Difference between revisions of "Social Engineering & Phishing Platform"
(Created page with "== Social Engineering == '''Social Engineering''' is a kind of cyber attack that influences a person to take an action that may or may not be in their best interests, according to Hadnagy. It relies on psychological manipulation with the goal of making individuals perform actions or share confidential information. === Social Engineering Attack Cycle === Social engineering is a process that requires a deep understanding of psychology, keen senses, and tons of research...") |
|||
| Line 105: | Line 105: | ||
==The Project== | ==The Project== | ||
[https://git.fh-campuswien.ac.at/c2010475112/Phishing-Platform ProjectGit] | [https://git.fh-campuswien.ac.at/c2010475112/Phishing-Platform ProjectGit] | ||
[[Category:Documentation]] | |||
Revision as of 17:22, 12 March 2024
Social Engineering
Social Engineering is a kind of cyber attack that influences a person to take an action that may or may not be in their best interests, according to Hadnagy. It relies on psychological manipulation with the goal of making individuals perform actions or share confidential information.
Social Engineering Attack Cycle
Social engineering is a process that requires a deep understanding of psychology, keen senses, and tons of research in order to gain trust and access. The cycle typically involves the following stages:
- Research
- Gathering information about the target before initiating any communication. This includes studying freely accessible websites, social media profiles, and other public sources.
- Developing a Relationship
- Applying the information from the “research” stage, to establish trust or authority with the target. The goal is to convince the target to provide information or grant access seemingly of their own free will.
- Exploiting the Connection
- Asking for the desired action or information while maintaining the target's trust to avoid suspicion.
- Utilizing Information
- Reusing gathered information or access in following attacks until the original objective is achieved.
Social Engineering Attack Methods
Social engineering encompasses various methods, including physical and psychological tactics, to gain unauthorized access.
Physical Attacks
- Tailgating
- Gaining access to restricted areas by following authorized personnel.
- Shoulder Surfing
- Secretly observing confidential information, such as passwords or PINs, by watching individuals operate devices.
- Dumpster Diving
- Sorting through discarded materials to obtain valuable information like passwords, customer numbers, or contracts.
Psychological Attacks
- Reciprocity
- Offering favours to create a sense of obligation to reciprocate.
- Obligation
- Evoking a feeling of duty or cooperation to comply with requests.
- Free Information
- Extracting seemingly harmless information through casual conversation.
- Authority
- Exploiting the perceived authority of figures to compel compliance.
- Desire to Help
- Faking distress to evoke sympathy and manipulate individuals into offering assistance.
Phishing
Phishing is a subfield of social engineering, which includes multiple strategies and methods aimed to gain personal information from targets. These attacks can be executed through various mediums such as Mail, text messages, or phone calls, and can be customized to the individual or sent out on a larger scale. In the following paragraphs multiple methods are shown.
- Mail Phishing
- Mail phishing is a well-known method, attackers impersonate legitimate sources and send emails to a wide range of Mail addresses. These often contain links or forms to fill out. These emails typically create a sense of urgency to prompt action.
- Spear Phishing
- Spear phishing involves a more targeted approach, these Mails are tailored to specific individuals or companies. Attackers make use of personal information to create an illusion of trustworthiness and legitimacy, increasing the likelihood of success.
- Whaling
- Whaling is similar to spear phishing. The significant difference is that in this method targets of a high-profile such as CEOs or public figures are the focus. It requires extensive research, to gather information for a successful spoof.
- Baiting
- Baiting attacks offer baits such as random USB sticks, email attachments, or links to invoke curiosity or offer desirable goods for free. They often use offers or a sense of urgency, like last-minute sales, to quickly needed action.
- Scareware
- Scareware exploits the tendency to act rash when someone feels threatened. By staging a threat and offering a solution to unsuspecting victims. This can be done in the form of emails, pop-ups, or SMS that lead to malware or fake websites collecting sensitive information.
Mail Phishing Exercise
The exercise "Mail Phishing" is designed to educate users about the risks about freely available personal information. Especially focusing on social media platforms. The exercise serves as a demonstration of how social engineers can exploit personal details to execute phishing attacks. Also underlining the necessity for cautious communication in work environments.
Purpose
- Raise Awareness
- By simulating a phishing scenario using social media information, the exercise aims to raise awareness about the potential threats of sharing personal details online.
- Educate about Phishing
- Through experiencing the attackers perspective, participants learn about the tactics used by Cybercriminals.
- Promote Alertness
- The exercise shows importance of exercising caution when sharing online.
Scenario
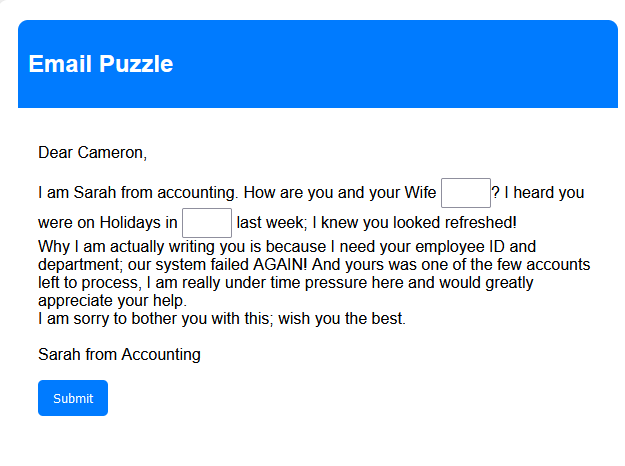
The exercises aim is to personalize a Mail to a employee, faking familiarity. It begins with Users are prompted to access publicly available social media data to gather information about the fictional individual. Upon gathering the necessary information, participants are instructed to complete an email addressed to Cameron, impersonating a colleague named Sarah from the accounting department. The email requests Cameron's employee ID and department. The Mail seems urgent thanks to faking a system failure, exploiting the familiarity implied by the shared personal details. If participants successfully fill in Cameron's employee ID t, they "win" the exercise. In the case of a successful spoof, the User gets a short text explaining the tactics behind this attack. Highlighting the potential risks associated with sharing personal information online and the importance of verifying requests for sensitive data in professional contexts.
Lessons
- Recognizing the risks associated with freely available personal information on social media.
- Understanding the tactics employed in phishing attacks and how they exploit human psychology.
- Developing critical thinking skills to discern legitimate communication from potential phishing attempts.
- Implementing best practices for safeguarding sensitive information in online interactions.
Shoulder Surfing Exercise
The Exercise "Shoulder Surfing" is designed to educate on the potential risks associated with unauthorized access to sensitive information. Furthermore, it should highlight the importance of good password hygiene. Participants engage in a simulated scenario where they attempt to uncover a coworker's password and User.
Purpose
- Highlighting the Simplicity of Shoulder Surfing
- By simulating a scenario where participants attempt to obtain a coworker's password through observation, the exercise underscores the risks associated with shoulder surfing and unauthorized access to sensitive information.
- Promote Good Password Hygiene
- Participants learn about the importance of using strong, unique passwords and avoiding the use of easily guessable information, such as details found in one's surroundings.
- Raise Awareness about Password complexity
- The exercise encourages participants to consider their password choices.
Scenario
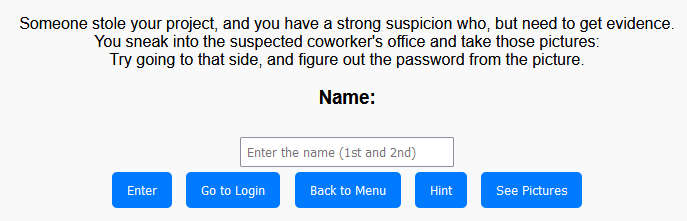
The exercise aims to figure out the identity of a coworker by “hacking” a web page. It begins with they suspect a coworker of stealing a project and need evidence to confirm their suspicions. Participants are tasked with extricating information’s based on the work environment and a shoulder surfing snapshot. Using the observed information, participants attempt to get into the coworker's given data on the site. Once participants successfully “hack” the Profile, they uncover personal information about the coworker, effectively confirming their identity and involvement in the scenario.
Learning Objectives
- Understanding the risks associated with shoulder surfing and unauthorized access to sensitive information.
- The importance of using strong, unique passwords to protect personal and professional accounts.
- Developing critical thinking skills to identify potential security vulnerabilities in password practices.
- Promoting a culture of security awareness and personal responsibility in safeguarding sensitive data.