Difference between revisions of "UPnP vulnerabilities"
FBirnegger (talk | contribs) |
LPuehringer (talk | contribs) |
||
| Line 5: | Line 5: | ||
== UPnP == | == UPnP == | ||
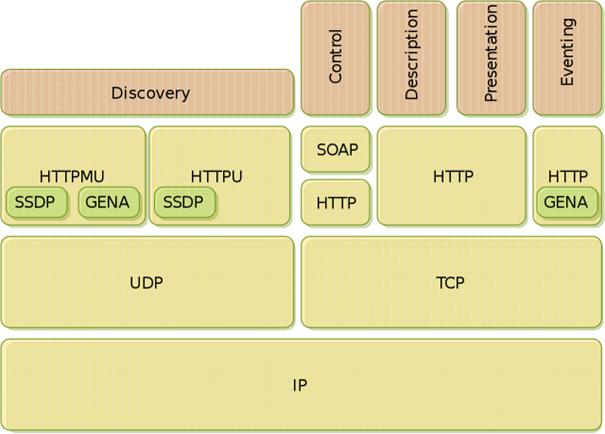
Universal Plug and Play is a protocol stack of known protocols, which is managed since 2016 by the Open Connectivity Forum, in order to automatically offer services in the network without configuration by the user. These services can range from editing port mappings on a router to switching a heater on/off. In order for a device to be a complete UPnP device it must go through a number of steps. | |||
This is done | |||
and | [[File:UPnP Protocol Stack.png]]<ref name="Protocol Stack"/> | ||
# Addressing | |||
As soon as a device is connected to the network, it searches for a DHCP server for an IP address; if none is found, it assigns itself one by means of Auto-IP. | |||
# Discovery | |||
After an address has been obtained, the device must announce its presence to the network. This is done via a advertisement, which uses HTTPMU on the address 239.255.255.250:1900, with the method NOTIFY, setting the NTS header field to ssdp:alive. In addition, devices can also search specifically for devices or services by means of a discovery request, using the method M-SEARCH. A device responds to a discovery request with an HTTP 200 message. | |||
# Description | |||
In the Discovery Response is a Location header field that contains the URL of the UPnP Device Description, which contains merchant-specific information and a list of all services and their service description URLs. The Service Description describes the actions offered by the device, its arguments, status variables and event characteristics. Documents must conform to the UPnP template language, an XML syntax defined by the UPnP Forum. | |||
# Control | |||
A control point can use the services of a UPnP device by invoking the actions with their arguments via a action invocation. This is done using SOAP, which transmits an XML SOAP envelope via a HTTP POST, which contains the action and its arguments. | |||
# Eventing | |||
UPnP uses an asynchronous publisher/subscriber model to communicate changes of status variables to control points. For this purpose GENA is used, which, like SOAP, uses HTTP and XML as underlying technologies. | |||
# Presentation | |||
This is an optional step that a vendor can implement so that the device can be controlled and managed via a web interface. | |||
== UPnP Vulnerability == | == UPnP Vulnerability == | ||
Revision as of 17:00, 8 January 2023
Summary
This document is about the general vulnerability and also about two well-known vulnerabilities of the UPnP protocol.
UPnP
Universal Plug and Play is a protocol stack of known protocols, which is managed since 2016 by the Open Connectivity Forum, in order to automatically offer services in the network without configuration by the user. These services can range from editing port mappings on a router to switching a heater on/off. In order for a device to be a complete UPnP device it must go through a number of steps.
- Addressing
As soon as a device is connected to the network, it searches for a DHCP server for an IP address; if none is found, it assigns itself one by means of Auto-IP.
- Discovery
After an address has been obtained, the device must announce its presence to the network. This is done via a advertisement, which uses HTTPMU on the address 239.255.255.250:1900, with the method NOTIFY, setting the NTS header field to ssdp:alive. In addition, devices can also search specifically for devices or services by means of a discovery request, using the method M-SEARCH. A device responds to a discovery request with an HTTP 200 message.
- Description
In the Discovery Response is a Location header field that contains the URL of the UPnP Device Description, which contains merchant-specific information and a list of all services and their service description URLs. The Service Description describes the actions offered by the device, its arguments, status variables and event characteristics. Documents must conform to the UPnP template language, an XML syntax defined by the UPnP Forum.
- Control
A control point can use the services of a UPnP device by invoking the actions with their arguments via a action invocation. This is done using SOAP, which transmits an XML SOAP envelope via a HTTP POST, which contains the action and its arguments.
- Eventing
UPnP uses an asynchronous publisher/subscriber model to communicate changes of status variables to control points. For this purpose GENA is used, which, like SOAP, uses HTTP and XML as underlying technologies.
- Presentation
This is an optional step that a vendor can implement so that the device can be controlled and managed via a web interface.
UPnP Vulnerability
There are many known vulnerabilities and security risks when talking about the UPnP Standard. On the Common Vulnerability and Exposure (CVE) website 130 different known vulnerabilities with the keyword ̈UPnPcan be found. Also, some known state institutions, like the FBI have publicly recommended to disable UPnP in general. The reason, according to the FBI Webpage, is that there are UPnP exploits which allow access to different IoT devices. Not only these known vulnerabilities make security such an important issue when talking about UPnP. The standard has also some general vulnerabilities by design. In some steps in UPnP networking there is no verification, integrity check or access control. There are also some UPnP SDKs which can be exploited.
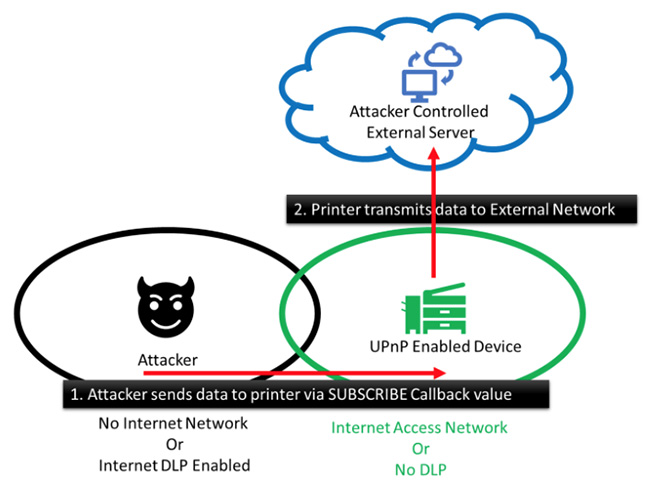
CallStranger Attack
In attack type, malicious actors send UPnP SUBSCRIBE requests to a target in which the CALLBACK header value is modified. The CALLBACK head value indicates to which machine the answer should be send to. With this vulnerability the callbacks could be directed anywhere. This attack could allow: • Scanning of internal ports • Reflected or amplified DDoS attacks • Bypassing DLP and network security to exfiltrate data The “CallStranger” Attack was fixed in April 2019
UPnP Flash Attack
This attack type is starting off with the victim opening a malicious SWF (Adobe Flash Player) file in the browser. This starts a silent attack which sends UPnP requests to the victim’s browser. These requests could open ports on the victim’s computer or change the primary DNS-Server of the victim. The UPnP Flash Attack is still not fixed and thus, it is still possible to carry out this attack.
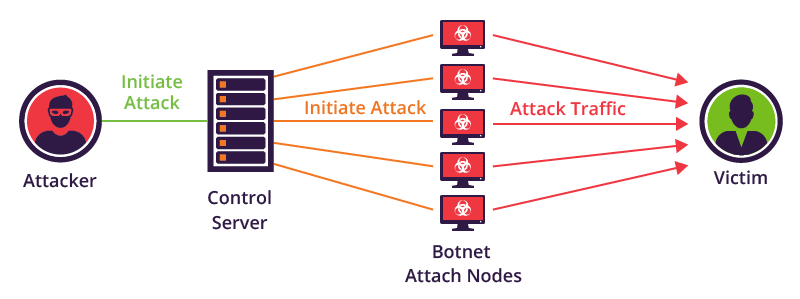
Mirai Botnet
A real-world example of a large-scale UPnP attack is the Mirai Botnet which was discovered in 2018. In this attack hundreds of thousands of routers over the internet where scanned and the attack software was searching for exposed Telnet ports which were added by UPnP. The Attackers BruteForced the default passwords of the devices and added these to the botnet. The botnet was then used to start large-scale DDoS attacks which shut down some target servers. A depiction of a simplified DDoS Attack with the Mirai Botnet can be seen in the picture below.
Courses
References
- https://www.upguard.com/blog/what-is-upnp
- https://openconnectivity.org/upnp-specs/UPnP-arch-DeviceArchitecture-v2.0-20200417.pdf
- https://github.com/yunuscadirci/CallStranger/blob/master/CallStrangerhttps://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=upnp
- https://www.fbi.gov/news/stories/cyber-tip-be-vigilant-with-your-internet-of-things-iot-devices
- https://openconnectivity.org/developer/specifications/upnp-resources/upnp/standards
- An Overview of UPnP-based IoT Security: Threats, Vulnerabilities, and Prospective Solutions; Golam Kayas, Mahmud Hossain, Jamie Payton, S. M. Riazul Islam; 2020
- https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=upnp
- [2]
- [3]
- ↑ Cite error: Invalid
<ref>tag; no text was provided for refs namedProtocol Stack - ↑ 2.0 2.1 https://www.helpnetsecurity.com/2020/06/09/cve-2020-12695/
- ↑ 3.0 3.1 https://www.imperva.com/blog/how-to-identify-a-mirai-style-ddos-attack/