Sphero BB-8 Robot: Bluetooth Connection Sniffing
Summary
This documentation is about the basics of Bluetooth hacking performed on the Sphero BB-8 Robot with GATT Tool and Bluetooth Connection Sniffing with the Ubertooth One. All results were obtained using GATT Tool or Bluetooth Connection Sniffing with Ubertooth and analyzed with Wireshark.
Requirements
- Linux distribution (Ubuntu 20.04.1 desktop amd64 was used for this documentation)
- Ubertooth One
- Wireshark
- hcitool
- gatttool
- bluetooth-btle
- Sphero BB-8 App
Description
Prerequisites
Ensure that the Bluetooth service is running
sudo service bluetooth status
Check if hcitool finds your Bluetooth sender
hcitool dev
Note: On some bluetooth dongles you need to enable the LE mode if you encounter problems while scanning or connecting.
btmgmt le on
Retrieve the Bluetooth Address of the victim device via hcitool
To retrieve the address of the targeted device you need to use hcitool to scan for bluetooth devices.
hcitool lescan LE Scan ... C0:BF:30:97:52:B3 (unknown) C0:BF:30:97:52:B3 BB-52B3
Connect to the target device and read its characteristics with GATT Tool
Characteristics can hint good starting points so we try to connect to the target device with GATT Tool and read its characteristics.
sudo gatttool -t random -I <Bluetooth interface> -b <BD_ADDR> connect
Depending on which bluetooth device you want to use you need to enter the name of the interface, you can get the name of your Bluetooth interfaces using hcitool.
Connecting to the Device in interactive mode
sudo gatttool -t random -I hci0 -b C0:BF:30:97:52:B3 connect
"hci0" is the Bluetooth dongle name and can differ on your device. When connected we can interact with the device. Now read the Characteristics of the target.
characteristics handle: 0x0002, char properties: 0x02, char value handle: 0x0003, uuid: 00002a00-0000-1000-8000-00805f9b34fb handle: 0x0004, char properties: 0x02, char value handle: 0x0005, uuid: 00002a01-0000-1000-8000-00805f9b34fb handle: 0x0006, char properties: 0x02, char value handle: 0x0007, uuid: 00002a04-0000-1000-8000-00805f9b34fb handle: 0x0009, char properties: 0x22, char value handle: 0x000a, uuid: 00002a05-0000-1000-8000-00805f9b34fb handle: 0x000d, char properties: 0x0c, char value handle: 0x000e, uuid: 22bb746f-2ba1-7554-2d6f-726568705327 handle: 0x000f, char properties: 0x10, char value handle: 0x0010, uuid: 22bb746f-2ba6-7554-2d6f-726568705327 handle: 0x0013, char properties: 0x0a, char value handle: 0x0014, uuid: 22bb746f-2bb1-7554-2d6f-726568705327 handle: 0x0016, char properties: 0x08, char value handle: 0x0017, uuid: 22bb746f-2bb2-7554-2d6f-726568705327 handle: 0x0019, char properties: 0x1e, char value handle: 0x001a, uuid: 22bb746f-2bb6-7554-2d6f-726568705327 handle: 0x001d, char properties: 0x0e, char value handle: 0x001e, uuid: 22bb746f-2bb7-7554-2d6f-726568705327 handle: 0x0020, char properties: 0x02, char value handle: 0x0021, uuid: 22bb746f-2bb8-7554-2d6f-726568705327 handle: 0x0023, char properties: 0x02, char value handle: 0x0024, uuid: 22bb746f-2bb9-7554-2d6f-726568705327 handle: 0x0026, char properties: 0x02, char value handle: 0x0027, uuid: 22bb746f-2bba-7554-2d6f-726568705327 handle: 0x0029, char properties: 0x0c, char value handle: 0x002a, uuid: 22bb746f-2bbd-7554-2d6f-726568705327 handle: 0x002b, char properties: 0x0a, char value handle: 0x002c, uuid: 22bb746f-2bbe-7554-2d6f-726568705327 handle: 0x002e, char properties: 0x0e, char value handle: 0x002f, uuid: 22bb746f-2bbf-7554-2d6f-726568705327 handle: 0x0031, char properties: 0x0e, char value handle: 0x0032, uuid: 22bb746f-3bba-7554-2d6f-726568705327 handle: 0x0035, char properties: 0x0a, char value handle: 0x0036, uuid: 00001013-d102-11e1-9b23-00025b00a5a5 handle: 0x0037, char properties: 0x08, char value handle: 0x0038, uuid: 00001017-d102-11e1-9b23-00025b00a5a5 handle: 0x0039, char properties: 0x12, char value handle: 0x003a, uuid: 00001014-d102-11e1-9b23-00025b00a5a5 handle: 0x003d, char properties: 0x02, char value handle: 0x003e, uuid: 00002a27-0000-1000-8000-00805f9b34fb handle: 0x003f, char properties: 0x02, char value handle: 0x0040, uuid: 00002a25-0000-1000-8000-00805f9b34fb handle: 0x0042, char properties: 0x02, char value handle: 0x0043, uuid: 00002a24-0000-1000-8000-00805f9b34fb handle: 0x0044, char properties: 0x02, char value handle: 0x0045, uuid: 00002a29-0000-1000-8000-00805f9b34fb handle: 0x0046, char properties: 0x02, char value handle: 0x0047, uuid: 00002a26-0000-1000-8000-00805f9b34fb
Analyzing the Characteristics with the GATT Tool
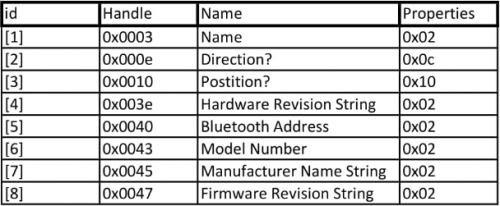
These are the Characteristics that could be analyzed.
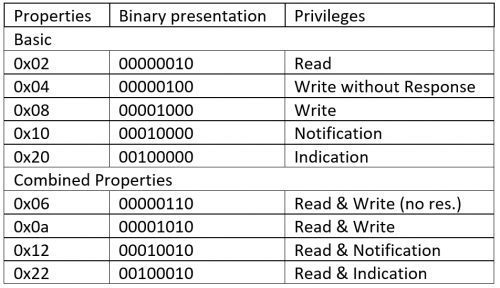
The Properties must be read as the following chart shows:
[1] Read the Device Name
Read the device name:
char-read-hnd 3 Characteristic value/descriptor: 42 42 2d 35 32 42 33
Hex to ASCII:
42 42 2d 35 32 42 33 --> BB-52B3
[2] presumably Writing the direction
When commanding the robot to move via the App, a write command gets send to the 0x000e handle. Under the circumstances I assume this is the direction to move.
char-write-cmd 0e 820958580000009d5870010000d089051b000000 Error: Characteristic Write Request failed: Attribute requires authorization before read/write
Couldn't get it to work. Requires authorization but increasing the sec-level in GAT Tool resulted in another error.
[3] presumable Getting Notified about location
Everytime the robot moves, it sends a notfication to the master. Under the circumstances I assume this is the current location.
Notification handle = 0x0010 value: ff fe 01 00 02 02 fa
[4] Read the Hardware Revision String
Read the Hardware Revision String:
char-read-hnd 3e Characteristic value/descriptor: 41 00 00 00 00 00
Hex to ASCII
41 00 00 00 00 00 --> A
[5] Read the Bluetooth Address
Read the Bluetooth Address:
char-read-hnd 40 Characteristic value/descriptor: 43 30 3a 42 46 3a 33 30 3a 39 37 3a 35 32 3a 42 33
Hex to ASCII
43 30 3a 42 46 3a 33 30 3a 39 37 3a 35 32 3a 42 33 --> C0:BF:30:97:52:B3
[6] Read the Model Number
Read the Model Number:
char-read-hnd 43 Characteristic value/descriptor: 33 30 00
Hex to ASCII
33 30 00 --> 30
[7] Read the Manufactor Name String
Read the Manufactor Name String:
char-read-hnd 45 Characteristic value/descriptor: 53 70 68 65 72 6f
Hex to ASCII
53 70 68 65 72 6f --> Sphero
[8] Read the Firmware Revision String
Read the Firmware Revision String:
char-read-hnd 47 Characteristic value/descriptor: 31 2e 34 37
Hex to ASCII
31 2e 34 37 --> 1.47
Sniffing with Wireshark
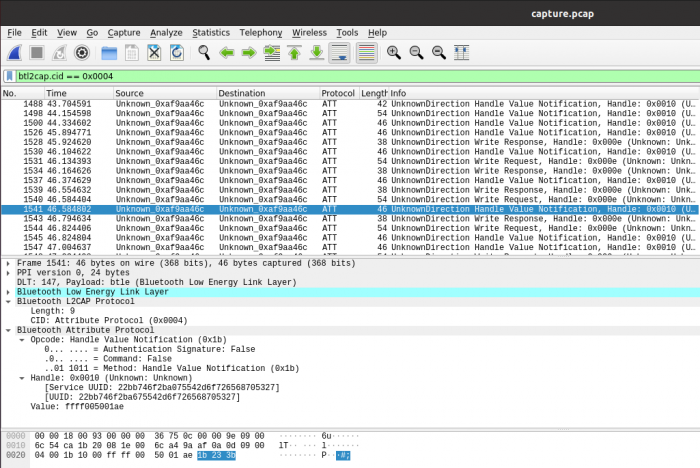
If you want to sniff BLE connection then please follow this guide: Bluetooth Sniffing with Ubertooth: A Step-by-step guide For this particullary device the ATT Protocol packets are interesting. You can filter them in Wireshark like shown in the picture below.
Used Hardware
- Ubertooth One, 2.4 GHz wireless development platform
- Sphero BB8 robot
- Bluetooth device that supports BLE