RowHammer, ThrowHammer and NetHammer attacks
Summary
In this paper, I presented and compared the different attacks about RowHammer, ThrowHammer and NetHammer but the special focus was lying on the RowHammer attack because this attack is the basis of the other attacks. Firstly, I gave an overview about the Internet, personal computers on households and how the technology developed year by year in order to bring a better feeling of understanding about todays capabilities and possibilities. Subsequently I demonstrated some details about the RAM, DRAM and also explained for what they will be used because these components are very important components of machines like computer. They are very affected by those attacks. Furthermore I described the attacks beginning by the RowHammer attack and how it works and what it uses in order to make the attack happen.
Dynamic Random Access Memory - DRAM
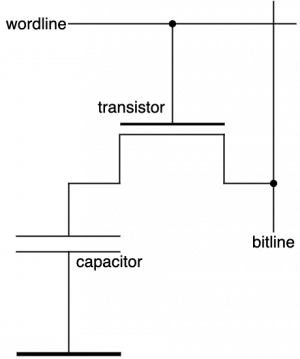
The DRAM is the easiest, slowest and cheapest memory type. Those kind of chips will be used in the todays RAM. Mostly the SDRAM type will be used. To stick on the facts from above, we will now look at how a DRAM look like. The figure shows the main structure of a DRAM memory cell component. It consist of a transistor, which works as a switch and a capacitor, which is the actual memory component. The capacitor is a component which can save an electric charge for a certain amount of time, it depends on the capacitor how long it can hold an electric charge. To fully charge or uncharge a capacitor it needs 5 * T (Tau) to either charge or uncharge it.
t = 5 ∗ T = 5 ∗ R ∗ C (2.1)
The formula to calculate the time when a capacitor will be fully charged or uncharged is showed on 2.1 where R is the resistor and C is the capacitor. In the DRAM memory cell a bit will be saved by charging the capacitor. Reading and writing happens through the transistor which functions as a switch. The transistor decides when to close the connection between capacitor and bitline and when to open it, so no information can flow to the bitline. Through the wordline the transistor can be controlled. Every gate of the transistor is connected to a wordline and each of this wordlines controls the access to the whole row. The cells of a DRAM are organized in arrays as described before. Each of those arrays are also called bank. A DRAM chip usually has 8 banks. Over time the charge will get lost and the data in the cell will also be lost. When a cell starts losing its data until it loses it completely the time in between is also called the data retention time. In order to not lose data fast and keep the data for a longer time each wordline of each row has to be accessed periodically, so in a specific interval of time, to charge the capacitors of that row through the bitlines. This process is called the "DRAM refresh". Every DRAM row needs to be refreshed within a certain frequency, which is usually 32 to 64 ms (Milliseconds) in the current DRAMs in order to ensure data integrity.
Requirements for RowHammer attack
- Have access to local computer
- Access to memory must not be cached - otherwise, the DRAM is never reached
- Memory access must be very fast (race against the refresh time)
- Memory access must be performed in a very targeted way - only specific combinations of proximate row access may cause bit flips
- This cause bit flips on adjacent rows
Requirements for ThrowHammer attack
- This is a remote attack
- Both attacker and victim computers have to enable RDMA on the NIC
- Attacker needs a fast network connection to victim computer
- Attacker sends packets as many as possible and as fast as possible to victim
- RDMA does write the data directly on the victim application instead on a buffer in-between
- This causes bit flips on DRAM cell rows
Requirements for NetHammer attack
- This is a remote attack
- This attack does neither need an executable code or RDMA enabled NICs
- Attacker needs a fast network connection to victim computer
- Attacker sends packets as many as possible and as fast as possible to victim, for example UDP packets with minimum packet size of 64 bytes
- It does not directly cause bit flips on the cells but instead it keeps reopening rows permanently which can cause bit flips
Description
RowHammer
The memory isolation is in general a key property of a reliable and secure computer or computing system. In normal circumstances an access to a memory address should not be that hard and it should definitely not have any side effects on data that is stored in other adjacent addresses. However, year for year the manufacturers tries to place more chips on the computer in order to gain more computing power and introduce new performance statistics to the end customer. In order to place more chips they have to make the chips smaller year for year. That means, those memory chips become much more vulnerable to disturbance. A disturbance is a phenomenon in which different memory cells interfere with each others operation. The whole problem and in the same time the key attack about this RowHammer topic is that repeatedly reading from the same memory address in DRAM could change data in adjacent memory addresses. In this addresses we talk about bits, so it could be for example that if a process A wants to access the memory address 2 several times in a row that some bits from the memory address 1 and 3 could change from one to zero or from zero to one, so it could flip. One bit change could manipulate the data that a memory address holds completely, so the data would be corrupt or would mean something completely different which is obviously not the sense of what DRAM should do or in general what the user of the computer at least expects. In specific, when a DRAM row is opened, so it is activated, and closed rapidly and repeatedly enough times within a DRAM refresh interval, one or more bits in physically adjacent DRAM rows can be flipped to the wrong value as described before. The repeating activating and closing a DRAM row is called hammering and this process as a whole is called RowHammer.
Possible Solutions against RowHammer attacks
Manufacturing better DRAM chips
- That means it is a must requirement for the major manufacturers to create and develop much better and secure DRAM chips then before. This includes that those chips should not be vulnerable to those easy attacks anymore.
Error correction codes
- Using strong error correction codes (ECC) would improve and help to correct errors that are coming from RowHammer attacks.
Refresh rate
- The increasing of the refresh rate for all of the memory would increase the milliseconds of the refresh time so it would be faster. The cell would get refreshed much faster. So the bits will be refreshed again and the cell has again the correct data instead of the manipulated ones.
Remapping/Retiring statically
- A statically remapping or retiring of RowHammer affected cells via a one time post-manufacturing analysis would decrease the probability of an upcoming RowHammer attack.
Remapping/Retiring dynamically
- A dynamically remapping or retiring of RowHammer affected cells during the system opera- tion would decrease the probability of an upcoming RowHammer attacks much more.
Identifying hammered rows
- Exactly identifying hammered rows during runtime and refreshing their adjacent rows. But all of those solutions are coming with performance, power or cost overheads.
Remote Direct Memory Access - RDMA
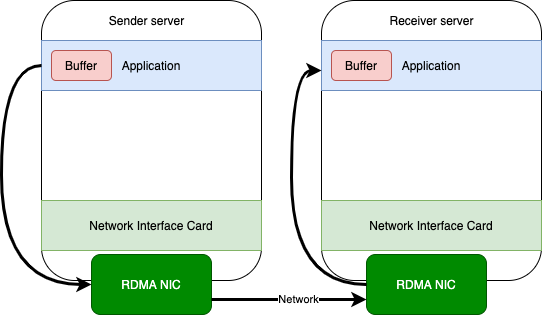
RDMA is technology that allows computers in a network to exchange data directly from the RAM without involving the CPU or the operating system of both communication partner computers. With this, it is possible to move data from and into a server by implementing a transport protocol into the hardware of the network interface card. This technology provides a function called "Zero-Copy-Networking" which enables to read data directly from a RAM of a computer and write the fetched data to the RAM of another computer in another network. RDMA provides a much faster data transferring time and a network with less latency. When both sender computer and receiver computer supports RDMA then the conversation will be executed faster than transferring the data when one of them does not support RDMA. Figure shows a conversation with an RDMA connection.
ThrowHammer
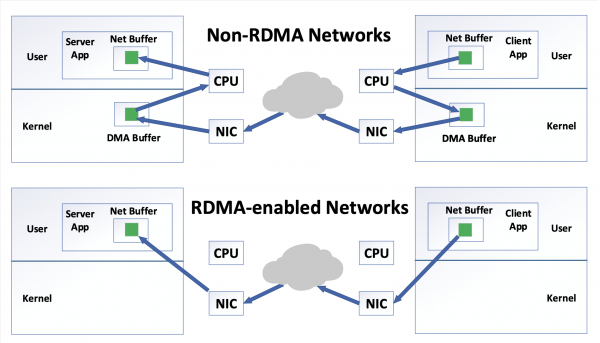
So the ThrowHammer attack is nothing else then a remotely used RowHammer attack where the attacker focuses on systems that are using RDMA. When the system wants to send a packet to another network then usually the CPU has to do some work. The CPU has to take the data from the client application and saves it to a direct memory access (DMA) buffer in the kernel space. Then the network interface card (NIC) takes this saved data from the DMA and sends it to the other network, to be more precise it will be send to the NIC of the other network. The target network then continues to copy the data to the DMA buffer and subsequently the CPU takes the data and provides it to the target client application. This is the general process of a non-RDMA system. With RDMA the CPU is not involved in this process, there is no need for it. So the client application sends directly the data to its own NIC and the NIC sends it further to the target NIC of the target network. When the target NIC gets the data it will be directly provided for the client application like showed in the figure.
In order to transfer packets efficiently ThrowHammer makes use of RDMA capabilities. Sending packets rapidly and frequently over a high speed network may cause bit flips on the target system because of RDMA.
NetHammer
The NetHammer attack is actually a RowHammer attack which is neither relying on any attacker controlled code on the victim computer or RDMA enabled network cards. So it does not require local code execution. It only needs a fast network connection between the attacker and the victim. This attack sends a crafted stream of small network packets to the target computer a one-location or single-sided RowHammer attack. Single-sided hammering is when accessing 8 randomly chosen memory locations simultaneously and there the probability is high that at least 2 out of 8 random memory locations will be mapped into the same out of 32 DRAM banks on DDR3. DDR3 is Double Data Rates 3 which is a SDRAM type. One-location hammering is when only accessing one single location at a high frequency. In this access pattern the attacker does not directly cause row conflicts but instead it keeps re-opening one row permanently. Each packet that is received on the target device, a set of addresses is accessed for example in a user-space application processing the contents, in the kernel driver, somewhere in between or a combination of all. So when sending packets rapidly and repeatedly, those set of addresses are hammered and therefore bit flips can occur. So to make remotely bit flips happen it is needed to send as many packets as possible, as fast as possible and in a short time frame over a the network. For example, UDP (User Datagram Protocol) packets without any specific content can be used for this attack. On those UDP packets it should be allowed to have an overall packet size of 64 B (Byte) which is the minimum packet size for an Ethernet packet. Ethernet has also a maximum frame size of 1518 B. With this it is possible to send up to 1 024 000 packets per second over a 500 Mbit per second connection.
Flip Feng Shui
Flip Feng Shui is a highly advanced implementation of Rowhammer capable of flipping bits in a controlled way anywhere in the software. Memory deduplication allows attackers to map a physical page onto a virtual page they own, as long as the page content is known. Rowhammer is then used to flip bits in locations of the target page. The developers of this technique managed to compromise the public RSA keys in the OpenSSH authorized_keys file, making them easier to factorize. They were then able to generate a private key and logged into the server.
Using the same techniques, they also flipped bits in the sources.list file, changing ubuntu.com to e.g. ubunvu.com (one bit flip away from the legitimate domain). The researchers registered these domains and served a malicious package update from it. By additionally manipulating the trusted.gpg file, they tricked the victim VM into verifying and installing a malicious update.
DRAMA and Rowhammer.js
Researchers from the TU Graz have published two very helpful tools which anyone can use to check if their computer is vulnerable to Rowhammer - more specifically, Rowhammer based on the cache eviction technique. The tools run on Linux Intel Ivybridge, Haswell or Skylake systems. It will only work against DDR3 DRAM.
Here is a demo of both tools provided by the authors: https://www.youtube.com/watch?v=X8-X_52rg80&ab_channel=DanielGruss
- DRAMA (https://github.com/IAIK/drama)
This tool is used to reverse-engineer the DRAM mappings - this is required so that specific rows can be targeted easily.
- git clone https://github.com/IAIK/drama
- cd drama/re
- make
- taskset 0x4 sudo ./measure -p 0.75 -s 16 (allocate 75% of DRAM for measurement, expect 16 sets) - After some time - this will output the most likely DRAM mappings
- Rowhammer.js (https://github.com/IAIK/rowhammerjs)
The "native" folder of this repository contains the source code for a simple Rowhammer attack. The code can be compiled for Haswell, Skylake and Ivybridge architectures. But first, the DRAM mappings from the DRAMA tool need to written into the source code. This way, the correct rows are hammered. If any bit flips are found, they will be output in the console.
- git clone https://github.com/IAIK/rowhammerjs
- cd rowhammerjs/native
- nano rowhammer.cc and insert the DRAM mappings for your specific architecture (see image)
- make rowhammer-ivy (for Ivybridge systems, adapt this command to your own architecture)
- ./rowhammer-ivy -d 2 -f 0 (two dimms, hammer only offset zero to increase attack speed)
Used Hardware
HP Pavilion Desktop PC with DDR3 RAM and Ivy-Bridge architecture
References
- T. Alsop, “How many people have access to a computer 2019,” Feb 2021. [Online]. Available: https://www.statista.com/statistics/748551/ worldwide-households-with-computer/
- W. b. C. Stouffer, “115 cybersecurity statistics and trends you need to know in 2021.” [Online]. Available: https://us.norton.com/ internetsecurity-emerging-threats-cyberthreat-trends-cybersecurity-threat-review.html
- A. Schaller, W. Xiong, N. A. Anagnostopoulos, M. U. Saleem, S. Gabmeyer, S. Katzen- beisser, and J. Szefer, “Intrinsic rowhammer pufs: Leveraging the rowhammer effect for improved security,” 2017 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), 2017.
- O. Mutlu and J. S. Kim, “Rowhammer: A retrospective,” IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, vol. 39, no. 8, p. 1555–1571, 2020.
- M. C.-T. Chao, H.-Y. Yang, R.-F. Huang, S.-C. Lin, and C.-Y. Chin, “Fault models for embedded-dram macros,” Proceedings of the 46th Annual Design Automation Conference on ZZZ - DAC 09, 2009.
- R.-F. Huang, H.-Y. Yang, M. C.-T. Chao, and S.-C. Lin, “Alternate hammering test for application-specific drams and an industrial case study,” Proceedings of the 49th Annual Design Automation Conference on - DAC 12, 2012.
- P. C.-F. Chia, S.-J. Wen, and S. H. Baeg, “New dram hci qualification method em- phasizing on repeated memory access,” 2010 IEEE International Integrated Reliability Workshop Final Report, 2010.
- M. Seaborn and T. Dullien., Jan 1970. [Online]. Available: https://googleprojectzero. blogspot.com/2015/03/exploiting-dram-rowhammer-bug-to-gain.html
- “throwhammer: rowhammer attacks over the network and defenses.” [Online]. Available: https://www.usenix.org/system/files/conference/atc18/atc18-tatar.pdf
- M. Lipp, M. Schwarz, L. Raab, L. Lamster, M. T. Aga, C. Maurice, and D. Gruss, “Nethammer: Inducing rowhammer faults through network requests,” 2020 IEEE Eu- ropean Symposium on Security and Privacy Workshops, 2020.