Difference between revisions of "Proxmark3: Installation"
Jostrowski (talk | contribs) (Add hf section) |
|||
| (12 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
== | == Summary == | ||
Installation of [[Proxmark3 RDV2 Kit|Proxmark3]] on macOS, Linux and Windows for RFID and NFC sniffing. | |||
<pre style="color: red"> | |||
To use the Bluetooth Module of the Proxmark3 RDV4 you need to install the https://github.com/RfidResearchGroup/proxmark3.git repository | |||
For installing on Linux please visit https://github.com/RfidResearchGroup/proxmark3/blob/master/doc/md/Installation_Instructions/Linux-Installation-Instructions.md | |||
</pre> | |||
== MacOS installation == | |||
=== Requirements === | |||
Xcode (AppStore) is a must. | |||
In addition to make the installation easier have either HomeBrew or MacPorts ready. | |||
A Tutorial for installing: | |||
A) HomeBrew: https://docs.brew.sh/Installation | |||
B) MacPorts: https://www.macports.org/install.php | |||
Because of their different architecture (HomeBrew/MacPorts), some parts of this tutorial are split into: | |||
A) Installation with HomeBrew | |||
B) Installation with MacPorts | |||
Just choose the tutorial that suits your current setup. | |||
=== Installation with HomeBrew === | |||
1. Download ("tap") the proxmark repository: | |||
brew tap proxmark/proxmark3 | |||
2. Install proxmark3: | |||
brew install proxmark3 | |||
=== Manual Installation === | |||
Download the drivers and install them. | |||
If you have MacPorts: | |||
sudo port install p7zip readline libusb libusb-compat perl5 wget qt5\\ arm-none-eabi-gcc pkgconfig | |||
If you have HomeBrew: | |||
brew tap nitsky/stm32 | |||
brew install readline libusb p7zip libusb-compat wget qt5 pkgconfig\\ arm-none-eabi-gcc | |||
Now you will need to add QT to the PKG_CONFIG_PATH so it find QT5 (replace YOUR_VERSION with your version number: | |||
export\\ PKG_CONFIG_PATH=/usr/local/Cellar/qt5/<<YOUR_VERSION>>/lib/pkgconfig/ | |||
3. And add moc_location in Qt5Core.pc file: | |||
export QT_PKG_CONFIG_QT5CORE=$(find /usr -name Qt5Core.pc 2>/dev/null) | |||
chmod 666 $QT_PKG_CONFIG_QT5CORE | |||
echo "moc_location=\${prefix}/bin/moc" >> $QT_PKG_CONFIG_QT5CORE | |||
chmod 444 $QT_PKG_CONFIG_QT5CORE | |||
4. For link creation to avoid any errors of "readline" (may happen): | |||
brew link --force readline | |||
5. Now either git clone or manually download the Proxmark project. Git clone: | |||
git clone https://github.com/Proxmark/proxmark3.git | |||
6. "cd" to the proxmark3 folder | |||
7. Now jump to the section "Connecting your Proxmark" | |||
=== Connecting your Proxmark === | |||
1. Insert your Proxmark and run | |||
system_profiler SPUSBDataType | |||
2.a) If your Proxmark is CDC you should somewhere see in the output: | |||
Product ID: 0x504d | |||
Vendor ID: 0x2d2d | |||
2.b) If your Proxmark is an HID device you should see: | |||
Product ID: 0x4b8f | |||
Vendor ID: 0x9ac4 | |||
If it is an HID Device you will need to upgrade it, then go to "Upgrading my Proxmark HID->CDC" | |||
If you have an CDC Proxmark you can jump to "Finish Line" | |||
=== Upgrading my Proxmark HID->CDC === | |||
1. Compile the bootrom, OS and software: | |||
make clean; make | |||
2. Also compile the HID compatible flash program: | |||
cd client/hid-flasher;make | |||
3. Disconnect Apple's HID driver, by installing a dummy kernel driver: | |||
sudo make install_kext | |||
sudo kextcache -system-caches | |||
4. Keep the Proxmark button pressed while reconnecting it to USB. Its yellow and red lights should light up (you can release the button after 5-ish seconds). | |||
5. Now upgrade the bootrom: | |||
./flasher -b ../../bootrom/obj/bootrom.elf | |||
6. cd ../.. | |||
7. Disconnect your proxmark and keep the button pressed while reconnecting to USB. | |||
8. While keeping the button pressed run to get the device name: | |||
ls /dev/cu* | |||
You should find a name like "/dev/cu.usbmodem####" (#### represents a number). | |||
9. While still KEEPING PRESSED the button update the FPGA and its OS: | |||
./client/flasher /dev/cu.usbmodem#### armsrc/obj/fullimage.elf | |||
10. Disconnect the proxmark and release the button. | |||
11. Now reconnect your proxmark to USB and run it: | |||
cd proxmark3/client | |||
./proxmark3 /dev/cu.usbmodem#### | |||
No need to go to "Finish Line", you are already finished with setting up the Proxmark Environment | |||
=== Finish Line === | |||
== | 1. Compile the bootrom and OS: | ||
make clean; make | |||
2. Disconnect your Proxmark from USB. Then keep the button pressed while reconnecting it back to USB. You can release the button when you see yellow/orange and red lights on your proxmark. (If you have an Elechouse v2 Proxmark3 or Elechouse v3 Proxmark3 Easy you do not need to press the button) | |||
3. Figure out your device name: | |||
ls /dev/cu* | |||
It should be something with /dev/cu.usbmodem#### (#### represents a number). | |||
4. After you have found your device run the program: | |||
cd proxmark3/client | |||
./proxmark3 /dev/cu.usbmodem#### | |||
== Linux installation == | |||
=== Requirements === | |||
* Operating system: Ubuntu 16.04 trusty amd64 | |||
=== Step 1 Compile resources:=== | |||
1. download and install some needed packages and libs | |||
sudo apt-get install p7zip git build-essential libreadline5 libreadline-dev libusb-0.1-4 libusb-dev libqt4-dev perl pkg-config wget libncurses5-dev gcc-arm-none-eabi libstdc++-arm-none-eabi-newlib libpcsclite-dev | |||
2. clone proxmark3 git repository | |||
git clone https://github.com/proxmark/proxmark3.git | |||
3. enter repo | |||
cd proxmark3 | |||
4. get newest version | |||
git pull | |||
5. Install the blacklist rules | |||
sudo cp -rf driver/77-mm-usb-device-blacklist.rules /etc/udev/rules.d/77-mm-usb-device-blacklist.rules | |||
sudo udevadm control --reload-rules | |||
6. add current user to group | |||
sudo adduser $USER dialout | |||
7. log out and log into your account | |||
8. compile proxmark3 | |||
make clean && make all | |||
=== Step 2 Identify proxmark3 device === | |||
dmesg | grep -i usb | |||
[ 9704.503904] usb 1-3: Manufacturer: proxmark.org | |||
[ 9704.539638] cdc_acm 1-3:1.0: ttyACM0: USB ACM device | |||
=== Step 3 Flash the firmware of the proxmark === | |||
!!! Do '''NOT''' press enter during the flashing process !!! | |||
./client/flasher /dev/ttyACM0 -b bootrom/obj/bootrom.elf armsrc/obj/fullimage.elf | |||
=== | === Step 4 Start the proxmark3 client === | ||
./client/proxmark3 /dev/ttyACM0 | |||
== Windows installation == | |||
=== Requirements === | |||
The tested Version for Windows was Windows 10, therefore the requirements for successfully completing our installation guide are: | |||
* Windows 10 | |||
* [https://git-scm.com/download/win Git for Windows] | |||
=== | === Installation === | ||
In order to be able to connect to your Proxmark3 under Windows you need to emulate a Linux environment which is done through a tool called ProxSpace. | |||
1. First you need to download the download the ProxSpace Repository through git. | |||
'''Caution!''' Your current working directory should contain no whitespaces! | |||
git clone https://github.com/Gator96100/ProxSpace.git | |||
2. Inside your ProxSpace Folder you should find "runme.bat". Start it. | |||
3. This will create and install all necessary packets and folders. After you should see the pm3-console. | |||
4. From this console you should change the directory to ProxSpace and download the Proxmark3 Repository: | |||
git clone https://github.com/Proxmark/proxmark3.git | |||
5. After this process is complete, cd to the proxmark3 directory: | |||
cd proxmark3 | |||
6. Compile the proxmark3 project: | |||
make clean && make all | |||
7. Install the proxmark3 driver | |||
==== Windows 10 ==== | |||
Since this driver is not officially signed by a trusted authority the installation is a bit tricky. You first have to start Windows in save-mode. This is done easiest, when pressing the shift-key while restarting your PC. On reboot you choose Startup-Settings followed by #7 Disable driver signature enforcement. | |||
After the computer restarted you connect the proxmark3 and go to the device manager, right click on the non-identified device (which is the proxmark3) and go to the settings. Click on update driver and search locally for the proxmark3.inf. If you have trouble getting the proxmark3 driver to work, please visit this [[https://store.ryscc.com/blogs/news/how-to-install-a-proxmark3-driver-on-windows-10 picture-guided tutorial]] | |||
After, the installation should be complete and you can safely restart your PC to normal mode again. From there start the runme.bat and the pm3-console should appear. | |||
==== Windows 7 ==== | |||
[[File:Win7-disable-driversignature.png|520px|right]] | |||
* Start command prompt (cmd.exe) as '''administrator''' and execute: | |||
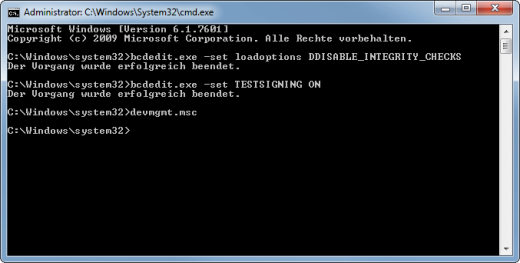
bcdedit.exe -set loadoptions DDISABLE_INTEGRITY_CHECKS | |||
bcdedit.exe -set TESTSIGNING ON | |||
* Open the device manager, right-click on the unknow device "proxmark3" and select "update" | |||
* Select the manual driver selection, and within your ''ProxSpace'' folder select the ''msys2\proxmark3\driver'' subfolder | |||
After the successful driver setup you may want to disable testsigning again, and restart windows | |||
bcdedit.exe -set TESTSIGNING OFF | |||
=== Update your Proxmark3 === | |||
To update the firmware of your Proxmark3 to the latest version, open cmd and type in (with x standing for the right number of your COM port, e.g. COM2): | |||
./proxmark/client/flasher COMx -b /bootrom/obj/bootrom.elf | |||
./proxmark/client/flasher COMX ./armsrc/obj/fullimage.elf | |||
=== Connecting to your Proxmark3 === | |||
After having done all the steps above you can safely connect to your Proxmark3 through (where x again stands for the right number of your COM port, e.g. COM2): | |||
./client/proxmark3.exe COMx | |||
== Usage == | |||
For using the Proxmark3 please visit our second documentation [[Proxmark3: Useful commands]] and feel free to have a look at the [https://github.com/Proxmark/proxmark3 Proxmark Repository!] | |||
== Resources and Tutorials == | |||
= | * Client commands: https://github.com/Proxmark/proxmark3/wiki/commands | ||
* Usage example: https://www.youtube.com/watch?v=FODGYfhqb4Q | |||
* Basic tutorial for RFID usage: https://blog.kchung.co/rfid-hacking-with-the-proxmark-3/ | |||
* Advanced tutorial: https://blog.kchung.co/rfid-hacking-with-the-proxmark-3/ | |||
* Capture NFC traffic of apple pay transaction: https://salmg.net/2017/12/29/analyzing-an-apple-pay-transaction-with-proxmark3/ | |||
== Used Hardware == | |||
[[Proxmark 3]] | |||
== References == | == References == | ||
* Product page and infos: https://www.elechouse.com/elechouse/index.php?main_page=product_info&cPath=90_93&products_id=2264&zenid=kmvhiob7nq1orc4pfjtf53sbr7 | |||
* https://github.com/Proxmark/proxmark3 | * Manual: https://www.elechouse.com/elechouse/images/product/proxmark3_V2/Proxmark3%20V2%20User%20Guid.pdf | ||
* https://github.com/ | * MacOS 10.x client installation: https://github.com/Proxmark/proxmark3/wiki/MacOS | ||
* Linux 16.04 client installation: https://github.com/Proxmark/proxmark3/wiki/Ubuntu-Linux | |||
* Windows 10 client installation: https://github.com/Proxmark/proxmark3/wiki/Windows | |||
[[Category:Documentation]] | [[Category:Documentation]] | ||
[[Category:Pentesting]] | |||
Latest revision as of 18:34, 12 March 2024
Summary
Installation of Proxmark3 on macOS, Linux and Windows for RFID and NFC sniffing.
To use the Bluetooth Module of the Proxmark3 RDV4 you need to install the https://github.com/RfidResearchGroup/proxmark3.git repository For installing on Linux please visit https://github.com/RfidResearchGroup/proxmark3/blob/master/doc/md/Installation_Instructions/Linux-Installation-Instructions.md
MacOS installation
Requirements
Xcode (AppStore) is a must.
In addition to make the installation easier have either HomeBrew or MacPorts ready. A Tutorial for installing:
A) HomeBrew: https://docs.brew.sh/Installation B) MacPorts: https://www.macports.org/install.php
Because of their different architecture (HomeBrew/MacPorts), some parts of this tutorial are split into:
A) Installation with HomeBrew B) Installation with MacPorts
Just choose the tutorial that suits your current setup.
Installation with HomeBrew
1. Download ("tap") the proxmark repository:
brew tap proxmark/proxmark3
2. Install proxmark3:
brew install proxmark3
Manual Installation
Download the drivers and install them. If you have MacPorts:
sudo port install p7zip readline libusb libusb-compat perl5 wget qt5\\ arm-none-eabi-gcc pkgconfig
If you have HomeBrew:
brew tap nitsky/stm32 brew install readline libusb p7zip libusb-compat wget qt5 pkgconfig\\ arm-none-eabi-gcc
Now you will need to add QT to the PKG_CONFIG_PATH so it find QT5 (replace YOUR_VERSION with your version number:
export\\ PKG_CONFIG_PATH=/usr/local/Cellar/qt5/<<YOUR_VERSION>>/lib/pkgconfig/
3. And add moc_location in Qt5Core.pc file:
export QT_PKG_CONFIG_QT5CORE=$(find /usr -name Qt5Core.pc 2>/dev/null)
chmod 666 $QT_PKG_CONFIG_QT5CORE
echo "moc_location=\${prefix}/bin/moc" >> $QT_PKG_CONFIG_QT5CORE
chmod 444 $QT_PKG_CONFIG_QT5CORE
4. For link creation to avoid any errors of "readline" (may happen):
brew link --force readline
5. Now either git clone or manually download the Proxmark project. Git clone:
git clone https://github.com/Proxmark/proxmark3.git
6. "cd" to the proxmark3 folder
7. Now jump to the section "Connecting your Proxmark"
Connecting your Proxmark
1. Insert your Proxmark and run
system_profiler SPUSBDataType
2.a) If your Proxmark is CDC you should somewhere see in the output:
Product ID: 0x504d Vendor ID: 0x2d2d
2.b) If your Proxmark is an HID device you should see:
Product ID: 0x4b8f Vendor ID: 0x9ac4
If it is an HID Device you will need to upgrade it, then go to "Upgrading my Proxmark HID->CDC" If you have an CDC Proxmark you can jump to "Finish Line"
Upgrading my Proxmark HID->CDC
1. Compile the bootrom, OS and software:
make clean; make
2. Also compile the HID compatible flash program:
cd client/hid-flasher;make
3. Disconnect Apple's HID driver, by installing a dummy kernel driver:
sudo make install_kext sudo kextcache -system-caches
4. Keep the Proxmark button pressed while reconnecting it to USB. Its yellow and red lights should light up (you can release the button after 5-ish seconds).
5. Now upgrade the bootrom:
./flasher -b ../../bootrom/obj/bootrom.elf
6. cd ../..
7. Disconnect your proxmark and keep the button pressed while reconnecting to USB.
8. While keeping the button pressed run to get the device name:
ls /dev/cu*
You should find a name like "/dev/cu.usbmodem####" (#### represents a number).
9. While still KEEPING PRESSED the button update the FPGA and its OS:
./client/flasher /dev/cu.usbmodem#### armsrc/obj/fullimage.elf
10. Disconnect the proxmark and release the button.
11. Now reconnect your proxmark to USB and run it:
cd proxmark3/client ./proxmark3 /dev/cu.usbmodem####
No need to go to "Finish Line", you are already finished with setting up the Proxmark Environment
Finish Line
1. Compile the bootrom and OS:
make clean; make
2. Disconnect your Proxmark from USB. Then keep the button pressed while reconnecting it back to USB. You can release the button when you see yellow/orange and red lights on your proxmark. (If you have an Elechouse v2 Proxmark3 or Elechouse v3 Proxmark3 Easy you do not need to press the button)
3. Figure out your device name:
ls /dev/cu*
It should be something with /dev/cu.usbmodem#### (#### represents a number).
4. After you have found your device run the program:
cd proxmark3/client ./proxmark3 /dev/cu.usbmodem####
Linux installation
Requirements
- Operating system: Ubuntu 16.04 trusty amd64
Step 1 Compile resources:
1. download and install some needed packages and libs
sudo apt-get install p7zip git build-essential libreadline5 libreadline-dev libusb-0.1-4 libusb-dev libqt4-dev perl pkg-config wget libncurses5-dev gcc-arm-none-eabi libstdc++-arm-none-eabi-newlib libpcsclite-dev
2. clone proxmark3 git repository
git clone https://github.com/proxmark/proxmark3.git
3. enter repo
cd proxmark3
4. get newest version
git pull
5. Install the blacklist rules
sudo cp -rf driver/77-mm-usb-device-blacklist.rules /etc/udev/rules.d/77-mm-usb-device-blacklist.rules sudo udevadm control --reload-rules
6. add current user to group
sudo adduser $USER dialout
7. log out and log into your account
8. compile proxmark3
make clean && make all
Step 2 Identify proxmark3 device
dmesg | grep -i usb [ 9704.503904] usb 1-3: Manufacturer: proxmark.org [ 9704.539638] cdc_acm 1-3:1.0: ttyACM0: USB ACM device
Step 3 Flash the firmware of the proxmark
!!! Do NOT press enter during the flashing process !!!
./client/flasher /dev/ttyACM0 -b bootrom/obj/bootrom.elf armsrc/obj/fullimage.elf
Step 4 Start the proxmark3 client
./client/proxmark3 /dev/ttyACM0
Windows installation
Requirements
The tested Version for Windows was Windows 10, therefore the requirements for successfully completing our installation guide are:
- Windows 10
- Git for Windows
Installation
In order to be able to connect to your Proxmark3 under Windows you need to emulate a Linux environment which is done through a tool called ProxSpace.
1. First you need to download the download the ProxSpace Repository through git.
Caution! Your current working directory should contain no whitespaces!
git clone https://github.com/Gator96100/ProxSpace.git
2. Inside your ProxSpace Folder you should find "runme.bat". Start it.
3. This will create and install all necessary packets and folders. After you should see the pm3-console.
4. From this console you should change the directory to ProxSpace and download the Proxmark3 Repository:
git clone https://github.com/Proxmark/proxmark3.git
5. After this process is complete, cd to the proxmark3 directory:
cd proxmark3
6. Compile the proxmark3 project:
make clean && make all
7. Install the proxmark3 driver
Windows 10
Since this driver is not officially signed by a trusted authority the installation is a bit tricky. You first have to start Windows in save-mode. This is done easiest, when pressing the shift-key while restarting your PC. On reboot you choose Startup-Settings followed by #7 Disable driver signature enforcement. After the computer restarted you connect the proxmark3 and go to the device manager, right click on the non-identified device (which is the proxmark3) and go to the settings. Click on update driver and search locally for the proxmark3.inf. If you have trouble getting the proxmark3 driver to work, please visit this [picture-guided tutorial]
After, the installation should be complete and you can safely restart your PC to normal mode again. From there start the runme.bat and the pm3-console should appear.
Windows 7
- Start command prompt (cmd.exe) as administrator and execute:
bcdedit.exe -set loadoptions DDISABLE_INTEGRITY_CHECKS bcdedit.exe -set TESTSIGNING ON
- Open the device manager, right-click on the unknow device "proxmark3" and select "update"
- Select the manual driver selection, and within your ProxSpace folder select the msys2\proxmark3\driver subfolder
After the successful driver setup you may want to disable testsigning again, and restart windows
bcdedit.exe -set TESTSIGNING OFF
Update your Proxmark3
To update the firmware of your Proxmark3 to the latest version, open cmd and type in (with x standing for the right number of your COM port, e.g. COM2):
./proxmark/client/flasher COMx -b /bootrom/obj/bootrom.elf ./proxmark/client/flasher COMX ./armsrc/obj/fullimage.elf
Connecting to your Proxmark3
After having done all the steps above you can safely connect to your Proxmark3 through (where x again stands for the right number of your COM port, e.g. COM2):
./client/proxmark3.exe COMx
Usage
For using the Proxmark3 please visit our second documentation Proxmark3: Useful commands and feel free to have a look at the Proxmark Repository!
Resources and Tutorials
- Client commands: https://github.com/Proxmark/proxmark3/wiki/commands
- Usage example: https://www.youtube.com/watch?v=FODGYfhqb4Q
- Basic tutorial for RFID usage: https://blog.kchung.co/rfid-hacking-with-the-proxmark-3/
- Advanced tutorial: https://blog.kchung.co/rfid-hacking-with-the-proxmark-3/
- Capture NFC traffic of apple pay transaction: https://salmg.net/2017/12/29/analyzing-an-apple-pay-transaction-with-proxmark3/
Used Hardware
References
- Product page and infos: https://www.elechouse.com/elechouse/index.php?main_page=product_info&cPath=90_93&products_id=2264&zenid=kmvhiob7nq1orc4pfjtf53sbr7
- Manual: https://www.elechouse.com/elechouse/images/product/proxmark3_V2/Proxmark3%20V2%20User%20Guid.pdf
- MacOS 10.x client installation: https://github.com/Proxmark/proxmark3/wiki/MacOS
- Linux 16.04 client installation: https://github.com/Proxmark/proxmark3/wiki/Ubuntu-Linux
- Windows 10 client installation: https://github.com/Proxmark/proxmark3/wiki/Windows