OWASP Mutillidae (2021)
Summary
OWASP Mutillidae is a free open source tool created for Pentesting of Web Applications. It is a "Vulnerable Web Application" that offers a Platform where the provided Exploits and Security flaws can be executed within a local environment. With over 40 different vulnerabilities and related training challenges, it provides a platform that shows the most common flaws of the last 15 years of web development. The vulnerabilities shown in the program are actual vulnerabilities within the application, so the application should only be run in a protected environment - such as a virtual machine. The current Version Mutillidae II was created by Jeremy Druin [1] (pseudonym: webpwnized), who also created the Tutorials for the Challanges and Installation Guides.
How it Operates
Every Vulnerability contained in the application is build in within a Webpage. By selecting the Exploit from a List (e.g. Authentication Bypass) a site with the corresponding explotable Webpage is loaded and ready to get "hacked". Since everything run at your local machine you can not harm anyone. The data such as "User Data" are stored in a Database which you set up when you install the Application (see Installation for more Information).
Practical example
SQL_Injection-> SQLi Extract Data
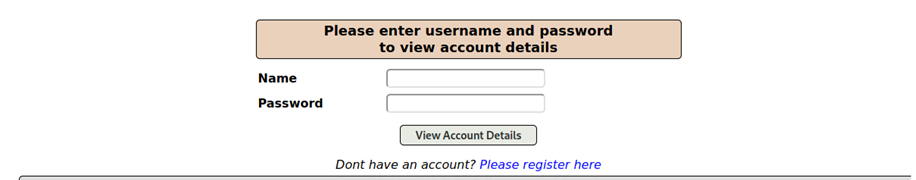
Now here is a short example how one vulnerability exploit could look like. In this case there is a query where user can request their userinformation by providing their credentials.
Normally the query should only retrun only on record when correct credentials are entered.
But this website is totally unsecure so we can easily rewrite the SQL query to give us a list of every user in the database. But how can we do this?
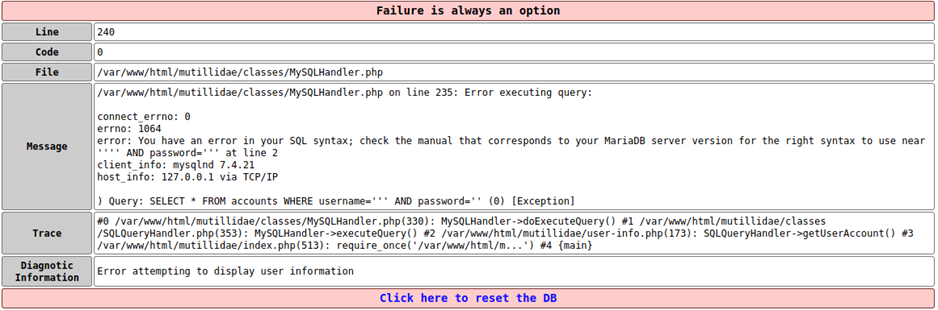
Step 1:
get an Exception by typing in invalid characters such as (', #, --)
Step 2:
Since we got an error message with the syntax how the sql statement is written we can alter the statement by simply put another statement in the form.
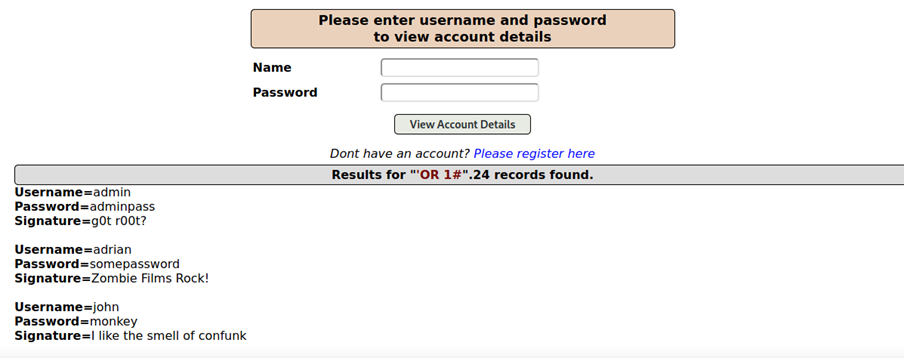
In this case i wrote ’OR 1# in the username fields to alter the query which should be now
SELECT * FROM acccounts where username= ’ ’OR 1# AND password = ’’
1 means true in SQL language and # is a comment so it ignores the password query. So our SQL String says now that it should gives as all datasets for which the condition is true which lead to following output:
Features
- over 40 vulnerabilities (OWASP Top Ten 2007, 2010, 2013 and 2017[2])
- Actually Vulnerable
- Simple Intallation and Maintaining
- User can switch between 3 security levels (no security, Client-side Security, Server-side Security)
- Used in web security courses
- Tutorials and Guides included in Application
- Updated frequently
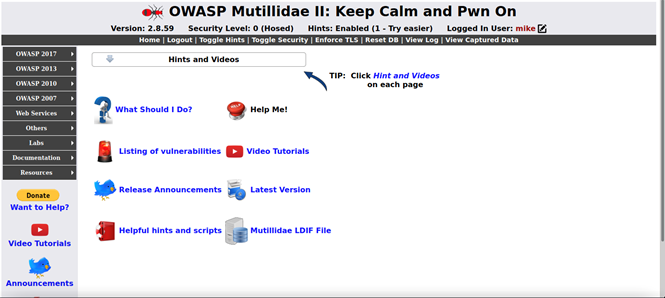
Interface
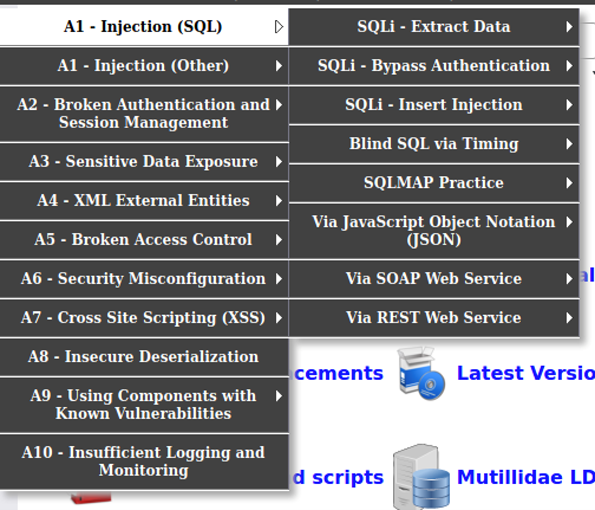
By clicking on any Item on the right dropdown menu, you can select any of the OWASP Top Ten Challanges from the last 15 years.
- Hints and Videos - leads you directly to a structured guide how the exercise could be completed.
- Toggle Security - you can choose between 3 Security levels for each exercise
- Reset DB - Clear all user Data
- Labs - Study Questions associated with the Exercises
Examples of Vulnerabilities
- SQL Injections (SQLi)[3]
- Cross-Site-Scripting [4]
- Sensitive Data Exposure
- other Injection (CSS, HTML, JavaScript)
- and many more...
Requirements
- Apache Webserver
- Database (MySQL/MariaDb)
- Packages: Sourcecode from git (https://github.com/webpwnized/mutillidae)
Installation
- Install Apache Webserver on your local Machine
- Install PHP on your local Machine
- Install a supported Database (e.g. MySQL, MariaDB)
If you have a XAMPP/LAMPP stack set up aleady, you might skip directly to installing Mutillidae. There are Videos from the creator which gives a Step-by-Step video tutorial
Installing Mutillidae
Head to the Folder where Websites are stored in Apache Webserver this could be the "htdocs" folder under XAMPP or if manually installed under a linux distribution this might be the folder "/var/www/html/"
Download the Repository from github (see #Requirements) and copy the contents of the Repository into the Webservers folder. After these steps go on your localhost webpage and make sure you can access Mutillidae Webinterface
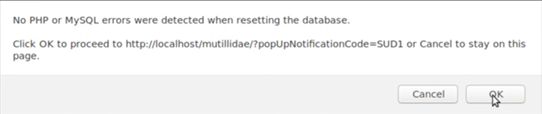
To see if the database is correctly installed press the "Reset DB" Button on the Webinterface. If you see the Message that no PHP or SQL errors were detected when resseting the database, the intallation of mutillidae succeded.
References
- https://owasp.org/www-project-top-ten/
- https://github.com/webpwnized/mutillidae
- https://www.youtube.com/c/webpwnized/featured
- https://github.com/webpwnized/mutillidae/blob/master/README-INSTALLATION.md Step-by-Step video tutorial
Internal Links