Security Databases Ecosystem
Summary
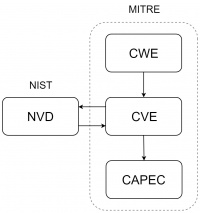
This documentation gives an introduction into the enumeration database ecosystem.
Introduction
Security databases categorize information of vulnerabilities, weaknesses or other cybersecurity related Topics. Every company had their own vulnerability database before MITRE started to build an interconnected database and only a portion of the organizations shared their information. MITRE developed in January 1999 a standardized enumeration system for vulnerabilities. The documentation of the enumeration system was written down in the paper “Towards a Common Enumeration of Vulnerabilities”. This enumeration system is seen known and used by many organizations today and set the foundation for various databases with other use cases.
Common Vulnerabilities and Exposures (CVE)
The Common Vulnerabilities and Exposures was published in September 1999 by MITRE. The initial list had 321 CVE entries. Today There are over 100.000 entries accessible for everyone. The CVE database was constructed to operate as trusted third party. Companies and individuals can send CVE entry requests which get checked by the CVE Numbering Authority. The CVE entry request than gets published on the CVE database. The CVE Entries are accessible for everyone.
A CVE entry consists out of:
- a CVE ID
- the Description
- and References to Papers and other sources which address the vulnerability
The CVE ID
CVE−YYYY −NNNN
The CVE ID is a unique identifier of the CVE. The YYYY part defines the year the CVE was assigned by a CVA or was published. The NNNN portion is a unique identifier that gets set back to zero if the YYYY part gets incremented. The restriction of the NNNN portion to 4 digits was removed in 2014 to an unlimited number of digits.
The U.S. National Vulnerability Database (NVD)
The U.S. National Vulnerability Database (NVD) is also a Vulnerability Database launched by the National Institute of Standards and Technology (NIST) in 2000. The NVD is synchronized with the CVE Database which means that CVE entries get uploaded to the NVD as soon as they get published. The Team of the NVD add enhanced information to the entries such as the affected configurations and a severity score. The severity score is calculated threw the Common Vulnerability Scoring System (CVSS).
Common Weakness Enumeration (CWE)
Common Weakness Enumeration (CWE) is also hosted by MITRE since 2008 and holds a list of common weaknesses. The difference between weaknesses and vulnerabilities is that weaknesses cause vulnerabilities. Du to the fact that weaknesses are hardware and software independent there are less of them and they are easy to categorize. The CWE ID is only four digits long and doesn’t have a year portion but they reference to parent or child weaknesses because they are organized in a tree like structure.
Common Attack Pattern Enumeration and Classification (CAPEC)
The Common Attack Pattern Enumeration and Classification (CAPEC) is a database specialized on common attack patterns. CAPEC was released by MITRE in 2007 and gets hosted by the organization until today. The purpose of CAPEC is to understand how hackers exploit weaknesses in software. The benefits of CAPEC are cybersecurity training and attacking tools for penetration testing.