Difference between revisions of "OWASP ZAP"
| Line 29: | Line 29: | ||
==How-To== | ==How-To== | ||
===Quickstart=== | ===Quickstart=== | ||
After opening ZAP you are asked if you want to persist the session. Answer "No" to quickly skip to the Quickstart. | |||
[[File:Zap-quickstart.png|thumb|ZAP Quickstart]] | [[File:Zap-quickstart.png|thumb|ZAP Quickstart]] | ||
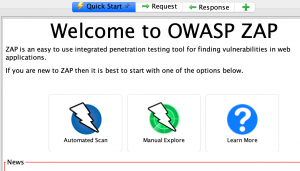
The easiest way to start using ZAP is via the Quick Start tab. Quick Start is a ZAP add-on that is included automatically when you installed ZAP. | The easiest way to start using ZAP is via the Quick Start tab. Quick Start is a ZAP add-on that is included automatically when you installed ZAP. | ||
Revision as of 12:25, 18 December 2020
Introduction
About
ZAP is short for Zed Attack Proxy. Before we delve into details as to what this means, what it is about, why it was created and what it can be used for, let us start by having a look at the principles of ZAP first for a better understanding.
The principles are:
- It is free, open source which means anyone can access and use it.
- It is also cross platform that is it works on Linux, Windows and Macs.
- It is easy to use; any user be it beginner or a professional can use it easily.
- It is easy to install; it requires Java Runtime Environment but everything else is included in standard downloads.
- It is fully internationalized, i.e., it has been translated to many other languages.
- It is fully documented, set of useful documents and helpline files are included.
- It works well with other tools, so that we can use other tools in conjunction with zap if we need to.
- It supports the use of well-regarded components.
These principles can be seen as the motivation behind ZAP, to summarise, it is designed to give everyone interested the chance to easily run security tests, at no cost, no matter their experience, the computer they use or the language they speak. OWASP (Open Web Application Security Project) is a non-profit organisation that publishes freely-available articles, and aside from tools like ZAP they also provide documentation and technologies that deal with web application security. A lot of other security publications refer to the OWASP publications, for example the OWASP Top 10 which is looking at the biggest security risks for organisations and which will be featured in its own chapter in this here paper later on. They also offer a Testing guide as well as a Development guide offering best practice information to those interested and many more interesting resources.
Description
ZAP’s focus is on testing web applications, the core idea behind it is a ”Man-in-the-Middle proxy”, that is, all web traffic between the web browser and the web application is first directed through ZAP. The data and messages can be intercepted, inspected, even modified before they are forwarded to their actual destination. There are different ways to run ZAP, it is possible to use it as a stand-alone application (Java 8+ is required) or as a daemon process.
It is also possible to run ZAP in combination with another proxy, e.g. if a company runs their web traffic through their own proxy or firewall solution first. In this case we configure our browser to connect to ZAP, and then we can configure ZAP to connect to that other proxy.
There are various Add-ons as well as an API which make it possible to be used in a variety of scenarios and also to extend ZAP further in the future. As stated in the principles, ZAP targets all skill levels, from those new to security testing who will probably start out by using automated tests, to developers, to those that run security tests for a living and can be considered specialists, making use of a variety of features including manual tests. The flexibility and extensibility (via add-ons in the ZAP marketplace that is part of the client) that ZAP provides make it a popular choice among security testers, add to that it is available for free and for pretty much every major operating system. Since we’re talking about security, to a lot of people it is also important to know what their security tools really do. ZAP is open source and code examination is possible if so desired, one can look at how certain functions are implemented and the developers are transparent about which data ZAP is ”sending home” (e.g. checks for new versions), and also how that background data can be controlled or even disabled (where possible). The ZAP community is also very open to new developers, anyone can submit bug fixes or create additional features for ZAP.
How-To
Quickstart
After opening ZAP you are asked if you want to persist the session. Answer "No" to quickly skip to the Quickstart.
The easiest way to start using ZAP is via the Quick Start tab. Quick Start is a ZAP add-on that is included automatically when you installed ZAP. To run a Quick Start Automated Scan:
- Start ZAP and click the Quick Start tab of the Workspace Window.
- Click the large Automated Scan button.
- In the URL to attack text box, enter the full URL of the web application you want to attack.
- Click the Attack button