Root-me
Root-me is a non-profit organization whose aim is to offer a great learning platform for ethical hacking. Together with its members, Root-me builds up a community where everyone can contribute as well as participate to the website’s development. Since it was founded in 2010 it became a platform offering the largest number and variety of content dedicated to cyber security such as ethical hacking or forensics as well as numerous exercises to train ethical hacking. Another name for ethical hacking is penetration testing which is performed using penetration testing tools.
Background
Rapid changes in the IT do not only bring more benefits into our everyday life but also cause new challenges for IT security. It is difficult nowadays to find any company that does not take advantage of the online services for better management, organization, or advertising. It thus seems necessary to protect this part of a business. Unfortunately, cyber-attacks definitely became the norm. Unauthorized individuals try to gain access to confidential data and resources by breaking into a system and get more and more creative in exploiting vulnerabilities. This led developers to undertake regular system checks in order to prevent potential attacks. This process is called a penetration test.
Penetration testing
A penetration test (PEN test) is a simulated cyber-attack against a system to identify its weak points. As a result, all present safety vulnerabilities should be detected. Those can have several different origins – human errors, bad design, or poor system configuration. Identifying the insecure areas does not only help to protect sensitive data from attackers and intruders but it also checks the strength of the organization’s security policies, the employee security awareness, and the general reaction to security events . In order to provide a platform for practical ethical hacking and information security, Root-Me was created.
Test models
Several test models are used to perform ethical hacking to ensure that the most vulnerabilities will be discovered. The most common are:
- external test: aims to exploit externally visible servers and devices, for instance the email server. Here the hacker tries to find possibilities how an attacker could gain access to the system.
- internal test: an attack done by an authorized user is simulated
- blind test: a real attack is simulated, the employees know about it and the ethical hacker gets very little knowledge about the whole system
- double blind test: where only a few people within the organization know that a penetration test is going to take place
Test types
Due to the variety of possible exploits, the defense system as well as the company as a whole has to checked for possible weak points. In the most cases it is not enough to ensure that all employees are using strong passwords. In some cases it may not be difficult to get the password or it even not is necessary to know it to enter the system in order to harm it. Therefore, it is necessary to check as many potential entry points as possible. Different test types are used for this purpose and they include:
- Network penetration test
This is all about inspecting the system by analyzing packets by e.g. performing deep packet sniffing and protocols. Network penetration testing aims to detect vulnerabilities in order to prevent violations such as Brute-Force attacks, SQL injections or Man-in-the-Middle attacks. A multitude of tools exists for this kind of testing and can principally be divided into two groups: tools which are mainly used to analyze the system and tools for actually attacking the system. Metasploit, the most used penetration testing automation framework in the world, offers both. Wireshark, Nmap or Netsparker are examples of tools for simply analyzing a network and all of them are free to use for everyone. Ettercap, an attacking tool, lets you perform a Man-in-the-Middle attack. On Root-me users can find many more freely available more or less popular tools and learn to use them by performing tasks in the provided challenges.
- Wireless penetration test
Here, the goal is to ensure WiFi security and application security. Interestingly, WiFi security options have been very weak until 2005 as hackers could break into the system of TJ Maxx, over TJ Maxx’ wireless LAN that has been secured by a rather powerless form of securing, namely Wired Equivalent Privacy (WEP). As a consequence, over 40 million customer records were stolen, which included millions of credit card numbers. However, this event led specialists to provide better solutions for protecting wireless connections.
- Social engineering
In this case the employee is exploited to gain access to desired resources. Professionals even tend to say that it is actually a human, who acts as the weakest link in the security chain. This leads to the situation, in which one does not need any programming skills or knowledge about a system in order to harm the company. A number of experiments have been done and documented showing how easy it often is to get passwords or any other informations by fooling someone. Kevin Mitnick, 'world's most famous hacker,' is the best example for social engineering. In his book, ‘Ghost in the wires’, he tells many stories about tricking people into giving him the informations he wanted.
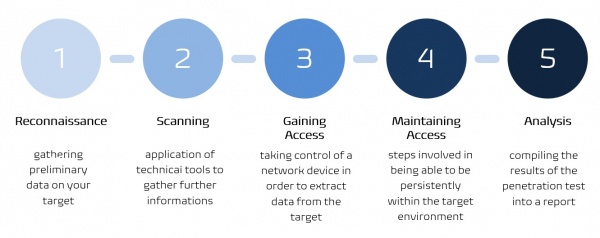
Test stages
Root-me
Root-me is an online platform offering the largest number and variety of practical content dedicated to cyber security. It follows the idea that everyone should have free access to knowledge and informations. All the users can participate in the development of the website by creating content and everyone can publish interesting news or articles. Also, everyone can create new challenges and share solutions to the already existing ones.
There is a strong focus on active participation: learning by doing. In order to achieve this goal, there are two rules that must be followed by all members. Firstly, it is not permitted to publish whole solutions for the challenges neither in the visible comment section directly on the website nor on the Internet in places like YouTube or GitHub. Secondly, it is not allowed to spoil users looking or asking for documentation on a challenge. All offered resources have to be supportive only and make it easier to find a solution instead of providing it.
One of the specialties users can find on Root-Me is the competition feeling. For every solved task points can be collected and eventually found and compared in the Ranking section with scores from other users.
How to use?
Log-in
It is necessary to log in before entering the website. The website may appear in French at first, but it can also be used in English, German, Spanish and Russian. After logging in the news section appears.
Challenges
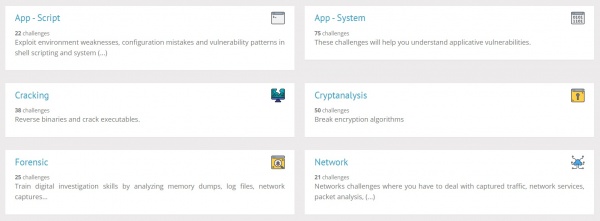
The menu is on the left. After selecting Challenges, we can see all the available categories and for each there are numerous tasks in form of challenges that we can choose. Over three hundred challenges available to learn hacking divided in following categories:
- App - Script
- App - System
- Cracking
- Cryptanalysis
- Forensic
- Network
- Programming
- Realist
- Steganography
- Web - Client
- Web - Server
As we can see on the Figure below, every category has a short description of what can be learnt there.
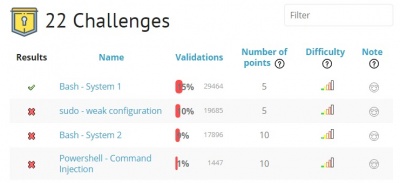
After selecting one of the category, challenges are shown as a list containing some information: a red cross or a green check mark telling if the challenge already has been successfully accomplished; the name of the challenge; the validation; number of points the user can get for the correct solution; the difficulty level; nickname of the creator; a note in form of a smiley which says how much other users liked the challenge and finally the number of available solutions. It the figure below challenges for App-Script are shown.
Choosing one of them leads us to a webpage where we directly can start the challenge.
Tools
Another important tab is the Tools tab. Here we can find tools than will help us to hit some of the challenges. Again, they are divided into categories, which include:
- Cryptography
- Forensic
- Network
- Online Tools
- Reverse Engineering
- System
- Web
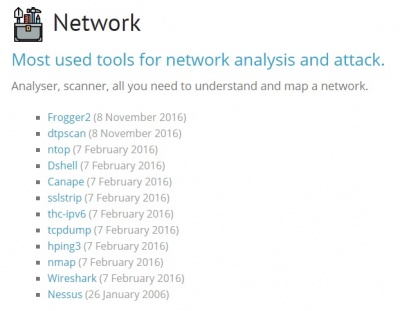
For example, when choosing Network, we get a list of network penetration testing tools like the previously mentioned Wireshark and many more. For each tool a basic core documentation is provided as well as a link, where this tool can be downloaded.
Write-up of a challenge
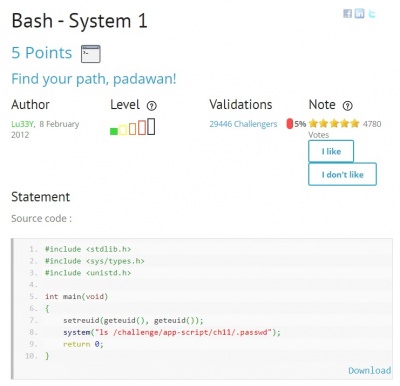
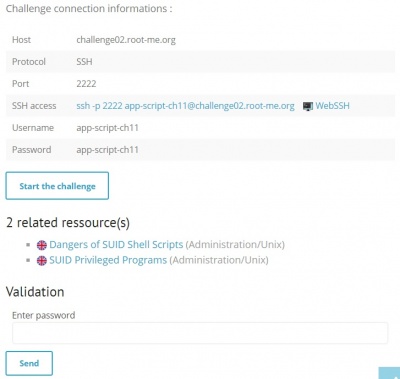
The presented challenge is the first one from the section Apt-Script, titled Bash – System 1. This category is about detecting environment weaknesses, configuration mistakes and vulnerability patterns in shell scripts. It is necessary to know some basics about the UNIX shell and skills for scripting languages. The goal is to get a password. To start one of these challenges, connection credentials are provided by Root-Me.
In the figure below we can see the provided source code. Also, some helpful resources are given.
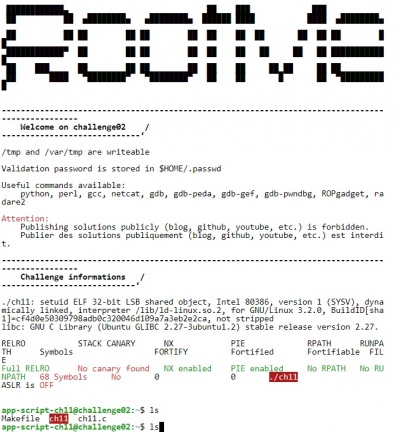
After clicking the ‘start the challenge’ button or ‘WebSSH’ link, the user is directed to a CLI, where the challenge immediately can be started. The Root-Me logo appears, followed by a reminder that publishing the solutions is forbidden.
Let's start by analyzing the source code. We know, that we want to get the password and in the code we can see that it can be found in the
/challenge/app-script/ch11/.passwdfile. The program .ch11 can be executed, however it only gives as the directory in which the password is placed, instead of the password itself.
ls-picThe problem here is the 'ls' command in the source code. It should be replaced with 'cat', so that we can actually see the content of the passwd file. We cannot, however, directly modify ch11.c since we do not have the right privileges but we can do it in another way. Currently we are in the standard user directory (~), but we can change it to the general directory
app-script-ch11@challenge02:/$When executing
ls -lawe get the list of all files and directories and we can recognize that the only directory in which we can create and modify files is
tmpHere, we are going to create a new directory, in which the whole process will take place. The name of the new directory will be
exAs already mentioned, we need to replace ls with cat, so we can simply copy the cat command from the /bin directory and paste it into /tmp/ex/ls. ‘ls’ will automatically be generated because of using the cp command. This is done by:
cp /bin/can /tmp/ex/lsNow we can go back to the standard user directory. The next step is to manipulate the PATH variable. This is the main vulnerability here. We are going to use the fact that the programming language C uses this variable for searching the command path. So instead of searching in the /bin directory for which we do not have any privileges, it searches in /tmp/ex, where we can modify files.
export PATH="/tmp/ex"At this point, after executing
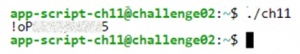
./ch11the password will be shown. Firstly, because we manipulated the PATH variable, and secondly, because instead of 'ls' 'cat' is executed.
After finishing, we can copy the password and paste it into the appropriate box on the challenge’s website. If the password is correct, we get the points and can also see solutions from other users.
Summary
Penetration testing tools are a powerful weapon which can be used in a variety of ways for different purposes. Ethical hacking is more than ever needed in our society, especially for big companies which possess vast amounts of sensitive data from their customers. It is crucial to identify weaknesses of the system to protect its data from intruders. The way to achieve this goal is to know how hackers are working and what tools they are using in order to know how to defend the system. Root-Me provides a platform for learning penetration testing for free in an effective and efficient way. Users can not only hit challenges but also every member can add his or her own input: new challenges, interesting articles or own solutions.
References
- https://www.cloudflare.com/learning/security/glossary/what-is-penetration-testing/
- https://openrepository.aut.ac.nz/handle/10292/7801
- https://ieeexplore.ieee.org/document/8673520
- https://www.root-me.org/
- https://ieeexplore.ieee.org/document/7494156
- https://www.computerweekly.com/news/2240080607/TJX-hack-the-biggest-in-history
- https://www.webroot.com/au/en/resources/tips-articles/what-is-social-engineering
- https://ieeexplore.ieee.org/document/8378035
- https://www.offensive-security.com/metasploit-unleashed/filesystem-and-libraries/
- https://www.networkworld.com/article/3296740/what-is-nmap-why-you-need-this-network-mapper.html