Stuxnet
Summary
Stuxnet was the first known cyber weapon to be developed and utilized in an act of strategic sabotage (attacking SCADA systems). This led to a paradigm shift from the CIA triad (Confidentiality, Integrity, Authenticity/Availability), which focuses on data security, to physical system safety. Stuxnet's origin remains unclear, although there are numerous theories about who might have been responsible for the attack. It contains complex code, targeting a specific setup. A total of seven vulnerabilities were found (four of them zero-day attacks) for propagating, hiding, taking over and executing. Further, it used two (stolen) signed certificates to make Windows believe its .dll files were legit. Unlike other worms or trojans it is quite huge and implements several programming languages. Interestingly, it also has an “expiry date” where it would stop working. If not for coincidence, it might have never been discovered.
Description
Targeted software and hardware setup
- Operating system: 32-bit Windows Operating System (2k, XP, 2003, Vista, Server 2008, 7, Server 2008 R2)
- PLC programming software: Siemens STEP7
- Hardware: S7-315-2/S7-417 programmable logic controllers with specific PROFIBUS VFD
Overview
- Over 500KBytes of code in several languages (mostly C and C++)
- Seven different ways to propagate, hide and replicate – four of them zero day exploits
- Two stolen certificates (RealTek Semiconductor and JMicron Technology) to appear legitimate
- Dropper / Worm (propagating by itself), Rootkit (by hiding itself and taking over the centrifuge controllers), Command&Control (by reporting to two servers outside and acquiring updates), SQL Injection, Man-in-the-Middle (by presenting “recorded” data to the monitors of the vaults while attacking), Process Injection
- Detailed knowledge about the targets was necessary to develop this malware
- Two different attack patterns – gas pressure and spin speed – which had very specific conditions and were not meant to destroy immediately but rather delay the uranium enrichment
- Development of Stuxnet (according to various sources) required a team of five to ten programmers working full-time for at least six months
Four zero-day attacks
Zero-day attacks target vulnerabilities that have not yet been found and therefore also not been patched, giving attackers huge advantages. Finding these vulnerabilities and developing working exploits costs a lot of time, money and human resources.
Replication
- Shortcut "LNK" Files Automatic File Execution vulnerability (CVE-2010-2568[1], MS10-046[2]): Bypassing disabled auto-run allowing auto-execution
- Print Spooler Service Impersonation vulnerability (CVE-2010-2729[3], MS10-061[4]): Installing .exe to %System% Folder that loads .dll file
Privilege escalation
- Task Scheduler Escalation of Privilege vulnerability (CVE-2010-3888[5]): Starting the .dll as a new process with administrator rights (Windows Vista / Windows 7 / Windows Server R2)
- Local Privilege Escalation vulnerability (CVE-2010-2743[6], MS10-073[7]): Starting the .dll as a new process within csrss.exe (Windows XP / Windows 2000)
Story of Stuxnet
Historical background
In April 2006 Iran announced they have successfully enriched uranium, refusing to give in to international demands to close its nuclear program. From February to November 2007 about 3000 new centrifuges were installed in Natanz, a uranium enrichment plant. In the same year the US Congress released $400 million for covert operations called "Olympic Games" against Iran´s nuclear program as Israel felt threatened by it due to their proximity to Iran. After Israel threatened physical violence, the US knew they had to find a solution.
In 2008, Israel requested assistance from the US for an airstrike on Natanz. However, US leaders were concerned that this action could escalate into a larger conflict. Given the political climate at the time, the US did not want to engage in another war. This is why they thought about sabotaging Iran with them knowing it.
Throughout 2009 the number of centrifuges at Natanz was increased to 8700. On at least one occasion, President Ahmadinejad proudly led a tour through the facility, providing videos and images of control rooms and centrifuges to the world.
Early 2010 the IAEA (International Atomic Energy Agency) inspectors that periodically visited Natanz, noticed a huge number of centrifuges being replaced. Later that year, Stuxnet was discovered and with it the cause for the failing centrifuges.
Centrifuges were important for the development of nuclear weapons because they can spin at a rapid speed to separate different isotopes of uranium.
Discovery
The first person to encounter what was later known as Stuxnet was Sergey Ulason at VirusBlokAda, Belarus in June 2010. One of their customers in Iran contacted them because their computer kept crashing.
Ulason and his colleagues discovered several interesting factors about the malware they were presented with, including the replication methods, the ability to hide in other processes and the usage of stolen certificates to legitimize to antivirus programs and Windows security.
They contacted Microsoft and RealTek to inform them about their discovery. As neither of the companies reacted, they finally posted their findings online, but it took a blog article by Brian Krebs on KrebsOnSecurity.com to gain attention.
Symantec started their own research on Stuxnet as it was to be then named. Also, Ralph Langner, a German cybersecurity specialist and expert on industrial control systems, turned his attention on Stuxnet. He found clues that it targeted a specific environment and only two Siemens PLC models.
By the time Stuxnet was discovered, the scientists had to replace over 1.000 centrifuges and the cascades were only working at 45-65 percent. By September 2010, the researchers found out that about 100.000 computers worldwide had been infected. From these machines, over 60 percent were located in Iran, which gave researchers a good idea about the original target.
Origins
Both evidence and motive indicate that the US and Israel were involved in the attack, as they have the financial means and human resources. Additionally, both countries maintain research facilities that could have been used to test the malware on the same setup as found in Natanz. Other sources even mention China and Russia. However, neither of these states admitted any involvement. Even Iran denies that the closure of Natanz happened as a consequence of a cyberattack.
Propagation
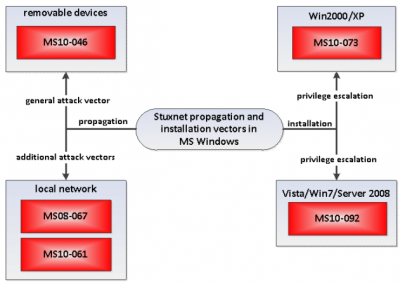
Stuxnet can spread in a variety of ways, as shown in the Figure "Stuxnet Propagation". Stuxnet spreads by infecting removable drives and copying itself over the network using a variety of means, including two Zero-Day exploits. Stuxnet also spreads by copying itself into Step 7 projects, using a technique that causes Stuxnet to run automatically when the project is opened. This section introduces the distribution routines via the network, removable drive and the Step-7 projects.
Propagation via removable media
The real goal of Stuxnet are the computers that control the centrifuges. These are referred to as PLCs (Programmable Logic Controllers) and are special computers that are used to control electronic devices or systems, such as industrial systems. The PLCs are connected to computers which control and monitor these PLCs, and usually neither are connected to the Internet. Hence, Stuxnet needed another vector to reach these computers. One way was to propagate through USB flash drives. The different versions of Stuxnet use different ways for this: newer versions use a Windows-LNK vulnerability and older versions use a vulnerability in the autorun.inf file, both of which are examined in more detail below.
LNK vulnerability (CVE-2010-2568)
Stuxnet registers a code on an infected Windows computer that copies Stuxnet to the drive when a USB drive is inserted. Interestingly, an existing copy of Stuxnet on the external drive will be removed if that drive has already infected three computers. In addition to the Stuxnet DLL and a loader for this DLL, the malware creates four .lnk files on the removable drive. These are used to run the loader when a user is viewing the drive.
To make sure that Stuxnet would reach its target, the attackers made sure to infect every version of Windows operating systems released after Windows 2000. An infected flash drive contained six malicious shortcut files. The first four files related to the different versions of operating systems. The .LNK files executed on Windows 7, the second one on Windows Vista and the last two executed on Windows XP, Windows server 2003 and Windows 2000.
Autorun.inf
An autorun.inf file is a file that causes Windows to automatically run a file on removable media when the media is inserted into the computer. Older versions of Stuxnet place an autorun.inf file on flash drives that are inserted into an infected computer. However, instead of using a separate file, it inserts the code for itself directly into the autorun file, along with valid commands to infect the computer with that code. Windows ignores the Stuxnet data portion because it ignores invalid commands in an autorun.inf file.
Propagation over the network
Stuxnet can use shared Windows folders to spread over a local network. It places a dropper file on any shares on remote computers and schedules a task to run. According to ESET, the task will be scheduled for the next day, while according to Symantec it should run two minutes after the file is shared.
Zero-Day-Exploit in print-spooler MS10-061[4]
This zero-day exploit was unique in that it had been discovered prior to its use by the creators of Stuxnet. Information along with source code had been published in a Polish security magazine in April 2009. However, the information about this vulnerability never reached Microsoft, which made it possible for Stuxnet creators to use it to spread the virus within a network. It has later been patched by Microsoft. It was also the only zero-day found in the first version of Stuxnet.
This zero-day made any system which had shared print rights in a network vulnerable. It allowed a remote user to copy files into the Windows %SYSTEM% directory, to which users have no access. There were two phases to this exploit. It first went through the injection phase, where a dropper and the files “winsta.exe” and “sysnullevent.mof” are copied into the directory. It did that by improperly impersonating a client who sent the two files to be printed to files in the directory.
The execution phase then triggered these two files. A dropper is a malicious program that is designed to spread malware to other computers. In the execution phase, the sysnullevent.mof file was used. This was a Managed Object Format or MOF for short, and it is used to create or register providers or events. This file also ran the winst.exe file, which would result in the infection of the system.
SMB vulnerability MS08-067 [8]
If a remote computer has this vulnerability, Stuxnet can send a bad path over SMB (a protocol for sharing files and other resources between computers), allowing arbitrary code to be run on the remote computer. This vulnerability allowed Stuxnet to execute code on a remote host if an affected system received a specially crafted RPC (Remote Procedure Call) request. On Microsoft Windows 2000, Windows XP and Windows Server 2000, Stuxnet could exploit this vulnerability without authentication and run arbitrary code. For Stuxnet it was possible to use this vulnerability in the crafting of a wormable exploit.
Peer-to-peer communication
Stuxnet also use a simple peer-to-peer (P2P) communication protocol to update infected hosts within a local network. It installs a RPC server and client on newly infected hosts. The RPC server listens for connections, allowing previously infected hosts to connect and check for updates. If necessary, the server can then send the latest version of Stuxnet to the requesting client.
WinCC database servers
Stuxnet scans the network for WinCC database servers. If it finds one, it uses a hard-coded password to establish a connection. Once connected, Stuxnet infects the server using a modified SQL query. [9]
Stuxnet attempts to infect all accessible shared network resources by leveraging the local user's credentials or employing the Windows Management Instrumentation (WMI). If successful, it copies itself to the resource and executes through a scheduled network job.
Propagation via Step 7 projects
Via Step7 projects, Stuxnet infects industrial control projects from Siemens SIMATIC Step7 that are opened on an infected computer. This is done by modifying DLLs (Windows Dynamic Link Library; a library with commonly used objects: code, data and resources) and an .exe file in the WinCC Simatic Manager so that they can also execute Stuxnet code. Stuxnet inserts the additional code into Step7 project directories.
Infection Process
To evade detection, Stuxnet injects its DLL file into trusted processes such as lsass.exe, winlogon.exe, or svchost.exe. It adapts its choice based on installed antivirus software to minimize risk of detection. Stuxnet then uses the two previously mentioned zero-day exploits for privilege escalation to gain administrator rights. It proceeds with the main installation, installing two driver files: a load point driver to relaunch Stuxnet after system reboots and a rootkit driver to conceal Stuxnet binaries. These drivers are signed with stolen certificates to appear legitimate. Stuxnet also injects into Windows services.exe for infecting removable drives and into Step7 processes for infecting Step7 projects. After installation, Stuxnet connects to a remote command and control (C&C) server for backdoor access and distribution of updates. If the targeted ICS software is found, it proceeds with its specific operations; otherwise, it continues propagating until it infects a suitable host.
Similar attacks
Duqu
In October 2011, Hungarian researchers discovered Duqu, which exhibited remarkable similarities to Stuxnet in terms of design, mechanisms, and internal structure. This led them to believe that the developers of Stuxnet might have been involved in creating Duqu. However, unlike Stuxnet, Duqu was not designed to manipulate physical processes in an industrial setting, but it was designed for the collection of data in cyber espionage. Duqu exploited a zero-day vulnerability in emails with a MS Word document. A parsing error in the kernel TrueType Font allowed the installation of Duqu.
Flame
The Flame attack, discovered in May 2012, was used for cyber espionage, similar to Duqu. After Flame was discovered in Europe, later also found in the United Arab Emirates as well as in Iran, the supposed main target of Stuxnet. Flame deploys mechanisms very similar to Stuxnet, though it is larger and does not target a specific industry. It also uses two zero-day exploits.
Triton
Triton was discovered in Saudi Arabia in 2017. Like Stuxnet, it was designed to target ICSs, in this case the control system of a petrochemical plant, endangering its safety. Luckily, it was discovered before it caused physical harm. It was also speculated that Triton was developed to modify safety systems to enable future attacks.
References
- Kim Zetter. Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon. Broadway Books, 2015.
- Ben Buchanan. The Hacker and the State. Harvard University Press, 2020
- Nicolas Falliere, Liam O Murchu, and Eric Chien. W32. Stuxnet dossier. White paper, Symantec Corp., Security Response, 5(6):29, 2011.
- D.E. Sanger. Confront and Conceal: Obama’s Secret Wars and Surprising Use of American Power. Crown, 2012.
- T. M. Chen and S. Abu-Nimeh. Lessons from stuxnet. Computer, 44(4):91-93, 2011
- Aleksandr Matrosov, Eugene Rodionov, David Harley, Juraj Malcho. Stuxnet Under the Microscope. Paper, ESET, 2010 accessed 02.03.2024.
- Boldizsár Bencsáth, Gábor Pék, Levente Buttyán, and Márk Félegyházi.The Cousins of Stuxnet: Duqu, Flame, and Gauss. Future Internet, 4(4):971–1003, November 2012.
- Sumayah Al-Rabiaah. The “Stuxnet” Virus of 2010 As an Example of A “APT” and Its “Recent” Variances. In 2018 21st Saudi Computer Society National Computer Conference (NCC), pages 1–5, Riyadh, IEEE, April 2018.
- Martin Giles. Triton is the world’s most murderous malware, and it’s spreading. MIT Technology Review, March 2019 accessed 04.03.2024.
- ↑ NIST. CVE-2010-2568 accessed 04.03.2024.
- ↑ Microsoft. Microsoft Security Bulletin MS10-046 - Critical accessed 03.03.2024.
- ↑ NIST. CVE-2010-2729 accessed 03.03.2024.
- ↑ 4.0 4.1 Microsoft, Microsoft Security Bulletin MS10-061 - Critical accessed 04.03.2024.
- ↑ NIST. CVE-2010-3888 accessed 03.03.2024.
- ↑ NIST. CVE-2010-2743 accessed 03.03.2024.
- ↑ Microsoft. Microsoft Security Bulletin MS10-073 - Important accessed 03.03.2024.
- ↑ Microsoft. Microsoft Security Bulletin MS08-067 - Critical accessed 02.03.2024.
- ↑ NIST. CVE-2010-2772 accessed 04.03.2024.