OWASP Mutillidae
OWASP Mutillidae is a "Vulnerable Web Application" (see also: Unsecure Webservices: bWAPP vs. JuiceShop) that allows users to test Exploits in a legal manner inside a insulated Sandbox Environment. A big advantage of Mutillidae is the fact that it doesn't rely on "Magic Statements" - user inputs that are checked against a predefined list of accepted solutions. Instead, the way to complete challenges is completely up to the users. Mutillidae Version II has been written by Jeremy Druin and currently contains about 40 Exploits and Skill Challenges, mainly picked from the OWASP Top Ten Vulnerabilities.
Installation
In order to use Mutillidae [1], the XAMPP-Stack[2] has to be running on the user's OS. The Mutillidae source code can then be placed inside XAMPP's "htdocs" folder. This will allow the website to be reached under the specified link.
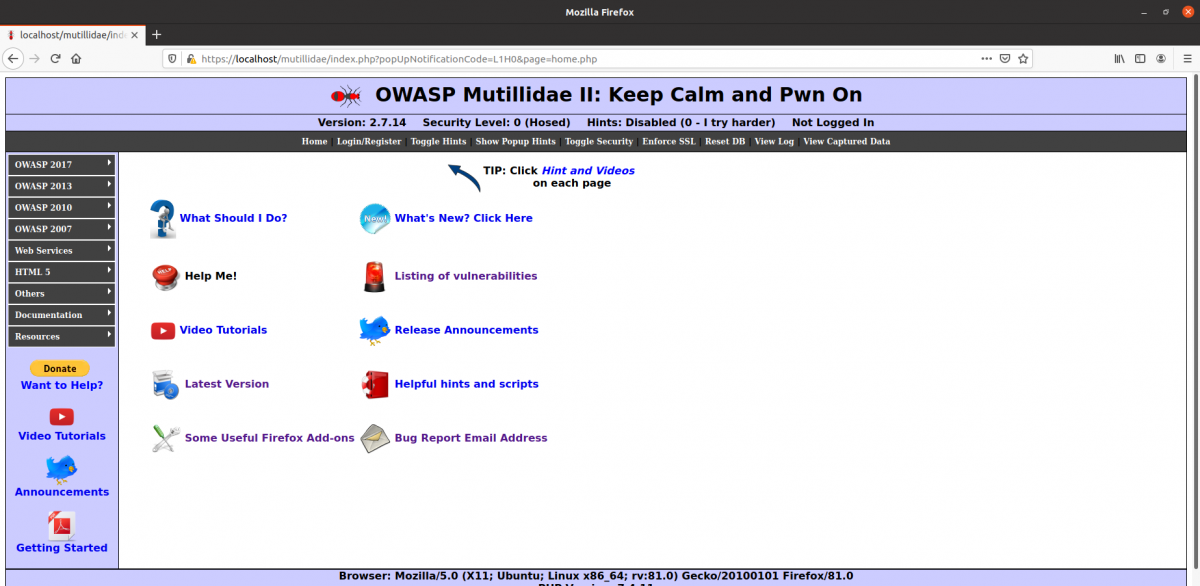
User Interface
As seen above, different features can be controlled on the landing page. The horizontal bar on top e.g. offers the possibility to hide or show hints, toggle through the three security levels or reset the backend database. On the left side, users can choose from different Vulnerabilities, sorted by the different published OWASP Vulnerabilities published throughout time. Pages will be offered, on which the specified Vulnerabilities can be tested. If hints are activated, the system will describe potential vulnerabilities presented by the different elements shown on the site.
Selected Vulnerabilities
A list of offered vulnerabilities include:
- SQL Injection (Data Extraction, Authentication Bypass)
- Various other forms of Injection (CSS, HTML, JavaScript, Buffer Overflows, XML)
- Cross-Site-Scripting (XSS)
- Various Security Missconfigurations
- Various forms of Authentication Bypass and Priviledge Escalation
Unique Features
- Actual environment instead of "Magic Statements"
- 3 Security Levels
- Embedded Help System
- A large amount of video tutorials by the creator [3]
- Fast backend reset