Difference between revisions of "RowHammer, ThrowHammer and NetHammer attacks"
| Line 37: | Line 37: | ||
[[File:non-rdma.png| | [[File:non-rdma.png|600px|]] | ||
=== NetHammer === | === NetHammer === | ||
Revision as of 10:40, 23 October 2021
Summary
In this paper, I presented and compared the different attacks about RowHammer, ThrowHammer and NetHammer but the special focus was lying on the RowHammer attack because this attack is the basis of the other attacks. Firstly, I gave an overview about the Internet, personal computers on households and how the technology developed year by year in order to bring a better feeling of understanding about todays capabilities and possibilities. Subsequently I demonstrated some details about the RAM, DRAM and also explained for what they will be used because these components are very important components of machines like computer. They are very affected by those attacks. Furthermore I described the attacks beginning by the RowHammer attack and how it works and what it uses in order to make the attack happen.
Requirements for RowHammer attack
- Have access to local computer
- Execute local code which rapidly and repeatedly reopens rows on DRAM cells
- This cause bit flips on adjacent rows
Requirements for ThrowHammer attack
- This is a remote attack
- Both attacker and victim computers have to enable RDMA on the NIC
- Attacker needs a fast network connection to victim computer
- Attacker sends packets as many as possible and as fast as possible to victim
- RDMA does write the data directly on the victim application instead on a buffer in-between
- This causes bit flips on DRAM cell rows
Requirements for NetHammer attack
- This is a remote attack
- This attack does neither need an executable code or RDMA enabled NICs
- Attacker needs a fast network connection to victim computer
- Attacker sends packets as many as possible and as fast as possible to victim, for example UDP packets with minimum packet size of 64 bytes
- It does not directly cause bit flips on the cells but instead it keeps reopening rows permanently which can cause bit flips
Description
RowHammer
The memory isolation is in general a key property of a reliable and secure computer or computing system. In normal circumstances an access to a memory address should not be that hard and it should definitely not have any side effects on data that is stored in other adjacent addresses. However, year for year the manufacturers tries to place more chips on the computer in order to gain more computing power and introduce new performance statistics to the end customer. In order to place more chips they have to make the chips smaller year for year. That means, those memory chips become much more vulnerable to disturbance. A disturbance is a phenomenon in which different memory cells interfere with each others operation. The whole problem and in the same time the key attack about this RowHammer topic is that repeatedly reading from the same memory address in DRAM could change data in adjacent memory addresses. In this addresses we talk about bits, so it could be for example that if a process A wants to access the memory address 2 several times in a row that some bits from the memory address 1 and 3 could change from one to zero or from zero to one, so it could flip. One bit change could manipulate the data that a memory address holds completely, so the data would be corrupt or would mean something completely different which is obviously not the sense of what DRAM should do or in general what the user of the computer at least expects. In specific, when a DRAM row is opened, so it is activated, and closed rapidly and repeatedly enough times within a DRAM refresh interval, one or more bits in physically adjacent DRAM rows can be flipped to the wrong value as described before. The repeating activating and closing a DRAM row is called hammering and this process as a whole is called RowHammer.
ThrowHammer
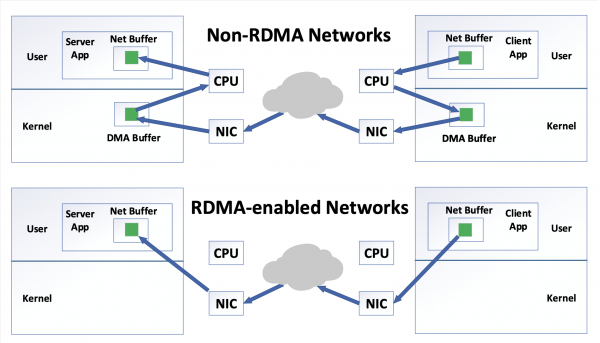
So the ThrowHammer attack is nothing else then a remotely used RowHammer attack where the attacker focuses on systems that are using RDMA. When the system wants to send a packet to another network then usually the CPU has to do some work. The CPU has to take the data from the client application and saves it to a direct memory access (DMA) buffer in the kernel space. Then the network interface card (NIC) takes this saved data from the DMA and sends it to the other network, to be more precise it will be send to the NIC of the other network. The target network then continues to copy the data to the DMA buffer and subsequently the CPU takes the data and provides it to the target client application. This is the general process of a non-RDMA system. With RDMA the CPU is not involved in this process, there is no need for it. So the client application sends directly the data to its own NIC and the NIC sends it further to the target NIC of the target network. When the target NIC gets the data it will be directly provided for the client application like showed in the figure.
NetHammer
The NetHammer attack is actually a RowHammer attack which is neither relying on any attacker controlled code on the victim computer or RDMA enabled network cards. So it does not require local code execution. It only needs a fast network connection between the attacker and the victim. This attack sends a crafted stream of small network packets to the target computer a one-location or single-sided RowHammer attack. Single-sided hammering is when accessing 8 randomly chosen memory locations simultaneously and there the probability is high that at least 2 out of 8 random memory locations will be mapped into the same out of 32 DRAM banks on DDR3. DDR3 is Double Data Rates 3 which is a SDRAM type. One-location hammering is when only accessing one single location at a high frequency. In this access pattern the attacker does not directly cause row conflicts but instead it keeps re-opening one row permanently. Each packet that is received on the target device, a set of addresses is accessed for example in a user-space application processing the contents, in the kernel driver, somewhere in between or a combination of all. So when sending packets rapidly and repeatedly, those set of addresses are hammered and therefore bit flips can occur. So to make remotely bit flips happen it is needed to send as many packets as possible, as fast as possible and in a short time frame over a the network. For example, UDP (User Datagram Protocol) packets without any specific content can be used for this attack. On those UDP packets it should be allowed to have an overall packet size of 64 B (Byte) which is the minimum packet size for an Ethernet packet. Ethernet has also a maximum frame size of 1518 B. With this it is possible to send up to 1 024 000 packets per second over a 500 Mbit per second connection.
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)