Difference between revisions of "OWASP Zed Attack Proxy"
Tag: Manual revert |
|||
| Line 87: | Line 87: | ||
[[File:Threat_Modeling(option)_-_A.jpg|400px]] | [[File:Threat_Modeling(option)_-_A.jpg|400px]] | ||
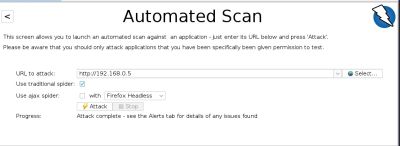
/ | //OWASP ZAP Automated Scan// | ||
[[File:Threat_Modeling(option)_-_B.jpg|400px]] | [[File:Threat_Modeling(option)_-_B.jpg|400px]] | ||
Revision as of 03:22, 7 January 2024
The Open Web Application Security Project(OWASP) is a non-profit organization aimed at improving the security of applications and services on the internet. Another important tool provided by OWASP is the ”OWASP Top 10” list. This list summarizes the ten most common security risks for web applications and is regularly updated based on data and trends in web application security. Based on the ”OWASP Top Ten,” various tools are developed to enhance security in the digital world, and one of these is OWASP ZAP.
Getting to Know OWASP ZAP
OWASP Zed Attack Proxy (ZAP) is a comprehensive, open-source penetration testing tool developed by The Software Security Project (SSP) under OWASP. Specifically designed for assessing web application security, it functions as a “Manipulator-in-the-middle proxy, intercepting and modifying messages between the tester’s browser and the application. ZAP is versatile and user-friendly, catering to both security novices and specialists. It is compatible with major operating systems and Docker, offering both manual and automated testing capabilities to identify and report vulnerabilities in web applications. The tool features a detailed desktop UI, a powerful API, command-line functionality, and is extensible through various add-ons available in the ZAP Marketplace. Emphasizing responsible use, ZAP simulates real attacks, underscoring the importance of using it only on applications for which the user has testing permission. Its multifunctionality, adaptability, and focus on responsible usage make ZAP a valuable asset in enhancing web application security.
Features
OWASP ZAP is a comprehensive tool in web application security, equipped with various modules to detect and analyze a wide range of vulnerabilities. With features like multiple attack modes and structured scanning, it plays a crucial role in identifying and mitigating potential threats in web applications.
Security Scanner for Web Applications: OWASP ZAP is utilized as a security scanner specifically designed for web applications. Various Modules:
It is equipped with various modules including:
- Proxy: For capturing data
- Fuzzer: For identifying vulnerabilities
- Spider: For discovering web applications
- Scanner: For conducting active and passive attacks
- Dictionary Method: To access files
Vulnerability Detection: OWASP ZAP is capable of detecting medium and low-level risks and vulnerabilities such as:
- URL rewriting
- Application error disclosure
- X Frame Options (XFO) header not set
- SQL injection
- Cross-Site Request Forgery (CSRF)
- Cookie without secure flag and HTTP only
Scanning Process: The scanning process in ZAP includes giving the Host Name/Host ID as input, carrying out the scanning to identify flaws, discovering vulnerabilities, performing risk analysis, and concluding the results. Modes of Attack: ZAP offers four modes of attack: standard mode, protected mode, attack mode, and safe mode. These modes are used to identify vulnerabilities on the web. Risk Analysis: After identifying vulnerabilities, the process of risk analysis is performed, categorizing risks into low, high, informational, and medium.
Methodology
There are various ways to analyze risks in OWASP. This is based on standard methods and is tailored to personalized security applications.
- Step 1: Pre-engagement Interactions: This phase involves establishing clear goals, scope, and legal boundaries for the security assessment or penetration test, often through contractual agreements.
- Step 2: Intelligence Gathering: The focus here is on collecting as much information as possible about the target system or organization, which could include public data or internal details.
- Step 3: Threat Modeling: In this optional step, potential threats and attack vectors are identified and assessed, helping to prioritize the focus areas for the assessment.
- Step 4: Vulnerability Analysis: This critical phase involves identifying and analyzing vulnerabilities within the system, which could be prone to exploitation.
- Step 5: Exploitation: This step involves attempting to exploit the identified vulnerabilities, demonstrating the potential impact of a breach.
- Step 6: Post Exploitation: After successful exploitation, this phase includes actions like collecting sensitive data, maintaining access, and understanding the extent of the compromise.
- Step 7: Reporting: A comprehensive report is prepared, detailing vulnerabilities, the methods used to exploit them, and the potential impact, providing valuable insights for mitigation.
- Step 8: Resolution and Re-Testing: Finally, the focus shifts to resolving the identified vulnerabilities and then re-testing to ensure that the fixes are effective and the vulnerabilities are fully addressed.
Execution
In this phase, we apply our findings in a practical manner. We conduct controlled attacks on identified vulnerabilities, such as exploiting the HTTP security flaw, within a safe testing environment. This allows us to observe the system’s response without disrupting normal operations. Every step is documented to develop effective improvement strategies.
Pre-engagement Interactions: In this phase, we define our target, which in this case is our web application at http://192.168.0.5 We plan to conduct an automatic scan to identify potential vulnerabilities. Normally, during this phase, we would also set a specific time for the scan or attack. This allows us to create an official document confirming that both teams agree to conduct the vulnerability scan. However, since this is merely a test environment of our own web application, adhering to the official process is not necessary in this instance
Intelligence Gathering: Our target is http://192.168.0.5, an internal DNS server. This server plays a key role in our network as it is responsible for mapping domain names to IP addresses. Our task in the intelligence gathering phase includes collecting details about the server configuration and identifying potential vulnerabilities to pinpoint possible security risks.
Threat Modeling(Option): In this step, we conduct a scan focused exclusively on HTTP vulnerabilities. The main issue here is that the connection via HTTP is unencrypted, which means that all traffic, including sensitive information such as login credentials and passwords, can potentially be intercepted and read. This vulnerability makes the system particularly susceptible to Man-in-the-Middle attacks.
//OWASP ZAP Automated Scan//
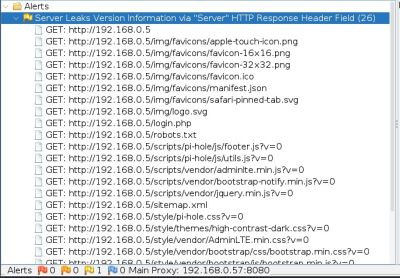
Vulnerability Scan Results