OWASP Juice Shop
At first glance, the OWASP Juice Shop looks like an inconspicuous online shop for fruit juices. In 2014 Björn Kimminich designed the latest and most privileged vulnerable web service [[1]] from OWASP. Two years after its foundation, Juice Shop was submitted and accepted as an OWASP tool project In a short time, Juice Shop generate a large community. The application is an intentionally insecure Web Service, and it look like an normal online shop. It is used to improve and test your hacking skills to avoid possible security lacks. Security enthusiastic can test and simulate different vulnerabilities in a safe environment without causing major damage to the network. Here the application includes vulnerabilities of the entire OWASP Top Ten, but also many other Vulnerabilities are found in this tool. There is enough documentation and further material on the official homepage to get a bigger overview.[[2]]
Architecture:
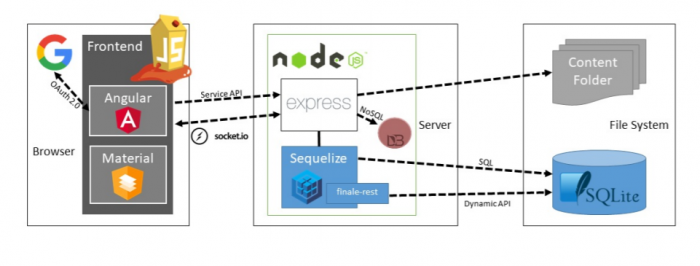
OWASP Juice Shop is a pure web application, which is implemented in JavaScript and TypeScript. In the frontend, Angular Framework is used to create a Single Page Application. The layout of the user interface is the implementation of Google's material design using Angular Material Components. In order to achieve responsiveness, the Angular Flex layout is used. All symbols which were used are from the Font Awesome library. Javascript is also used as a programming language in the backend. An Express Application is hosted on a Node.js server and provides the client-side code to the browser. The client is also provided with the required backend functionality via a RESTful API. SQLite was selected as the database. Sequelize and Finale-Rest are used as abstraction levels from the database. A MarsDB is part of the OWASP Juice Shops as additional data storage. It is a JavaScript derivative of the popular MongoDB NoSQL database and compatible with most query and change operations. Push notifications that appear when a challenge is successfully hacked are implemented via a WebSocket Protocol. The application also offers users a comfortable way of registration via OAuth 2.0. This give users the possibility to sign in using their Google accounts.
Installation
For a successful installation, the following steps must be observed:
- Node.js must be installed on the device. Then you can download the application from the official Git repository from OWASP (https://github.com/bkimminich/juice-shop). There you will also find a detailed instructions and further information.
- The downloaded file will be extracted to any path.
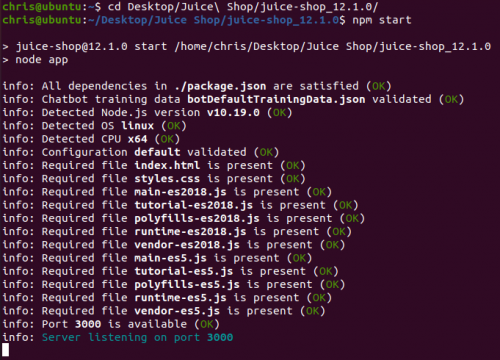
- To start the Juice Shop, open the terminal and switch to the path where you extracted the file. Then you start the program with the command "npm start"
- Then you can see which port is open, and open any browser and enter “localhost: [port]“
Example
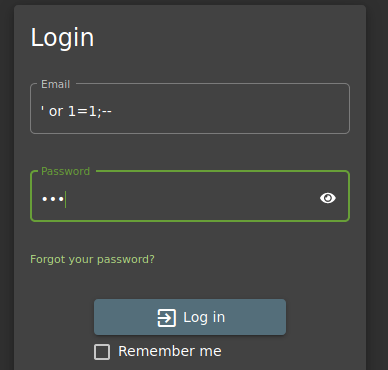
In this example an attempt is made to log in to the website without having any credential. So, here we are using a SQL command instead of an email and a randomly selected password should suffice in this case. You can log in as an administrator with the following query because the result is always ‘True’ and the administrator appears to be the first in the selection list.
- 'or 1 = 1; --
It is even possible to log in as a different user, for example as Jim or Bender. If you have successfully completed these challenges, it will lead to displayed on the page.
- 'or 1 = 1 and email not like ('% admin% '); --
- 'or 1 = 1 and email like ('% bender% '); --