OWASP ZAP
Introduction
About
ZAP is short for Zed Attack Proxy. Before we delve into the details as to what this means, what it is about, why it was created and what it can be used for, let us start by having a look at the principles of ZAP first for a better understanding.
The principles are:
- It is free and open source, so anyone can access and use it.
- It is cross-platform (Windows, Linux, macOS, Docker)
- It is newcomer friendly, but offers advanced and more complex functions as well.
- It is easy to install; it requires Java Runtime Environment, but everything else is included in standard downloads.
- It is fully internationalized, i.e., it has been translated to many other languages.
- It is fully documented, meaning it has a set of useful documents and helpline files are included.
- It works well with additional third-party tools. For example: Automation
- It supports the use of well-regarded components.
These principles can be seen as the motivation behind ZAP. To summarize, it is designed to give everyone interested in web security the chance to easily run security tests, without depending on paid software or advanced skills. OWASP (Open Web Application Security Project) is a non-profit organization that publishes freely-available articles and aside from tools like ZAP, they also provide documentation and technologies, that deal with web application security. Many security publications refer to the OWASP publications. An example is the OWASP Top 10, which is looking at the biggest security risks for organizations. OWASP Top 10 will be covered in more detail in another chapter. They also offer a testing guide as well as a development guide, offering best practice information to those interested, and many more interesting resources.
Description
ZAP’s focus is on testing web applications. The core idea behind it, is a ”Man-in-the-Middle proxy” that is placed between the client's browser and the web application. HTTP requests and responses can be intercepted, inspected and even modified before they are forwarded to their actual destination. There are different ways to run ZAP, it is possible to use it as a stand-alone application (Java 8+ is required) or as a daemon process.
Additionally, it is possible to run ZAP in combination with another proxy, e.g. if a company runs their web traffic through their own proxy or firewall solution first. In this case we configure our browser to connect to ZAP and then we can configure ZAP to connect to the proxy of the company.
There are various Add-ons, as well as an API, which enhance the functionality and features of ZAP. As stated in the principles, ZAP targets all skill levels. Beginning with those who are new to security testing, who are likely to start out using automated tests, to developers that run security tests for a living and which make use of a variety of features including manual tests. The flexibility and extensibility (via add-ons in the ZAP marketplace) that ZAP provides, makes it a popular choice among security testers. Since we’re talking about security, to a lot of people, it is also important to know what their security tools really can do. ZAP is open source and code examination is possible. If desired, one can look at how certain functions are implemented. The developers are transparent about which data ZAP is collecting (e.g. checks for new versions) and also how that background data can be controlled or even disabled (where possible). The ZAP community is also very open to new developers, anyone can submit bug fixes or create additional features for ZAP.
How-To
Installation
First, go to the Download section on the official website for ZAP and select the installer for your operating system.
Additionally, Java version 11 or higher must be installed. There are no additional requirements.
Test target
If you want to try out the features of ZAP and do not want to set up your own server, you can find places like Firing Range, which is a free-to-use online installation of Google's Firing Range. Alternatively, an online accessible OWASP Juice Shop instance like the official one can be used to try out and learn ZAP. Do NOT run active features of ZAP against public websites without permission, you might alter data and this kind of attack can be prosecuted!
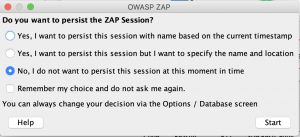
Persistent Sessions
After opening ZAP you are asked if you want to persist the session. ZAP is able to save its sessions. In other words, collected and analyzed data from web applications are saved. It enables the user to continue their analysis of the web application without the need to reach the web application. Caution is advised. The more aggressive ZAP is attacking, the more data will be collected. A few minutes of scanning can result in hundreds of Megabytes.
Modes
ZAP has different modes to choose from:
- Safe: Only allows operations, that are not considered dangerous. Dangerous meaning, manipulating requests and attacking the web application
- Protected: This is the officially recommended mode. It allows dangerous operations, but only on URLs that were put in the Scope of our target or in other words, only selected sites will be attacked.
- Standard: ZAP is allowed to do anything to the web application
- ATTACK: ZAP actively scans new nodes as soon as they are discovered.
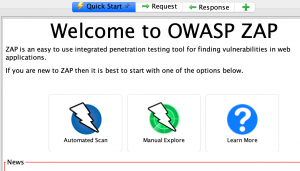
Quick Start/Automated Scan
The easiest way to start using ZAP is via the Quick Start tab. To run a Quick Start/Automated Scan:
- Start ZAP and click the Quick Start tab of the Workspace Window.
- Click the large Automated Scan button.
- In the URL to attack text box, enter the full URL of the web application you want to attack.
- Click the Attack button
Manual Scan
A manual scan can be done the following way:
- Start ZAP and click the Quick Start tab of the Workspace Window. (see above)
- Click the large Manual Explore button.
- In the URL to explore text box, enter the full URL of the web application you want to explore.
- Select the browser you would like to use
- Click the Launch Browser
Next, you will be presented with a welcome message that includes the HUD tutorial (see figure “ZAP HUD Welcome Message”)
Spider
After starting an automated scan, the Spider tab opens up in ZAP. The Spider “crawls” through the web application and tries to find every page of the web application. Optionally, a more advanced AJAX spider for AJAX-rich sites can be used.
Add-ons
There is a Marketplace for ZAP where extra Add-ons for ZAP can be found. These make it possible to extend the functionality of ZAP even further, and typically it is possible to add or remove them without restarting the ZAP application. Usually, Add-ons are assigned one of the following states:
- Release: high-quality add-on
- Beta: reasonable quality but possibly incomplete or still requires testing • Alpha: requires further development
You can reach the marketplace by clicking on the blue-red-green squares symbol in the UI, it stands for “Manage Add-ons”.
User Agent Settings
If you go to Tools → Options → Connection in the ZAP GUI you can configure the Default User Agent (as in, which browser as well as operating system) that ZAP should pretend to be when connecting to websites. You may get different responses depending on this, especially older websites did have their own configurations for Internet Explorer that were unlike those for other browsers.
API
It is possible to interact with ZAP using its powerful Application Programming Interface (API), almost every feature that the GUI offers can be accessed via API and more features are being added with future versions. It also helps not only beginners that there is an extensive documentation for the API, giving examples for Shell script, Python and Java commands to run features.
Requests to the API are via GET and POST endpoints, responses are available in a variety of formats such as JSON, HTML and HTML but also custom formats such as HAR. The content of the response formats is always the same but the developer can select the format that best fits their use case depending on what they are looking for. There are recommendations given such as using HTML for good readability in reports, JSON or XML if one is looking to quickly parse the returned result.
It is also possible to use ZAP to scan APIs and even automate the scanning process for these API scans, using the same file formats we that we use for ZAP’s own API (JSON, etc.). However, the main problem with scanning APIs is the exploration, figuring out what to target and using which methods since most of the time browsing or spidering will not lead to useful results for APIs.
Why is an API key required by default?
Since ZAP can be controlled via API, we also must protect it from malicious sites or attackers that are looking to basically remotely control our ZAP installation or make changes to it. So it was decided to make the usage of an API key mandatory to hinder these attempts.
Attack the OWASP Top 10 using ZAP
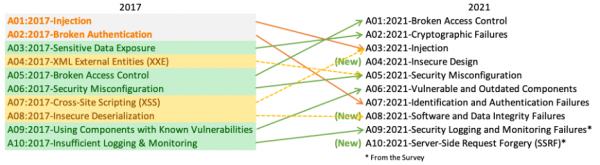
One of the many guides found at the ZAP website is about how to attack the Top 10 security threats using ZAP. The content of the following tables is taken from the Zapping the Top 10 Guide. The last OWASP Top 10 was 2017. The current OWASP Top 10 is from 2021, which has three new categories, with naming and scoping changes, and some combined vulnerabilities in the Top 10 for 2021. More information about the Top 10 can be found on their OWASP Top Ten Page.
Passive versus Active Scanning
Passive scanning is considered safe and legal. It is used to find vulnerabilities without modifying requests nor malicious actions. It is also run in a background thread, so it does not negatively affect the performance when exploring an application.
Active Scanning is considered malicious and should only be used when verbal or written permission of the owner of the target web application is acquired. Active Scan is running by default in Standard and Attack Mode.
Limitations of a standard passive scan are that pages that require a login can not be accessed by ZAP, since the authentication will not be handled by ZAP. It is, however, possible to configure the functionality to authenticate. Another limitation is that the sequence in which a passive scan explores the target is pretty much uncontrollable. But ZAP offers a solution for almost every limitation, and that means there are many extra features in ZAP for exploring and attacking other than the passive scan. For exploring a site, we already mentioned spidering as a viable option, but we need to keep in mind that they also are rather limited when it comes to filling out forms. Forms may be filled with default data or random strings instead of the required information. So it is suggested that spidering is used in combination with manual exploration, so that an actual user can, for example, fill out form data if an error message is returned.
Another recommendation for exploration is to take a look at the web application with a browser proxying through ZAP. The benefit of this method is that all requests and responses undergo a passive scan by ZAP and a site tree is built. Additionally, ZAP will record potential vulnerabilities that it finds for future reference.
Videos
A series of short videos (~10 mins each) about different ZAP features can be found both here and here.
References
- Official Documentation for ZAP
- R. S. Devi and M. M. Kumar, "Testing for Security Weakness of Web Applications using Ethical Hacking," 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184), Tirunelveli, India, 2020, pp. 354-361, doi: 10.1109/ICOEI48184.2020.9143018.[1]