 4: There is barely any documentation on how to use Dave ™ 4 or solutions to problems on writing code or handling error messages, not even on the Infineon webpage. The example codes just explained how to get the code running but they didn't say what the application is really supposed to do, the user doesn't really know what the input & the output should be or what to do in case of an error. | Unpredictable Problems with Dave ™ 4: There is barely any documentation on how to use Dave ™ 4 or solutions to problems on writing code or handling error messages, not even on the Infineon webpage. The example codes just explained how to get the code running but they didn't say what the application is really supposed to do, the user doesn't really know what the input & the output should be or what to do in case of an error. Also the support from Infineon was not very helpful in this case. The only thing provided by Infineon was the DAVE IDE and some Code Examples. The next thing is the huge amount of effort that must be taken when simply installing a test program on the kit. The IDE must be installed manually as well as the drivers and the debugger does still not work. This is frustrating when thinking about to implement a cryptographic functions on the kit. | ||
Problems with Arduino: On the official "Optiga Trust E Evaluation Kit" Website is a link to a GitHub Repo with Arduino Code examples. Unfortunately you can not use these examples because the board is not detected in the Arduino IDE. Also after installing the requires drivers the board ist still not detected. | |||
To sum this up: the board has a poor compatibility to other devices. For some reason you can only connect the board to a x64-based Windows-machine. Also the DAVE IDE does only exist for Windows. The next problem are the drivers. Infineon requests the user to install external J-Link drivers to run the debugger but also with the installed drivers the debugger does not work. This makes it nearly impossible to deploy any security related applications with the Optiga Trust E Evaluation Kit. Overall it's very hard to use the board and his functions. | |||
== Courses == | |||
* [[Einführendes_Wahlfachprojekt]] (2019) | |||
== References == | |||
<ul> | |||
<p>https:// | <li>Overview of XMC-Microcontrollers & Software: | ||
<p>https://www.infineon.com/cms/en/product/microcontroller/32-bit-industrial-microcontroller-based-on-arm-cortex-m/?redirId=53843#!tools</p></li> | |||
Small sample Code ECDH: | <li>Sample Code AES: | ||
<p>https://github.com/kokke/tiny-ECDH-c</p> | <p>https://www.infineon.com/cms/en/product/promopages/aim-mc/dave_downloads.html</p></li> | ||
<li>Sample Code ECDH & SHA: | |||
<p>https://github.com/Infineon/getstarted-optiga-trust-x</p></li> | |||
<li>Small sample Code ECDH: | |||
<p>https://github.com/kokke/tiny-ECDH-c</p></li> | |||
</ul> | |||
[[Category: | [[Category:Documentation]] | ||
Latest revision as of 19:44, 6 January 2022
Summary
This article gives an overview about the functions and use case of the Optiga Trust E Evaluation Kit. The XMC4500 chip from the board enables a secure communication in the IoT environment by providing integrity of the data. This can be achieved with the help of cryptographic certificates.
In the end a short conclusion about the poor usability of the board is given. By now, the board can only be used with an x64-based Windows machines and programming the microcontroller requires a good basic knowledge in this field. Infineon's support is also not really given anymore for the Kit.
Used Hardware/Software
Infineon requests the user to register at www.infineon.com under the myInfineon portal to get all relevant information and software regarding the actual kit. However the XMC4500 Relax Kit can not be registered anymore on the myInfineon platform. Therefore, the DAVE IDE has to be installed manually. The link for the DAVE installer is provided below. Alternatively, the Keil MDK can be used.
Infineon development tools
Download-Link for Dave ™ version 4.5 (Windows only)
Download-Link for Example Codes
DAVE Code Examples ARDUINO Code Examples
First Steps
Quick Start - Simple LED Blinky
The DAVE ™ package contains the IDE and all required libraries. There's also a quick start tutorial for DAVE in the installation folder.
Datasheets
- Optiga Trust E Evaluation Kit Overview
- XMC4500 Board User’s Manual
- Optiga Trust E Datasheet
- Application Note for Optiga Trust E
- Optiga Trust E Product Brief
- Optiga Trust E/X Reference Manual
OPTIGA ™ Trust E-Evaluation Kit
The Infineon Technologies OPTIGA ™ Trust E-Evaluation Kit evaluates and demonstrates Security for IoT peripherals. The kit features a PC plug-in board based on the XMC microcontroller and comes with a free to use GitHub repo software based on the open-source-application Arduino. The OPTIGA ™ Trust E Evaluation Kit allows the user to try out OPTIGA Trust E applications, including authentication, adding cryptographic certificates, and read/write data.
The OPTIGA ™ Trust E Evaluation Kit helps protect services, business models and user experience. This security solution uniquely identifies objects and protects PKI networks based on their one-way authentication mechanism. In addition, the Board protects the quality and safety of products.
The OPTIGA Trust E is based on Elliptic Curve Cryptography (ECC) with 256-bit, AES128 and SHA-256. This security technology greatly enhances the security of the entire system. In addition, the OPTIGA Trust E covers a wide range of applications to protect the authentication, security and confidentiality of embedded devices. These include mutual authentication, secure communication, data store protection, lifecycle management, secured updates, and platform integrity protection.
The out-of-the-box facility, with full system integration and pre-programmed essentials, reduces design, integration and deployment requirements. As a ready-to-use solution, the OPTIGA Trust E comes with OS, embedded application and full host-side integration support.
Characteristics
- High-end security controller
- One-way authentication with ECDSA
- Mutual authentication with DTLS client (standard RFC 6347)
- Secure communication with DTLS
- Compliant with USB Type-C ™ authentication standard
- I2C interface
- Cryptographic support: ECC256, AES128, SHA-256, TRNG, DRNG
- Standard and extended temperature ranges
- Complete system integration support
- Common Criteria certified EAL6 + (high) hardware
- Cryptographic Toolbox based on ECC NIST P256, P384 and SHA256 (register, verify, key generation, ECDH, session key derivation)
Security Features
Cryptographic support:
- ECC256
- AES128
- SHA-256
- TRNG (TrueRandomNumberGenerator)
- DRNG (DigitalRandomNumberGenerator)
Functions
The Board provides three main functions for the user:
- One-Way Authentication
- Cryptographic Certificates
- Read and Write Data
Step 1 to 3: The host sends an "Open Application" command to the client to start the authentication process. The client reads and verifies the certificate. To verify the certificate, all intermediate certificates and the trusted root certificate are required.
Step 4 to 8: The security of the authentication process depends heavily on the quality of the random numbers. In case of repetitions in the pattern, a replay attack may occur. To prevent this, the random numbers are signed with the kit's private key in step 4. Finally, the signature is verified using the public key from the previously obtained device certificate. To successfully authenticate a client, the decrypted signature message and the random number (originally sent) must match.
Used Technology
AES - Advanced Encryption Standard
Advanced Encryption Standard, AES for short, is a symmetric encryption method. Since the end of 2001, Rijndeal has been officially standardized as AES in the US by NIST (National Institute of Standards and Technology). It is used for the encryption of documents and communication connections. AES is not patented and therefore freely usable.
Rijndael and AES are block ciphers based on a substitution-permutation network (SPN). The procedure alternates between substitution and permutation at each step. The transformation of the plaintext occurs in several rounds of the same structure. The plaintext is not processed as a whole, but in blocks.
For Rijndael, block length and key length can be independently 128, 160, 192, 224 or 256 bits. For AES, the block length is set to 128 bits and the key size to 128 (10 rounds), 192 (12 rounds), and 256 bits (14 rounds). The AES decryption necessarily requires that the same steps be followed as with encryption. Just in reverse order. It is, in a way, a weakness of AES.
ECC - Elliptic Curve Cryptography
Crypto-systems and methods based on elliptic curves are referred to as ECC methods. ECC procedures have been part of the NIST (National Institute of Standards and Technology) standards since 1999. ECC methods are among the asymmetric encryption methods. The number after the hyphen refers to the key length. Typical applications of ECC are the key exchange and signature procedures. Also, Mozilla Foundation products (including Firefox, Thunderbird) support ECC with min. 256 bit key length.
Roughly speaking, ECC methods are based on operations with pairs of points on certain elliptic curves. Despite the complexity, the mathematics behind the ECC methods has been sufficiently well researched. Most cryptographers recommend ECC methods to be preferred. The use of elliptic curves requires that both communication partners support the same curve. That means you can not just use any curve. It has to be a specific one.
SHA - Secure Hash Algorithm (SHA-1 / SHA-2 / SHA-3)
The Secure Hash Algorithm, SHA for short, and all its versions, are cryptographic hash functions. These are used to calculate a check value for any digital data (messages) and are among other things the basis for creating a digital signature. The check value is used to ensure the integrity of a message. If two messages produce the same check value, the equality of the messages should be guaranteed in their normal discretion, without prejudice to specific attempted manipulation of the messages. That's why we require a cryptographic hash function, the property of collision safety: it should be virtually impossible to create two different messages with the same test value.
SHA was developed by the US secret service NSA on behalf of the US standardization authority NIST. SHA is used in all popular web applications and network protocols. PGP, SSL, IPsec and S / MIME. And of course with different signature methods. For example, for signing certificates. The original SHA is referred to as SHA-1 to distinguish it from its successors SHA-2 and SHA-3. SHA-3 should not replace SHA-2, but is an alternative. Should SHA-2 be broken at some point, you can go to SHA-3.
Cryptographic Certificates
Cryptographic Certificates are a way to map a public key to a corresponding entity. In this case, the entity can be anything (a person, a server, a thing). By using certificates the user can be 100% sure that the messages were really sent by the corresponding entity.
Certificates must be verified by the Kit. This process is part of the "One-Way Authentication". The Kit needs to verify all certificates up to the "Certificate Authority" (CA). The CA is the end of the the certificate chain and all communication partners need to trust this Authority.
Application Field
The Optiga Trust E Evaluation Kit was designed so support any kind of IoT Application. Here are some examples where the Kit could be used:
- Industrial Control and Automation
- Consumer Electronics
- Smart Home
- Medical Equipment
The Kit is build to support the Security of any IoT peripheral. Most of the devices do not have their own security protocol implemented because of the huge limitations in IoT. However, the underlying microcontroller programming and the missing support from Infineon are the reasons why the board was never widely used in private environment.
Objective and results of the project
Getting started with DAVE
The first objective was to test a simple Led toggling program to determine wether the XMC4500 board is working as it is supposed to. To do that the DAVE ™ 4 environment was used as it is recommended by Infineon. After the download and installation of Dave ™ 4 according to the Quick installation guide that came with the download, the Segger JLink needs to be installed and the libraries need to be updated as well. The first example code can be tested by downloading it on the Dave application itself, then building and debugging it. In this case, there was a problem. The microcontroller was not recognized by the program, the JLink couldn't be found. Following approaches were taken:
- update the Segger JLink
- checking the preferences of Dave ™ 4
- trying other example codes
- contact the Infineon Support
- etc.
It has turned out, that DAVE 4 is not compatible with the latest J-Link driver. Also the promised GUI from the Infineon-website does not exist. After talking to the support of Infineon it was clear that there is no "Demo Software" for private usage.
The next approach was to see if the microcontroller would run on Keil MDK, A simple LED blinking examples code was installed and successfully run on the Keil environment. This meant that the microcontroller was actually able to connect to the PC. The next move was to try out older versions of Dave (Dave ™ 3), which also didn't work. So an older version of the Segger JLink was installed, and finally the board could be connected to Dave, it worked on both Dave ™ 3 and Dave ™ 4. The LED toggling code worked properly.
Functions
AES: The AES example code can be installed through the Dave ™ 4 Project Library. The installation is described on the corresponding Readme-file. Another problem appeared after running the code trough the debugger. The application was supposed to let the Led blink if the values of the key and the decryption output matched. But even though they did the Led still wouldn't toggle. The approach was to configure USART to be able to connect the microcontroller with TeraTerm so that the user can see if the algorithm worked correctly. But because of the fact that the XMC4500 was only recognized by the Dave application and not by the PC itself, there was no COM-Port found by TeraTerm. Therefore the final step was to set one of the other Leds as the output and to let the Led blink at the start and turn it off after the values matched by setting the 'Initial Output Level' of the Digital I/O pin to high.
ECC & SHA: There are no example codes distributed from Infineon for the ECC and SHA algorithms, but a few C example codes can be found on the internet. The example codes that were tested for these projects can be found on the 'References' part of this aritcle. There were error messages on all of these example codes. Almost all the time the problem was the included library. Either there were some files missing or the files coulnd't be found on that path. Another problem was that the code was not compatible with the Dave ™ 4 interface. The example codes were modified to try to solve these error messages. Either the paths of the files were changed or new library files were added. But with each modification, new error messages popped up. For this project especially the Optiga Trust X Framework code on Github seemed to be a good choice for cryptographical algorithms for Dave ™ 4. But, again, the problem was to integrate the two branches of the code, develop & master, so that the library files were complete. But even though the paths to the files were changed in the code or/and the location of these files were changed, the error messages couldn't still be resolved. There are probably other underlying problems for these errors.
Conclusion
Unpredictable Problems with Dave ™ 4: There is barely any documentation on how to use Dave ™ 4 or solutions to problems on writing code or handling error messages, not even on the Infineon webpage. The example codes just explained how to get the code running but they didn't say what the application is really supposed to do, the user doesn't really know what the input & the output should be or what to do in case of an error. Also the support from Infineon was not very helpful in this case. The only thing provided by Infineon was the DAVE IDE and some Code Examples. The next thing is the huge amount of effort that must be taken when simply installing a test program on the kit. The IDE must be installed manually as well as the drivers and the debugger does still not work. This is frustrating when thinking about to implement a cryptographic functions on the kit.
Problems with Arduino: On the official "Optiga Trust E Evaluation Kit" Website is a link to a GitHub Repo with Arduino Code examples. Unfortunately you can not use these examples because the board is not detected in the Arduino IDE. Also after installing the requires drivers the board ist still not detected.
To sum this up: the board has a poor compatibility to other devices. For some reason you can only connect the board to a x64-based Windows-machine. Also the DAVE IDE does only exist for Windows. The next problem are the drivers. Infineon requests the user to install external J-Link drivers to run the debugger but also with the installed drivers the debugger does not work. This makes it nearly impossible to deploy any security related applications with the Optiga Trust E Evaluation Kit. Overall it's very hard to use the board and his functions.
Courses
- Einführendes_Wahlfachprojekt (2019)
References
- Overview of XMC-Microcontrollers & Software:
- Sample Code AES:
https://www.infineon.com/cms/en/product/promopages/aim-mc/dave_downloads.html
- Sample Code ECDH & SHA:
- Small sample Code ECDH: